![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
147 Cards in this Set
- Front
- Back
|
block cipher being developed as a successor to DES. It operates under the symmetric key model.
|
Advanced Encryption Standard (AES)
|
|
|
developed in the 1970s by the National Bureau of Standards with the help of the National Security Agency" with an algorithm submitted by IBM. It operates under the symmetric key model. This is the current standard
|
Data Encryption Standard (DES) and Triple-DES (3DES)
|
|
|
an encryption algorithm that employs the asymmetric key model.
|
Diffie-Hellman
|
|
|
block cipher used in PGP. unlike the other block cipher algorithms is patented by the Swiss firm of Ascom. They have, however, been generous in allowing, with permission, free noncommercial use of their algorithm, with the result that ______ is best known as the block cipher algorithm used within the popular encryption program PGP."
|
International Data Encryption Algorithm (IDEA)
|
|
|
993 by Bruce Schneier as a fast, free alternative to existing encryption algorithms. Since then it has been analyzed considerably, and it is slowly gaining acceptance as a strong encryption algorithm.
|
Blowfish
|
|
|
unpatented, and the source code is uncopyrighted and license-free; it is free for all uses." (Counterpane Internet Security: ________: A New Block Cipher) It operates under the symmetric key model.
|
Twofish
|
|
|
family of algorithms that employ the asymmetric key model. There are actually multiple incarnations of this algorithm; RC5 is one of the most common in use.
|
Rivest-Shamir-Adelman (RSA)
|
|
|
Select this check box to rely on a common passphrase rather than on public key cryptography. The file is encrypted using a session key, which encrypts using a passphrase that you will be asked to choose.
|
Conventional Encryption
|
|
|
Select this checkbox to create a self decrypting executable file. If you select this option, the file is encrypted using a session key, which encrypts (and decrypts) using a passphrase that you are asked to choose. To decrypt the file, double-click it and enter the appropriate passphrase. This option is especially convenient for user’s who are sending encrypted files to people who do not have PGP software installed.
|
Self Decrypting Archive (SDA)
|
|
|
focuses on immediate response, but if the attack escalates or is disastrous the process changes to disaster recovery and BCP
|
IRP
|
|
|
typically focuses on restoring systems after disasters occur, and as such is closely associated with BCP
|
DRP
|
|
|
occurs concurrently with DRP when the damage is major or long term, requiring more than simple restoration of information and information resources
|
BCP
|
|
|
A high-level manager to support, promote, and endorse the findings of the project
|
Champion
|
|
|
Leads the project and makes sure a sound project planning process is used, a complete and useful project plan is developed, and project resources are prudently managed
|
Project Manager
|
|
|
Should be the managers or their representatives from the various communities of interest: Business, IT, and Information Security
|
Team Members
|
|
Fill in the Blanks of the Contingency Planning Hierarchy.
|
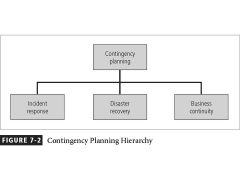
Contingency Planning, Incident Response, Disaster recovery, and business continuity
|
|
Fill in the steps of the Contingency Planning Timeline.
|
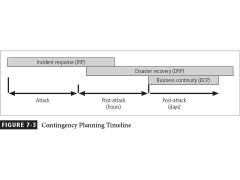
Incident Response (IRP), Disaster Recovery (DRP), and Business Continuity (BCP)
|
|
|
What has the following steps.
1. Treat attack identification 2. Business unit analysis 3. Attack Success Scenarios 4. Potential Damage Assessment 5. Subordinate Plan Classification |
Business Impact Analysis (BIA)
|
|
|
The detailed description of activities during an attack
|
Attack Profile
|
|
|
* The second major task within the BIA is the analysis and prioritization of business functions within the organization
* Identify the functional areas of the organization and prioritize them as to which are most vital * Focus on a prioritized list of the various functions the organization performs |
Business Unit Analysis
|
|
|
whether or not an organization is able to take effective action during the event to combat the effect of the attack
|
Qualifying Differene
|
|
|
________ is an attack against an information asset that poses a clear threat to the confidentiality, integrity, or availability of information resources
|
An Incident
|
|
|
Attacks are only classified as incidents if they have what three characteristics?
|
Are directed against information assets
Have a realistic chance of success Could threaten the confidentiality, integrity, or availability of information resources |
|
|
What are the following?
*intrusion detection systems, both host-based and network-based *virus detection software *systems administrators *end users |
Possible Incident Detectors
|
|
|
When Does an Incident Become a Disaster?
|
* the organization is unable to mitigate the impact of an incident during the incident
* the level of damage or destruction is so severe the organization is unable to quickly recover * It is up to the organization to decide which incidents are to be classified as disasters and, thus, receive the appropriate level of response |
|
|
consists of actions that guide the organization to stop the incident, mitigate the impact of the incident, and provide information for the recovery from the incident
|
Incident Reaction
|
|
|
What are the following the steps of?
* There must be a clear establishment of priorities * There must be a clear delegation of roles and responsibilities * Someone must initiate the alert roster and notify key personnel * Someone must be tasked with the documentation of the disaster * If and only if it is possible, some attempts must be made to mitigate the impact of the disaster on the operations of the organization |
Disaster Recovery Plan (DRP)
|
|
|
actions taken during and after a disaster focusing on the people involved and addressing the viability of the business
|
Crisis Managment
|
|
|
outlines reestablishment of critical business operations during a disaster that impacts operations
|
Business Continuity Planning
|
|
|
The bulk batch-transfer of data to an off-site facility.
|
Electronic Vaulting
|
|
|
The transfer of live transactions to an off-site facility; only transactions are transferred not archived data, and the transfer is real-time.
|
Remote Journaling
|
|
|
Not only processing duplicate real-time data storage, but also duplicates the databases at the remote site to multiple servers.
|
Database Shadowing
|
|
|
* Fully configured and ready to operate within a few hours of a disaster
* Can support a short- or long-term outage * Flexible in its configuration and options |
Hot Site
|
|
|
* Partially configured with some equipment
* Essentially provide the facility and some peripheral devices, but not a full configuration like a hot site |
Warm Site
|
|
|
*Supplies basic computing environments including wiring, ventilation, plumbing, and flooring
|
Cold Site
|
|
|
What are these the six steps of?
1. Identifying the mission- or business-critical functions 2. Identifying the resources that support the critical functions 3. Anticipating potential contingencies or disasters 4. Selecting contingency planning strategies 5. Implementing the contingency strategies 6. Testing and revising the strategy |
Contingency Planning Process
|
|
|
What is the major drawback to law enforcement involvement?
|
You lose control of your data and systems.
|
|
|
deals with many computer crimes that are categorized as felonies
|
Federal Bureau of Investigation
|
|
|
works with crimes involving US currency, counterfeiting, credit cards, identity theft, and other crimes
|
US Secret Service
|
|
|
has a bank fraud investigation unit and the Securities and Exchange Commission has investigation and fraud control units as well
|
US Treasury Department
|
|
|
What is the biggest advantage to law enforcement involvement?
|
Better equipt
|
|
|
what was
* Developed in a language called ABAP * Platform that includes the operating system and database called Basis |
R/3
|
|
|
*Language of choice is Java and ABAP
* Basis is replace with the SAP Web Application Server (WAS) which implements the J2EE 1.3 standard * Extended by several products including BI, Portals and others |
SAP NetWeaver
|
|
|
* Creates professional user interfaces while minimizing manual coding
* Uses visual design tools and reuses UI components * Users Model-View-Controller architecture, clear separation between UI and backend services |
Web Dynpro
|
|
|
* An abstraction of the database that allows more platform independence than JDBC
* Allows a direct relational interface or an object-based interface to access data with little work on the part of the developer |
Open SQL
|
|
|
Facilitates unified access to enterprise applications to enable Drag and Relate operations
|
Unification technology
|
|
|
Renders HTML pages which users interact
|
Page builder
|
|
|
Create users and assign then roles
|
Use role management
|
|
|
Single sign on to all systems
|
User management
|
|
|
Built on proven technology. A solution verified for large data warehouses (5+ Tb)
|
Performance/Scalability
|
|
|
Integrates business processes. Provides a centralized metadata repository with a consistent business semantic. Read-to-go templates and best-practices – horizontal and vertical business content.
|
Business Orientation
|
|
|
Supports decision-making requirements of every user.
|
Actionable Information
|
|
|
A platform for process integration based upon the exchange of XML messages
|
Exchange Infrastructure (XI)
|
|
|
To tap the contents of text documents by structuring and classifying them so relevant information is available
|
Knowledge Management
|
|
|
Is designed to provide a unified view of data from a distributed and heterogeneous environment
|
Master Data Management (MDM)
|
|
|
A model-driven development environment that allows applications to be assisted by the use of modeling to describe the structure of the application so that code and interfaces of various sorts can be generated.
|
Composite Application Framework (CAF)
|
|
|
Security mechanisms:
security clearance of personnel, pwd protection, information classification, security policies, application program controls, audit |
External procedures
|
|
|
Security mechanisms:
hazards, fire, flooding, radiation |
Physical security
|
|
|
Security mechanisms:
encryption, duplication, hot, cold sites |
Data storage
|
|
|
Security mechanisms:
authentication, access, threat monitoring, audit trail |
Processor software
|
|
|
Security mechanisms:
memory protection, reliability |
Processor hardware
|
|
|
Security mechanisms:
encryption |
Communication lines
|
|
|
A critical element of security and control in a financial application is monitoring of
|
Great Plains Dynamics (GPD)
|
|
|
What GPD tool combines inquiry and reporting capabilities to provide easier access to Dynamics business objects
|
SmartList
|
|
|
__________________________ can also be used to set the SmartList views that will be available to a specific user or to a specific user class.
|
SmartList Security window
|
|
|
For security by ___________, the settings apply to the members of the class without regard to what Dynamics Company they work with.
|
user class
|
|
|
For a ______________, select the company these settings should apply to.
|
single user
|
|
|
what is a classification feature in Dynamics in which users are grouped and given the same levels of access to the accounting system.
|
user class
|
|
|
states that in lists of numbers from many real-life sources of data, the leading digit is 1 almost one third of the time, and larger numbers occur as the leading digit with less and less frequency as they grow in magnitude, to the point that 9 is the first digit less than one time in twenty. This is based on the observation that real-world measurements are generally distributed logarithmically, thus the logarithm of a set of real-world measurements is generally distributed uniformly.
This counter-intuitive result applies to a wide variety of figures, including electricity bills, street addresses, stock prices, population numbers, death rates, lengths of rivers, physical and mathematical constants, and processes described by power laws (which are very common in nature). Even more counter-intuitively, the result holds regardless of the base in which the numbers are expressed, although the exact proportions of course change. |
Benford's law
|
|
|
Is used to analyze data and produce reports for both non-technical and expert users. It saves you time and money by accomplishing in minutes what used to take hours or even days.
|
ACL
|
|
|
is the perceived level of risk that a material misstatement may occur in the client's un-audited financial statements, or underlying levels of aggregation, in the absence of internal control procedures.
|
Inherent risk (IR)
|
|
|
is the perceived level of risk that a material misstatement in the client's un-audited financial statements, or underlying levels of aggregation, will not be detected and corrected by the management's internal control procedures
|
control risk (CR)
|
|
|
is the perceived level of risk that a material misstatement in the client's un-audited financial statements, or underlying levels of aggregation, will not be detected by the auditor.
|
detection risk (DR)
|
|
|
The higher the assessment of inherent and control risk the more ________________ the IS auditor should normally obtain from the performance of substantive audit procedures.
|
audit evidence
|
|
|
_______________ is broadly defined as a process, effected by an entity's board of directors, management and other personnel, designed to provide reasonable assurance regarding the achievement of objectives in the following categories:
Effectiveness and efficiency of operations. Reliability of financial reporting. Compliance with applicable laws and regulations. |
Internal control
|
|
|
has established a common definition of internal controls, standards, and criteria against which companies and organizations can assess their control systems.
|
COSO
|
|
|
is a term used for a number of concepts involving either the performance of an investigation of a business or person, or the performance of an act with a certain standard of care. It can be a legal obligation, but the term will more commonly apply to voluntary investigations.
|
Due diligence
|
|
|
identifying, assessing and evaluating the levels of risk facing the organization, also begins in this stage.
|
risk management task
|
|
|
has been considered the industry standard for computer security since the development of the mainframe. It was solely based on three characteristics that described the utility of information: confidentiality, integrity, and availability.
|
The C.I.A. triangle
|
|
|
weaknesses or faults in a system or protection mechanism that expose information to attack or damage
|
Vulnerability
|
|
|
a category of objects, persons, or other entities that represents a potential danger to an asset.
|
Threats
|
|
|
to take advantage of weaknesses or vulnerability in a system
|
Exploit
|
|
|
an act that is an intentional or unintentional attempt to cause damage or compromise to the information and/or the systems that support it.
|
Attack
|
|
|
a subject or object’s ability to use, manipulate, modify, or affect another subject or object.
|
Access
|
|
|
the probability that something can happen.
|
Risk
|
|
|
an active entity that interacts with an information system and causes information to move through the system for a specific end purpose
|
Subject
|
|
|
he action of gathering, analyzing, and applying information about products, domain constituents, customers, and competitors for the short term and long term planning needs of an organization
|
Competitive intelligence
|
|
|
Name the threat Category:
Accidents, employee mistakes |
Acts of human error or failure
|
|
|
Name the threat Category:
Piracy, copyright infringement |
Compromise to intellectual property
|
|
|
Name the threat Category:
Unauthorized access and/or data collection |
Deliberate acts of espionage or trespass
|
|
|
Name the threat Category:
Blackmail of information disclosure |
Deliberate acts of information extortion
|
|
|
Name the threat Category:
Destruction of systems or information |
Deliberate acts of sabotage or vandalism
|
|
|
Name the threat Category:
Illegal confiscation of equipment or information |
Deliberate acts of theft
|
|
|
Name the threat Category:
Viruses, worms, macros, denial-of-sevice |
Deliberate software attacks
|
|
|
Name the threat Category:
Fire, flood, earthquake, lightning |
Forces of nature
|
|
|
Name the threat Category:
Power and WAN service issues |
Deviations in quality of services from service providers
|
|
|
Name the threat Category:
Equipment failures |
Technical hardware failures or errors
|
|
|
Name the threat Category:
Bugs, code problems, unknown loophols |
Technical software failures or errors
|
|
|
Name the threat Category:
Antiquated or outdated technologies |
Technological obsolescence
|
|
|
A risk management strategy calls on us to “know ourselves” by identifying, classifying, and prioritizing the organization’s information assets
|
Risk Identification
|
|
|
Modification of Systems Development Life Cycle for risk managment
|
waterfall methodology
|
|
|
We can determine the relative risk for each of the vulnerabilities through a process called _______________.
|
Risk Assessment
|
|
|
what formula is used for Risk Determination
|
RISK ={(likelihood of vulnerability occurrence)*(value or impact)}- percentage risk already controlled + an element of uncertainty
|
|
|
strategies for risk management:
Apply safeguards |
avoidance
|
|
|
strategies for risk management:
Transfer the risk |
transference
|
|
|
strategies for risk management:
Reduce the impact |
mitigation
|
|
|
strategies for risk management:
Inform themselves of all of the consequences and accept the risk without control or mitigation |
acceptance
|
|
|
is simply how often you expect a specific type of attack to occur, per year
|
Annualized Rate of Occurrence (ARO)
|
|
|
is the calculation of the value associated with the most likely loss from an attack
|
Single Loss Expectancy (SLE)
|
|
|
is the percentage loss that would occur from a given vulnerability being exploited
|
exposure factor (EF)
|
|
|
What is the formula for Single Loss Expectancy (SLE)?
|
asset value x exposure factor (EF)
|
|
|
What is the formula for Annualized Loss Expectancy (ALE) ?
|
= Single Loss Expectancy (SLE) * Annualized Rate of Occurrence (ARO)
|
|
|
Rather than use the financial value of information assets, review peer institutions to determine what they are doing to protect their assets
|
benchmarking
|
|
|
_________is the analysis of measures against established standards
|
Baselining
|
|
|
___________ defines the quantity and nature of risk that organizations are willing to accept as they evaluate the tradeoffs between perfect security and unlimited accessibility
|
Risk appetite
|
|
|
What are the three types of plans that help mitigate damages causes by incidents?
|
1. incident response planning (IRP)
2. disaster recovery planning (DRP) 3. business continuity planning (BCP) |
|
|
_________ direct how issues should be addressed and technologies used
|
Policies
|
|
|
What are the following examples of?
* high risk, moderate risk, low risk * board confidential, senior management confidential, department confidential, company confidential, public |
Information Classification
|
|
|
One of the foundations of security architectures is the requirement to implement security in layers. __________________ requires that the organization establish sufficient security controls and safeguards, so that an intruder faces multiple layers of controls
|
Defense in depth
|
|
|
The point at which an organization’s security protection ends, and the outside world begins, is referred to as the __________________. Unfortunately the _________ does not apply to internal attacks from employee threats, or on-site physical threats.
|
security perimeter
|
|
|
An ___________________________ is used to detect many types of malicious network traffic and computer usage that can't be detected by a conventional firewall. This includes network attacks against vulnerable services, data driven attacks on applications, host based attacks such as privilege escalation, unauthorized logins and access to sensitive files, and malware (viruses, trojan horses, and worms).
|
intrusion detection system
|
|

What is this model known as?
|

The Triangle model
|
|
|
Positive identification of person/system seeking access to secured information/services
|
Authentication
|
|
|
Predetermined level of access to resources
|
Authorization
|
|
|
Logging use of each asset
|
Accounting
|
|
|
Unique alphanumeric identifier used to identify an individual when logging onto a computer/network
|
Username
|
|
|
Secret combination of keystrokes that, when combined with a username, authenticates a user to a computer/network
|
Password
|
|
|
____________ prevents eavesdropping or replay attacks, and ensures the integrity of the data. Its designers aimed primarily at a client-server model, and it provides mutual authentication — both the user and the server verify each other's identity.
__________ builds on symmetric key cryptography and requires a trusted third party. |
Kerberos
|
|
|
Point-to-Point Protocol (PPP) mechanism used by an authenticator to authenticate a peer
|
Challenge Handshake Authentication Protocol (CHAP)
|
|
|
Electronic means of verifying identity of an individual/organization
|
Digital Certificates
|
|
|
Converts plain text message into secret message
|
Encryption
|
|
|
Converts secret message into plain text message
|
Decryption
|
|
|
Uses only one key
|
Symmetric cipher
|
|
|
Uses a key pair (private key and public key)
|
Asymmetric cipher
|
|
|
Trusted, third-party entity that verifies the actual identity of an organization/individual before providing a digital certificate
|
Certificate authority (CA)
|
|
|
Practice of using a trusted, third-party entity to verify the authenticity of a party who sends a message
|
Nonrepudiation
|
|
|
* Authentication devices assigned to specific user
* Small, credit card-sized physical devices * Incorporate two-factor authentication methods * Utilize base keys that are much stronger than short, simple passwords a person can remember |
Security Tokens
|
|
|
Security Token Type:
* Act as a storage device for the base key * Do not emit, or otherwise share, base tokens |
Passive
|
|
|
Security Token Type:
* Actively create another form of a base key or encrypted form of a base key that is not subject to attack by sniffing and replay * Can provide variable outputs in various circumstances |
Active
|
|
|
what type of authentication does the following?
* Uses measurements of physical or behavioral characteristics of an individual * Generally considered most accurate of all authentication methods * Traditionally used in highly secure areas Expensive |
Biometrics
|
|
|
This is what percent of the time will an authorized person be rejected by the system.
|
FRR (False Rejection Rate)
Type 1 error rate |
|
|
This is what percent of the time will an unauthorized person be accepted by the system?
|
FAR (False Acceptance Rate)
Type 2 error rate |
|
|
Point at which FRR and FAR is?
|
cross over
|
|
|
Known to be the most secure type of biometric authentication.
|
Retina
|
|
|
What are the important factors to consider when choosing a biometric technology for your application? ______________will show you how each technology ranks for cost, accuracy, effort and ease of use.
|
Zephyr Analysis
|
|
|
_____________ is the art and science of writing hidden messages in such a way that no one apart from the intended recipient knows of the existence of the message; this is in contrast to cryptography, where the existence of the message itself is not disguised, but the content is obscured. Quite often, _________________ is hidden in pictures.
|
Steganography
|
|
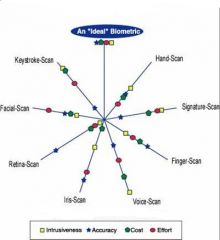
What does this diagram represent?
|
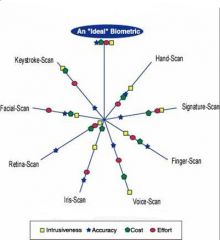
The Zephyr Analysis
|

