![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
50 Cards in this Set
- Front
- Back
|
1. You are a desktop support technician for your company. Management has asked you to implement smart cards as a secure authentication procedure for all computers in your company, and you must install smart card readers on all company computers. You have purchased a supply of the readers from an independent vendor. The shipment comes with a CD-ROM that includes drivers and support applications for Windows 7. Although the drivers are digitally signed, the support applications are not. You must ensure that the correct drivers and applications are installed.
How should you proceed? (Each answer represents part of the solution. Choose two.) A Insert the CD-ROM and install the drivers and applications before installing the reader. B Insert the CD-ROM and install the drivers and applications after installing the smart card reader. C Select Update Driver from the reader’s properties in Device Manager to install the drivers and applications. D Attach the smart card reader to the computer before inserting the CD-ROM. E Attach the smart card reader to the computer after inserting the CD-ROM. |
B, D.
|
|
|
Joe is a landscape designer who travels extensively throughout his state working with residential and business clients to create award-winning gardens and beauty spots. He uses a Windows 7 Ultimate portable computer and needs to conserve power when traveling on the road. He has noticed that when he presses the power button on his computer, it does not fully turn off and continues to consume battery power with the result that he has occasionally lost work.
Joe would like to ensure that the computer is always completely off when he presses the power button when on battery power. What should he do? (Each answer represents a complete solution. Choose two.) A From the Windows Mobility Center, select the Power saver option. B From the Power Options Control Panel applet, select Change plan settings under the current power plan, and then select Change advanced power settings. In the Power Options dialog box, expand the Power buttons and lid category, expand Power button action, and then select Shut down. C From the Power Options Control Panel applet, select Change plan settings under the current power plan, and then select Change advanced power settings. In the Power Options dialog box, expand the Power buttons and lid category, expand Start menu power button, and then select Shut down. D From the Power Options Control Panel applet, select Choose what the power buttons do, and then select Shut down under On Battery for When I press the power button. E From the Power Options Control Panel applet, select Change plan settings under the current power plan. Then change the Put the Computer to Sleep setting under On Battery to Never. F From the Power Options Control Panel applet, select the Power saver power plan. |
B, D.
|
|
|
You have upgraded your computer to Windows 7 Home Premium. After several of your friends experienced problems with unwanted software being installed on their Windows XP Home Edition computers, you want to ensure that Internet Explorer displays a warning should a web page attempt to install software or run programs on your computer. Which of the following should you do?
A From the Safety menu in Internet Explorer, ensure that the SmartScreen Filter is enabled. B On the Privacy tab of the Internet Options dialog box, select the Block All Cookies option. C On the Privacy tab of the Internet Options dialog box, ensure that the pop-up blocker is enabled. D On the Security tab of the Internet Options dialog box, ensure that Protected mode is enabled for the Internet zone. |
D
|
|
|
Shirley is a tech support technician for Que Publishing. In recent months, many users in her company have received new Windows 7 computers. A manager named Karen needs to access a website operated by a subsidiary company named Cert Guide. She reports that she receives the message Your security settings prohibit the display of unsigned ActiveX controls when she attempts to connect.
Que Publishing has a policy requiring that users can download unsigned ActiveX controls from approved Internet websites only. Shirley verifies that Karen’s Internet Explorer settings are configured as the defaults. What should Shirley do to enable Karen to access the website operated by Cert Guide? (Each answer represents part of the solution. Choose two.) A Add the Cert Guide website to the Local intranet zone. B Add the Cert Guide website to the Trusted sites zone. C In the Security Settings–Internet Zone dialog box, enable the Download unsigned ActiveX controls option. D In the Local Intranet dialog box, clear the Include all sites that bypass the proxy server check box. E In the Local Intranet dialog box, clear the Require server verification (https:) for all sites in this zone check box. F In the Trusted Sites settings, clear the Require server verification (https:) for all sites in this zone check box. G In the Security Settings–Internet Zone dialog box, enable the Initialize and script ActiveX controls not marked as safe for scripting option. |
B,F
|
|
|
Alex has refurbished an older laptop computer by installing a new 2.5 GHz processor, a 300 GB hard disk, and 2 GB RAM. The computer has a CD-ROM drive that he has not replaced, but no DVD-ROM drive. Alex would like to install Windows 7 Home Premium on this computer but is concerned because the installation media is published on a DVD-ROM disc. Which of the following methods can he use to install Windows 7 on this computer? (Choose all that apply.)
A A network share B A portable hard drive C Windows Deployment Service (WDS) D A USB thumb drive |
A, B, D.
|
|
|
You are a help desk administrator for Billbored’s LLC. The company’s network consists of an Active Directory Domain Services (AD DS) forest with an “empty” root domain and two child domains: one that houses user and desktop accounts and another that houses proprietary resources and the majority of administrative accounts. All employees are running Windows 7 Enterprise computers and receive IP addresses from DHCP servers. The company has implemented folder redirection so that computers can be moved about the network without affecting users’ data. A new user calls the help desk because he cannot open his Documents folder. You ask him to open the Network folder, and he reports that the folder is empty. You then provide him with the instructions to run Ipconfig. He reports that the screen states:
Windows IP Configuration Ethernet adapter Local Area Connection: Media State ......................: Media disconnected Connection-specific DNS Suffix: . : IPv4 address .....................:192.168.0.88 Subnet Mask ......................:255.255.255.0 Default Gateway ..................: What should you instruct the user to do? A Click Start, type cmd in the Start menu Search field, and press Enter. At the command prompt, type netstat –e and press Enter. B Plug the cable into the wall outlet, and the other end into the Ethernet adapter of the computer, and if they are already connected then ensure the connection is not loose. When they are firmly connected, open the command prompt window and type ipconfig/release, and then follow that command with ipconfig /renew. C Plug the cable into the wall outlet, and the other end into the Ethernet adapter of the computer, and if they are already connected then ensure the connection is not loose. When they are firmly connected, access the Network and Sharing Center. Click Manage network connections. Then right-click the local area connection and choose Diagnose, and in the dialog box that appears, click Reset the network adapter Local Area Connection. D Click Start, type cmd in the Start menu Search field, and press Enter. At the command prompt, type nbtstat –RR and press Enter. E Click Start and in the Start Menu Search field, type notepad c:\windows\system32\drivers\etc\hosts; then press Enter. Add the IP address of the DHCP server to the end of the HOSTS file. |
B.
|
|
|
Abby is a graphics art designer for an advertising agency. She is using a Windows 7 Ultimate computer that contains three hard disks, two of 400 GB capacity and one of 200 GB capacity. The operating system and several design applications are installed on the 200 GB disk, which is configured as the C: drive. The applications access very large files and consume considerable disk I/O actions. She needs to configure the hard disks on her computer for optimum operation of these applications.
Which of the following actions should Abby take to accomplish this objective? (Each correct answer represents part of the solution. Choose two.) A Convert the two 400 GB disks to dynamic storage. B Convert all three disks to dynamic storage. C Create a spanned volume from the two 400 GB disks. D Create a spanned volume from all three disks. E Create a striped volume from the two 400 GB disks. F Create a striped volume from all three disks. |
A, E.
|
|
|
Peter is an office administrator and part-time technical support specialist for an insurance office that employs eight agents. The office runs a workgroup containing eight Windows 7 Professional computers and one Windows Server 2008 computer. Sarah creates an intranet website on her Windows 7 computer that includes current fees for services offered by the medical office.
Other users in the office attempt to access Sarah’s website but are unable to access it. In fact, other users are unable to reach Sarah’s computer using the ping command with either the name or IP address of her computer. But Sarah is able to reach personal files that are stored on the server. How should Peter advise Sarah to enable other users to access her website? (Each answer represents part of the solution. Choose two.) A Open the Windows Firewall with Advanced Security on Local Computer dialog box. On the Public Profile tab, select the Allow option under Inbound Connections. B In the Windows Firewall Control Panel applet, click Change notification settings. In the Customize Settings for Each Type of Network dialog box that appears, click Turn off Windows Firewall under Home or work (private) network location settings. C In the Windows Firewall Control Panel applet, click Change notification settings. In the Customize Settings for Each Type of Network dialog box that appears, clear the check box labeled Block all incoming connections, including those in the list of allowed programs. D In the Windows Firewall Control Panel applet, click Allow a program or feature through Windows Firewall. In the Allow programs to communicate through Windows Firewall dialog box that appears, select Remote Administration. E In the Windows Firewall Control Panel applet, click Allow a program or feature through Windows Firewall. In the Allow programs to communicate through Windows Firewall dialog box that appears, click Change settings, select Add port, and then add TCP port 80 (Hypertext Transfer Protocol, HTTP) to the exceptions list. F Open the Windows Firewall with Advanced Security on Local Computer dialog box. From the left pane, right-click Inbound Rules and choose New Rule. From the New Inbound Rule Wizard, select Port and then specify TCP and Specific local ports. Type 80 in the text box and complete the remaining steps of the wizard. |
C, F.
|
|
|
Kevin is a consultant who is responsible for deploying 200 new Windows 7 Enterprise computers. The client firm has requested that Kevin use the Deployment Workbench and ensure that the Windows 7 images he uses are placed on a distribution share and include all required device drivers, applications, and updates. Which deployment tool should Kevin use?
A Windows Deployment Services (WDS) B Microsoft Deployment Toolkit (MDT) 2010 C Deployment Image Servicing and Management (DISM) D Remote Installation Services (RIS) |
B.
|
|
|
Brendan is a desktop support technician for his company, which operates an Active Directory network consisting of a single domain. All client computers run Windows 7 Enterprise. No policies have been configured in the domain for use of BitLocker or data recovery.
A user named Olga has configured BitLocker Drive Encryption on her laptop, which is equipped with a Trusted Platform Module (TPM). While configuring BitLocker, Olga chose the option to print the recovery password. Olga contacts Brendan and informs him that she is unable to start the computer and cannot remember the recovery password or locate the document on which she printed it. What should Brendan do to enable access to the data? A Access the BitLocker applet in Control Panel and select the Turn Off BitLocker option. B Insert a USB flash drive. C Access the BitLocker Drive Encryption Recovery Console. D Reformat the laptop’s hard drive and reinstall Windows 7. Then restore the data from backup. |
D.
|
|
|
Ethan is a desktop support specialist for a small company that operates a workgroup-based network. A Windows 7 Ultimate computer in his office contains several shared folders that users in the office must have access to. Ethan needs to ensure that only users with valid usernames and passwords can access the shared folders on this computer, including the Public folder. What should he do?
A Configure each shared folder with the usernames of the users who need access. B In the Network and Sharing Center, enable the Public folder sharing option. C In the Network and Sharing Center, disable the Network discovery option. D In the Network and Sharing Center, enable the Password protected sharing option. |
D
|
|
|
Tom is upgrading a computer from Windows Vista Ultimate to Windows 7 Ultimate. The computer is a 2.8 GHz Pentium IV and has 1 GB of RAM and a 250 GB hard disk. After the first restart, Tom is informed that the computer is infected with a master boot record virus. What should he do before continuing with the installation?
A Reboot the computer to Windows Vista Ultimate, and scan and remove all viruses. B Remove or disable any antivirus software installed in Windows Vista. C Run the Check Compatibility Online option and follow any recommendations provided. D Run fixmbr.exe from the Windows 7 DVD-ROM. E Upgrade the computer to 2 GB of RAM. |
B
|
|
|
Owen is a systems administrator for an engineering firm located in Dallas. The firm operates an Active Directory Domain Services (AD DS) domain in which servers run Windows Server 2008 R2 and client computers run Windows 7 Enterprise. Software developers have created two specialized applications that engineers use in their day-to-day work. These engineers have user accounts that belong to the Engineers global group. Some junior employees who do not need access to these applications have fooled around with them, wasting valuable time and jeopardizing vital corporate functions. These applications are not digitally signed, and it is not anticipated that this status will change. Owen’s boss would like him to ensure that only authorized employees have access to these applications. Other applications should not be blocked. What should Owen do? (Each answer represents part of the solution. Choose two.)
A In a GPO linked to the domain, configure an AppLocker path rule that blocks execution of the specialized applications. B In a GPO linked to the domain, configure an AppLocker publisher rule that blocks execution of the specialized applications. C In a GPO linked to the domain, configure an AppLocker file hash rule that blocks execution of the specialized applications. D Specify an exception that allows other programs covered by the rule to execute. E Specify an exception that allows members of the Engineers group to run the applications. |
C, E.
|
|
|
Wayne is a consultant who is preparing a bid for a multimillion dollar contract his company is hoping to land. After working all week on an important document for this bid, Wayne discovers one Friday that this document file has become corrupted. Wayne’s computer runs Windows 7 Enterprise and has system protection enabled on all volumes.
Wayne’s computer is configured with the default backup options. He must recover the latest version of this document so that he can complete the bid with minimal delay because the submission deadline is next Monday. What should Wayne do? A Use System Restore to restore the computer to its state of yesterday afternoon. B Use the Restore previous versions option. C Restore the document from the most recent backup. D Use a system repair disc. |
B
|
|
|
Teresa is preparing a script that will create a virtual hard disk (VHD) on which she will be installing Windows 7. She opens an administrative command prompt and starts the DiskPart utility. Which of the following commands can she use to create a fixed VHD of size 40 GB and named w7.vhd?
A create vdisk file="c:\w7.vhd" maximum=40 type=fixed B create vdisk file="c:\w7.vhd" maximum=40000 type=fixed C create partition primary file="c:\w7.vhd" maximum=40 type=fixed D create partition primary file="c:\w7.vhd" maximum=40000 type=fixed |
B
|
|
|
Paul is using a computer that he has upgraded from Windows Vista Home Premium to Windows 7 Home Premium. He notices that whenever he starts many of his programs or attempts to access the properties of many Control Panel items, he is presented with a UAC prompt. Paul believes that he should not be receiving all these prompts but still would like to be prompted when he attempts to install a program or when websites attempt to make changes to his computer’s configuration. What should Paul do?
A Create shortcuts for the programs that should not receive UAC prompts. On these shortcuts, access the Compatibility tab and select the Run this program as an administrator option. B Access the User Account Control Settings dialog box and select Always notify me when: Programs try to install software or make changes to my computer; I make changes to windows settings. C Access the User Account Control Settings dialog box and select Default–Notify me only when programs try to make changes to my computer. D Access the User Account Control Settings dialog box and select Never notify me when: Programs try to install software or make changes to my computer; I make changes to windows settings. |
C
|
|
|
Sheila is a help desk technician for White’s Photographic Supply, a company that caters to digital photographic needs of camera stores and portrait studios. All desktop computers run either Windows XP Professional or Windows 7 Professional and receive TCP/IP configuration information from a DHCP server on the network.
One evening, several administrators shut down a file server named Server1 for some much-needed maintenance tasks. Several hours later they restart the server and move it to a different subnet. The next morning, Sheila receives calls from several users reporting that they cannot connect to shared folders on Server1. Which of the following commands should Sheila instruct the users to run on their computers? A ipconfig /flushdns and ipconfig /registerdns B ipconfig /release and ipconfig /renew C ipconfig /displaydns D nbtstat –R E nslookup |
A
|
|
|
Nancy is a sales representative for a high technology firm that includes aerospace and defense firms as well as the U.S. military among its clients. She uses a notebook computer running Windows 7 during her visits to client locations. This computer holds confidential data for all clients including data that could provoke a national security incident should the notebook fall into the wrong hands.
Nancy decides to use BitLocker drive encryption to secure the contents of the notebook, which is not equipped with a TPM module. The computer already contains several folders with important data files. Which of the following does she need to do to enable BitLocker on her notebook without losing any existing data? (Each correct answer represents part of the solution. Choose two.) A Use a system repair disc to access the System Recovery Options dialog box and select the Command prompt option. Then repartition the hard drive in the notebook to hold a 40 GB Windows partition and a single partition that holds all data files. B Use a system repair disc to access the System Recovery Options dialog box and select the Command prompt option. Then repartition the hard drive in the notebook to hold a 1.5 GB system partition and a single partition that holds both operating system files and the data files. C In the Local Group Policy Editor, enable the Choose how BitLocker-protected operating system drives can be recovered policy. D In the Local Group Policy Editor, enable the Require additional authentication at startup policy and select the Allow BitLocker without a compatible TPM option. E Use a USB flash drive to hold the encryption keys and access password. F Use a floppy disk to hold the encryption keys and access password. |
D, E
|
|
|
Colby is a network administrator for a company that operates an Active Directory Domain Services (AD DS) domain in which all servers run Windows Server 2008 R2. Client computers run a mix of Windows Vista Enterprise and Windows 7 Professional. Much employee time has been lost to users playing games on their computers during work hours, so Colby would like to create a policy that blocks execution of any games including those installed by default in Windows. He opens a Group Policy object (GPO) linked to the domain. Which of the following policies should he create and enable?
A He should create an AppLocker policy that specifies a path rule that blocks all games. B He should create an AppLocker policy that specifies a hash rule that blocks all games. C He should use Software Restriction Policies to create a policy specifying a path rule that blocks all games. D He should use a Software Installation Policy that uninstalls all game software from affected computers. |
C
|
|
|
Robert is using the User State Migration Tool (USMT) to migrate 100 users in his company from old Windows XP computers to newly purchased computers running Windows 7 Enterprise. He will be using a file server running Windows Server 2008 R2 as a storage location for user documents and settings during the course of the migration. He also wants to ensure that all data is encrypted and password-protected to minimize the possibility of unauthorized access during the migration. What migration strategy should Robert use?
A He should use a wipe-and-load migration utilizing a compressed migration store. B He should use a side-by-side migration utilizing a compressed migration store. C He should use a wipe-and-load migration utilizing a hard-link migration store. D He should use a side-by-side migration utilizing a hard-link migration store. |
B
|
|
|
Kristin has just purchased a new portable computer that runs Windows 7 Ultimate and is setting up a new wireless connection that will enable her to access her company’s wireless access point, which uses the IEEE 802.1x authentication method and the TKIP encryption protocol.
Kristin accesses the Manually connect to a wireless network dialog box and enters the network name and passphrase. She needs to select a security type that will enable connection using the TKIP encryption protocol by default without the need to enter a preshared key or passphrase. Which security type should she select? A WPA-Personal B WPA2-Personal C WPA-Enterprise D WPA2-Enterprise |
C
|
|
|
Lynn is responsible for performance management of 50 computers running Windows 7 Enterprise in her company’s Active Directory Domain Services (AD DS) domain. She has configured Group Policy to assist her in collecting event logs from these computers onto a single Windows 7 Ultimate computer in her work cubicle so that she can identify problems rapidly and respond to users’ concerns. Which of the following should she configure on this computer?
A A source-initiated event subscription B A collector-initiated event subscription C A filter that views logs by event source D A filter that views logs by user and computer |
A
|
|
|
George is using a computer that is equipped with a 100 GB hard disk containing three partitions. The first partition holds an installation of Windows XP Professional, the second partition holds data files, and the third partition is currently empty.
George would like to install Windows 7 on his computer but still have access to Windows XP. What should he do? A Boot the computer with the Windows 7 DVD. Select the option to perform a clean installation, select the first partition, format this partition with the NTFS file system, and install Windows 7 on this partition. B Boot the computer with the Windows 7 DVD. Select the option to upgrade Windows, and install Windows 7 on the first partition. C Boot the computer with the Windows 7 DVD. Select the option to perform a clean installation, select the third partition, format this partition with the NTFS file system, and install Windows 7 on this partition. D Boot the computer with the Windows 7 DVD. Select the option to perform a clean installation, format both the first and third partitions, install Windows 7 on the first partition, and then install XP on the third partition. |
C
|
|
|
Mike uses a Windows 7 Home Premium computer for web browsing, word processing, and photo editing. One day, while on an interesting website, he is offered a new add-on for download. So, he downloads and installs this add-on and then restarts Internet Explorer. However, he is unable to access any websites even though Internet Explorer starts properly. What should Mike do?
A Reset Internet Explorer to default settings. B Run Internet Explorer using the No Add-ons option. C Uninstall the add-on from the Manage Add-ons dialog box. D Uninstall the add-on from the Control Panel Programs applet. |
D
|
|
|
Ross is the network administrator for Bones, LLC. He has configured a new Windows 7 Professional desktop computer that will be used to share files for a folder named FOLDER. Ross has set the security permissions to be as follows:
Authenticated users—Allow Read Administrator—Allow Full Control Accounting—Allow Modify Ross has set the shared folder permissions to be as follows: Everyone—Allow Read Accounting—Deny Full Control Administrators—Allow Full Control Jill is a member of the Accounting group and the Administrators group. When Jill tries to access FOLDER from another computer on the network, what access rights will she have? A Full Control B Modify C Read D None |
D
|
|
|
Ann is responsible for maintaining Windows 7 images for her company. Graphic artists use computers prepared from an image that includes Adobe Photoshop among other applications. This image currently includes Photoshop CS4, but Ann would like to update the image by replacing Photoshop CS4 with Photoshop CS5. What should she do? Each correct answer represents a complete solution. Choose two.
A Use DISM with the /Remove-Package option to remove Photoshop CS4, and then use DISM with the /Add-Package option to add Photoshop CS5 to the image. B Use DISM with the /Remove-Package option to remove Photoshop CS4, and then use the New Application Wizard in MDT 2010 to add Photoshop CS5 to the image. C Use DISM with the /Remove-Apps option to remove Photoshop CS4, and then use the New Application Wizard in MDT 2010 to add Photoshop CS5 to the image. D Use DISM with the /Remove-Package option to remove Photoshop CS4, and then use DISM with the /Add-Apps option to add Photoshop CS5 to the image. |
A,B
|
|
|
Louise is a computer consultant that provides assistance to several clients, working as much as possible from her home office, where she has a Windows 7 Professional desktop computer. She has just entered into a new contract to provide support to a client named DLJ Software, a software company that specializes in high-end computer games as well as complex mathematical and graphical art programs. The company’s network is connected to the Internet through a firewall operated on a Windows Server 2003 computer.
An employee named Andrew sends Louise a Remote Assistance invitation. Louise accepts the invitation but cannot connect to Andrew’s computer. Part of Louise’s contract is the providing of assistance to users in DLJ Software’s, clerical, human resources, and financial departments, most of whom are not very knowledgeable about advanced computer technologies. What should Louise do so she can fulfill her tasks? A Ask Andrew to select the Allow connections only from computers running Remote Desktop with Network Level Authentication (more secure) option. B Ask Andrew to clear the Allow this computer to be controlled remotely option. C Ask Andrew to add Louise’s domain user account to the Remote Desktop Users local group on his computer. D Request that a network administrator open TCP port 3389 on the company firewall. |
D
|
|
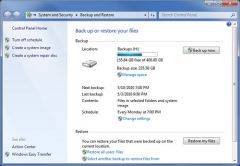
Maria is responsible for a new Windows 7 computer. She has set up Windows Backup to back up her computer’s system image and document files but after a few weeks realizes that an important folder containing images she has shot with her digital camera is not being backed up. So, she opens the Backup and Restore applet and it appears to her as seen in the exhibit. Which location should she select to modify the backup settings to include these digital images?
A Create a system image B Create a system repair disc C Back up now D Manage space E Change settings |
E
|
|
|
Brenda has experienced problems in the past with updates downloaded from the Microsoft website causing applications to fail unexpectedly. So, she has configured Windows Update on her computer to check for updates but to let her choose whether to download and install them.
A few months later, Brenda realizes that an optional patch that her work colleagues have received is missing from her machine, and its performance has suffered as a consequence. What should she do to view and restore this update while retaining the option to let her choose whether to download and install future updates? A From the Windows Update applet in Control Panel, click Change settings, and then select the check box labeled Give me recommended updates the same way I receive important updates. B From the Windows Update applet in Control Panel, click Change settings, and then select the Install updates automatically (recommended) option. C From the Windows Update applet in Control Panel, click View update history, select the update, and then click Restore. D From the Windows Update applet in Control Panel, click Restore hidden updates, select the update, and then click Restore. |
D
|
|
|
Bob is the desktop administrator of his company. A user named Emily installs a tax calculation application on her Windows 7 Professional computer. After she restarts her computer, she observes that the computer runs very slowly.
Emily uninstalls the tax calculation application and restarts her computer. However, the computer still runs very slowly. She asks Bob to return her computer to its previous condition as soon as possible while preserving her data and computer settings. What should Bob do? A Restart the computer with a system repair disc and use the most recent system image to restore the computer. B Restart the computer in safe mode and restore Windows 7 using the most recent system restore point. C Edit the Registry to remove all references to the tax calculation application. D Restart the computer in safe mode and use Wbadmin.exe to restore the most recent system image. E Restart the computer by using the Last Known Good configuration. |
B
|
|
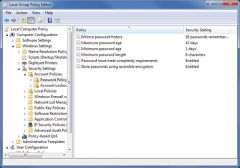
Kane is a desktop support specialist for his company. He is responsible for enforcing policies on a Windows 7 Ultimate computer that are designed to reduce the chance of outsiders hacking passwords on this computer, so he configures the password policy as shown in the exhibit.
The company security auditor comes around and looks at Kane’s password settings. He informs Kane that one of these settings actually reduces the security of the computer’s passwords from its default. Which setting should Kane modify? A Enforce password history B Minimum password age C Minimum password length D Password must meet complexity requirements E Store passwords using reversible encryption |
E
|
|
|
Erin is a temporary employee who is performing accounting tasks for a clothing company named Femme Fatale. The company operates an Active Directory Domain Services (AD DS) domain. The company has its own certification authority (CA) hierarchy hosted on three Windows Server 2008 R2 computers. The company also has a secured internal website named https://www.femmefatale.com/financial.
Erin needs to connect to this website to perform her job, but when she attempts to reach it from her computer running Windows 7 Ultimate, she receives a message that the website certificate is not from a trusted source. She checks with company employees and is assured that this is the correct website name. What should she do to connect successfully to the website? A From the Security tab of the Internet Options dialog box, change the security level of the Local Intranet zone to Low. B From the Advanced tab of the Internet Options dialog box, enable the Use SSL 2.0 option. C From the Content tab of the Internet Options dialog box, install the website certificate to the Trusted Root Certification Authorities certificate store on her computer. D From the Security tab of the Internet Options dialog box, clear the Enable Protected Mode check box. |
C
|
|
|
Judy has run System Image Manager to create an answer file that she intends to distribute to users on a USB flash drive that will be used for installing Windows 7 Professional from a DVD-ROM. She needs to ensure that the answer file has been given the proper name. Which name should this file have?
A Unattend.txt B Unattend.xml C Winnt.sif E Reminst.sif |
B
|
|
|
Phil is concerned with the performance of his Windows 7 computer because it does not appear to be responding as rapidly as it did a few months ago. He creates a data collector set and logs his performance over the period of a workday. Then he uses Performance Monitor to display the collected data and notices the following results:
Memory\Pages/sec: 62 Processor\% Processor Time: 71 LogicalDisk\% Disk Time: 74 PhysicalDisk\% Disk Time: 63 System: Processor Queue Length: 3 Which of the following system upgrades should Phil do first? A Add a faster hard disk. B Add a larger hard disk. C Add additional memory. D Install a faster processor. E Install a second processor. |
C
|
|
|
Jason has been using a computer running Windows XP Home Edition for several years. The computer has suited him well, especially with the several hardware upgrades he has performed over the years, but he is excited about all the new features available in Windows 7, so he purchases the upgrade to Windows 7 Home Premium.
Jason is unsure that all the hardware on his computer will work properly once he has installed Windows 7. What should he do first? A Run the Windows 7 Upgrade Advisor. B Run the Windows 7 Program Compatibility Wizard. C Run the Windows 7 Easy Transfer Wizard. D Access the Device Manager in Windows XP and upgrade the drivers on all hardware devices with the Windows 7–compatible ones. |
A
|
|
|
Kim is responsible for maintaining the virtual hard disk images used on Windows 7 computers in her company. A VHD mounted on the f: drive of a computer contains an image of Windows 7 Home Premium. Kim would like to upgrade this VHD to Windows 7 Ultimate. Which command should she use for this purpose?
A dism /image:f:\ /Set-Edition:Ultimate B dism /image:f:\ /Get-Edition:Ultimate C wdsutil /image:f:\ /Set-Edition:Ultimate D wdsutil /image:f:\ /Get-Edition:Ultimate |
A
|
|
|
You are a tax preparer for Taxes in Texas. All your computers are configured with Windows 7 Enterprise. Because of recent privacy laws, you cannot allow anyone other than official tax preparers to have access to your tax preparation materials for clients. You store all client files in the CLIENTS folder on your NTFS-formatted C: drive, as do all other tax preparers in your workgroup. You have four staff persons who work in the office. They are in the STAFF group. All tax preparers are in the PREP local group. One of the STAFF group members is also a member of the local Administrators group on each computer. What can you do to configure your system to ensure the privacy laws are met?
A Delete all users and groups from your computer. B Configure the PREP group to have full control of the C:\CLIENTS folder. C Run cipher /e on the C:\CLIENTS folder. Add certificates for each tax preparer to the encryption attributes. D Run cipher /d on the C:\CLIENTS folder. Add certificates for the STAFF group. |
C
|
|
|
Evan is the systems administrator for his company. All desktop and portable computers in the company run Windows 7 Enterprise. Users in the Research department bring their portable computers to the conference room for a biweekly planning meeting. These users require a simple means of manually placing their computers in a low-power condition without using the Start menu. In addition, they need their computers to resume normal operating condition as rapidly as possible.
How should Evan configure the Power Options properties to accomplish these needs? A Configure the computers to use the Power saver power plan. B Configure the computers to use the High performance power plan. C Configure the Critical battery alarm on the computers to enable sleep mode when the battery capacity drops to 5%. D Configure the computers to enter sleep mode when the lid is closed. E Configure the power button on each computer to enable hibernation. |
D
|
|
|
Donna is a developer who needs to work with more than one operating system to assess how her applications behave in different conditions. Her computer has a 300 GB hard disk containing three partitions formatted with the FAT32 file system. Windows XP Professional is installed on the first partition. She wants to install Windows 7 Ultimate in a dual-boot configuration.
What should she do? A While running Windows XP, insert the Windows 7 DVD-ROM and follow the prompts provided. When she receives the option to select the type of installation, select Custom (advanced). Then select the second partition to install Windows 7, and format this partition with the NTFS file system. B While running Windows XP, insert the Windows 7 DVD-ROM and follow the prompts provided. When she receives the option to select the type of installation, select Upgrade. Then select the second partition to install Windows 7, and format this partition with the NTFS file system. C Do not reformat any partition. While running Windows XP, insert the Windows 7 DVD-ROM and follow the prompts provided. When she receives the option to select the type of installation, select Custom (advanced). Then select the second partition to install Windows 7. D Do not reformat any partition. While running Windows XP, insert the Windows 7 DVD-ROM and follow the prompts provided. When she receives the option to select the type of installation, select Upgrade. Then select the second partition to install Windows 7. |
A
|
|
|
Barbara has become frustrated as of late because she receives a large quantity of pop-up advertisements when she is browsing the Internet from her Windows 7 Home Premium computer. She would like to eliminate pop-up advertisements from appearing on all websites except http://www.myfavoritesite.com. What should she do? (Each answer represents part of the solution. Choose two.)
A From the Pop-up Blocker Settings dialog box, select the Low blocking level. B From the Pop-up Blocker Settings dialog box, select the Medium blocking level. C From the Pop-up Blocker Settings dialog box, select the High blocking level. D From the Pop-up Blocker Settings dialog box, add the http://www.myfavoritesite.com website as an allowed website. E From the Security tab of the Internet Options dialog box, add the http://www.myfavoritesite.com website to the Trusted Sites zone. |
C, D.
|
|
|
im is deploying 150 new Windows 7 Professional computers to users in his company. These users have old computers running either Windows XP Professional or Windows Vista Business that are to be donated to a charity that refurbishes the computers for use by schoolchildren. Jim must ensure that documents, personal data, and settings for all users are copied from their old computers to their new computers. What should he do?
A Run the Sysprep utility on each old computer. Use a third-party disk imaging utility to create an image of the hard disk. After installing Windows 7 Professional, apply each user’s disk image to his or her new computer. B Use Robocopy.exe to copy all documents and personal data from each user’s old computer to the new computer. Run the Regedit command to export the computer’s Registry to a .reg file. In the installation script for each new computer, copy the documents and personal data to the computer, and import the .reg file. C Use the Recovery Console to start each old computer. Copy the Registry files, documents, and personal data to a network share. In the installation script for each new computer, copy the information from the network share to each new computer. D Run the Scanstate.exe utility on each user’s old computer. Save the information created by the utility to a network share. Run the Loadstate.exe utility in the installation script for each new computer, and specify the network share as the data source. |
D
|
|
|
Leona is the domain administrator for an advertising agency, which operates an Active Directory Domain Services (AD DS) domain. There are 15 Windows Server 2008 computers, 75 Windows XP Professional computers, and 63 Windows 7 Professional computers. The company has just purchased a Plug and Play digital camera for use by the advertising designers, and Leona has installed this camera on a Windows 7 Professional computer.
Leona needs to verify that the drivers for the camera are signed, and she needs to view information about the signer of the drivers. What should she do? A Run the sigverif utility. B View the driver information from Device Manager. C View the driver information from the Components node of the System Information tool. D Verify that the device is listed on the latest version of the Windows 7 Logo Program for Hardware list. |
B
|
|
|
John installs a new application on his computer. The computer immediately exhibits errors and shuts down with a Stop error. John doesn’t know what to do and calls you before he restarts his computer. What do you tell John?
A Restart the computer with the Last Known Good Configuration. B Restart the computer in safe mode and then use System Restore. C Use a system image to restore the computer. D Use the Startup Repair Tool to repair the computer’s configuration. |
A
|
|
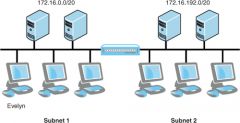
You are the network administrator for a company that operates a network consisting of two subnets separated by a router, as shown in the exhibit.
The subnets are configured with IPv4 addresses according to the network ranges shown in the exhibit. The router interfaces are configured with the IP addresses 172.16.0.1 and 172.16.192.1, respectively, and all client computers are configured with static IP addresses. A user named Evelyn reports that she is unable to access any computers on Subnet 2. She does not have any difficulty accessing computers and their shared resources on Subnet 1. You run ipconfig on her computer and notice that it is configured with the IP address 172.168.11.201, the subnet mask of 255.255.255.0, and the default gateway 172.16.0.1. How should you modify the configuration of Evelyn’s computer so that she is able to reach computers on Subnet B? A Change the subnet mask on Evelyn’s computer to 255.255.240.0. B Change the subnet mask on Evelyn’s computer to 255.255.255.0. C Change the default gateway on Evelyn’s computer to 172.16.192.1. D Access the Advanced TCP/IP Settings dialog box on Evelyn’s computer and configure an additional IP address on the 192.168.11.192/20 network. |
A
|
|
|
Tara is working at her Windows 7 Ultimate desktop computer and wants to use PowerShell to obtain a list of processes running on a Windows Server 2008 R2 machine named Server8. Which of the following commands should she use?
A icm server8 {get-process} B icm server8 get-process C winrs –r:server8 {get-process} D winrs –r:server8 get-process E winrm server8 {get-process} F winrm server8 get-process |
A
|
|
|
Lawrence is a network administrator for the head office of a large bank. As part of a general systems upgrade, the bank has purchased 150 new 500 GB hard disks to be installed in Windows 7 Enterprise computers. These computers already have a single hard disk of 60 to 200 GB capacity, which is configured as a basic volume and formatted with the NTFS file system.
Lawrence needs to write a script that will automate the creation of a simple volume on a new hard disk and mount it to the c:\mounted folder on a Windows 7 Enterprise computer. From the list of commands given, choose the commands that he must include in the script and arrange them in the proper order. A Convert basic B Convert dynamic C Create partition simple disk 1 D Assign mount=c:\mounted E Select disk 1 F Create volume simple disk 1 G Add disk=1 H Mount volume c:\mounted |
E, B, F, H.
|
|
|
Stephanie is a tech support specialist for a company that operates an Active Directory Domain Services (AD DS) network with two domains in a single forest. She has installed Windows 7 Professional on a new computer with the aid of an answer file named Unattend.xml. The answer file instructs the computer to join one of the domains, but after the final reboot, Stephanie discovers that the computer has not joined the domain. Which of the following logs should she use to troubleshoot this problem?
A Setupapi.dev.log B Setuperr.log C Scesetup.log D Setupact.log E Netsetup.log |
E
|
|
|
Connie is using a Windows 7 Professional laptop computer to connect to her company’s VPN server using Secure Sockets Tunneling Protocol (SSTP) to make the connection to a VPN server running Windows Server 2003. When she attempts to complete the connection, she receives an error code 741 accompanied by the message stating that The local computer does not support the required encryption type. What should Connie do to make a successful connection to the VPN server?
A Access the Security tab of the VPN Connection Properties dialog box, select No encryption allowed (server will disconnect if it requires encryption), and then click OK. B Access the Security tab of the VPN Connection Properties dialog box, select Require encryption (disconnect if server declines), and then click OK. C Access the Security tab of the VPN Connection Properties dialog box, select Maximum strength encryption (disconnect if server declines), and then click OK. D Reconfigure her VPN connection to use the Point to Point Tunneling Protocol (PPTP) instead. |
C
|
|
|
Lisa installs a new device driver and reboots her Windows 7 Ultimate computer. Before the logon screen appears, the computer displays the Blue Screen of Death (BSOD) with the error IRQL_NOT_LESS_OR_EQUAL. Which of the following should she do first?
A Press F8 to access the Advanced Startup Options menu. Select Safe Mode, roll back the device driver, and restart the computer. B Press F8 to access the Advanced Startup Options menu. Select Last Known Good Configuration. C Use a system repair disc to restart the computer. From the System Recovery Options dialog box, choose System Restore. D Use a system repair disc to restart the computer. From the System Recovery Options dialog box, choose Command Prompt, remove the device driver, and restart the computer. |
B
|
|
|
Terri has used the DiskPart utility to create a VHD named c:\w7.VHD of size 50 GB on her computer. She now accesses the Disk Management snap-in and wants to create a partition on the VHD that she can use for installing a virtual copy of Windows 7. However, she cannot find the disk listed. What does she need to do before she can proceed further?
A She needs to format the disk. B She needs to convert the disk to dynamic storage. C She needs to mark the disk as active. D She needs to mount the disk. |
d
|

