![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
75 Cards in this Set
- Front
- Back
|
chipping code
|
a spread spectrum modulation scheme that generates a redundant bit pattern for each transmitted bit. The bit pattern, called a chip or chipping code, enables receivers to filter out signals that don't use the same bit pattern, including noise or interference. The chipping code serves two primary functions: 1) It identifies the data so that the receiver can recognize it as belonging to a certain transmitter. The transmitter generates the chipping code and only receivers that know the chipping code can decipher the data. 2) The chipping code spreads the data across the available bandwidth. Longer chips require more bandwidth but allow a greater probability that the original data can be recovered. Even if one or more bits in the chip are damaged during transmission, technology embedded in the radio can recover the original data using statistical techniques without the need for retransmission.
---HP Wireless FAQ's--- |
|
|
co-location
|
Ability to co-exist with other access-points. FHSS has the advantage.
|
|
|
direct sequence
|
A system for generating spread spectrum transmissions by phase-modulating a sine wave pseudorandomly by an unending string of pseudonoise code symbols, each of duration much smaller than a bit. http://answers.com
|
|
|
narrowband
|
Using only enough frequency that is required to get job done. Normally higher powered than Spread Spectrum.
|
|
|
noise floor
|
background noise. signal-to-noise ratio is critical.
|
|
|
processing gain
|
is the ratio of the spread bandwidth to the unspread bandwidth. It is usually expressed in decibels (dB).
http://answers.com |
|
|
Throughput vs Bandwidth
|
answering
|
|
|
PSK
|
Phase Shift Keying
|
|
|
DPSK
|
Differential Phase Shift Keying: 0,180
|
|
|
DQPSK
|
Differential Quaternary Phase Shift Keying: 0,90,180,270
|
|
|
CCK
|
Complementary Code Keying
|
|
|
802.11
|
base standard:
1Mbps and 2Mbps FHSS and DSSS |
|
|
802.11b
|
1,2,5.5, 11
HR-DSSS |
|
|
802.11a
|
6, 9, 12, 18, 24, 36, 48, 54
OFDM |
|
|
802.11d
|
802.11d is a wireless network communications specification for use in countries where systems using other standards in the 802.11 family are not allowed to operate.
The 802.11d specification is similar in most respects to 802.11b. The main difference is that the configuration can be fine-tuned at the Media Access Control layer (MAC layer) level to comply with the rules of the country or district in which the network is to be used. .... ---SearchMobileComputing.com Definitions--- |
|
|
802.11e
|
Enhancement to 802.11 that includes quality of service (QoS) features
Facilitates prioritization of data, voice, and video transmissions ---SearchMobileComputing.com Definitions--- |
|
|
802.11F
|
Recommended Practice - defines the management frame that stations use to request reassociation with a a 2nd AP, an the mangemnet frame that APs use to grant or deny the reassociation.
---CWNA studies--- |
|
|
802.11g
|
***Extends the maximum data rate of WLAN devices that operate in the 2.4 GHz band, in a fashion that permits interoperation with 802.11b devices
***Uses OFDM Modulation (Orthogonal FDM) ***Operates at up to 54 megabits per second (Mbps), with fall-back speeds that include the "b" speeds ---SearchMobileComputing.com Definitions--- |
|
|
802.11h
|
***Enhancement to 802.11a that resolves interference issues (military, medical, Europe)
***Dynamic frequency selection (DFS) ***Transmit power control (TPC) ---SearchMobileComputing.com Definitions--- |
|
|
802.11i
|
***Enhancement to 802.11 that offers additional security for WLAN applications
***Defines more robust encryption, authentication, and key exchange, as well as options for key caching and pre-authentication ---SearchMobileComputing.com Definitions--- |
|
|
802.11j
|
Japanese regulatory ***extensions to 802.11a specification
***Frequency range 4.9 GHz to 5.0 GHz ---SearchMobileComputing.com Definitions--- |
|
|
802.11n
|
***Higher-speed standards -- under development
***Several competing and non-compatible technologies; often called "pre-n" ***Top speeds claimed of 108, 240, and 350+ ... ***Competing proposals come from the groups, EWC, TGn Sync, and WWiSE and are all variations based on MIMO (multiple input, multiple output) ---SearchMobileComputing.com Definitions--- |
|
|
802.11s
|
amendment will define standards for automatically forming mesh networks with 802.11 access points.
---CWNA p318--- |
|
|
UNII bands
|
UNII - Unlicensed National Information Infrastructure
|
|
|
ISM bands
|
ISM - Industrial, Scientific, Medical
|
|
|
IV
|
Initialization Vector
|
|
|
WEP
|
Wired Equivalent Privacy (WEP)
|
|
|
WPA
|
WPA --- WiFi Protected Access --- pre 802.11i solution provided by the Wi-Fi Alliance (Oct 2002) to counteract weaknesses in WEP.
***based on a Draft 3 of the IEEE 802.11i standard. |
|
|
What are the weaknesses of WEP?
|
***1 The IV value is too short and not protected from reuse.
***2 The way keys are constructed from the IV makes it susceptible to weak key attacks (FMS attack). ***3 There is no effective detection of message tampering (message integrity). ***4 It directly uses the master key and has no built-in provision to update the keys. ***5 There is no protection against message replay. |
|
|
2 modes of WPA
|
WPA - requires RADIUS
WPA-PSK - pre-shared-key |
|
|
TKIP
|
TKIP -
Temporal Key Integral Protocol |
|
|
WPA2
|
WPA2 - certifies compatibility with 802.11i
|
|
|
EAP
|
Extensible Authentication Protocol - RFC 3748
---wikipedia--- |
|
|
LEAP
|
The Lightweight Extensible Authentication Protocol (LEAP) is a proprietary EAP method developed by Cisco Systems prior to the IEEE ratification of the 802.11i security standard.
---wikipedia--- |
|
|
EAP-TLS
|
EAP-Transport Layer Security or EAP-TLS, defined in RFC 2716, is an IETF open standard, and is well-supported among wireless vendors. It offers a good deal of security, since TLS is considered the successor of the SSL standard. It uses PKI to secure communication to the RADIUS authentication server or another type of Authentication Server. So even though EAP-TLS provides excellent security, the overhead of client-side certificates may be its Achilles' heel.
---wikipedia--- |
|
|
EAP-MD5
|
EAP-MD5, defined in RFC 3748, is another IETF open standard, but offers minimal security. The MD5 hash function is vulnerable to dictionary attacks, and does not support mutual authentication or key generation, which makes it unsuitable for use with dynamic WEP, or WPA/WPA2 enterprise.
---wikipedia--- |
|
|
EAP-PSK
|
EAP-PSK, defined in RFC 4764, is the first pure symmetric-key EAP method with appropriate security that was fully specified and reviewed by IETF. It is a light and extensible method that does not resort to any public-key cryptography.
---wikipedia--- |
|
|
EAP-TTLS
|
EAP-Tunnelled Transport Layer Security, or EAP-TTLS is an EAP protocol that extends TLS. It was co-developed by Funk Software and Certicom. It is widely supported across platforms, and offers very good security. The client does not need be authenticated via a CA-signed PKI certificate to the server, but only the server to the client. This greatly simplifies the setup procedure as a certificate does not need to be installed on every client.
---wikipedia--- |
|
|
EAP-IKEv2
|
EAP-IKEv2 is an EAP authentication method based on the Internet Key Exchange Protocol version 2 (IKEv2). It provides mutual authentication and session key establishment between an EAP peer and an EAP server.
---wikipedia--- |
|
|
PEAP
|
Protected Extensible Authentication Protocol (PEAP) is a joint proposal by Cisco Systems, Microsoft and RSA Security as an open standard. It is already widely available in products, and provides very good security. It is similar in design to EAP-TTLS, requiring only a server-side PKI certificate to create a secure TLS tunnel to protect user authentication
---wikipedia--- |
|
|
EAP-FAST
|
EAP-FAST
(Flexible Authentication via Secure Tunneling) is a protocol proposal by Cisco Systems as a replacement for LEAP. ---wikipedia--- |
|
|
EAP-SIM
|
EAP-SIM
EAP for GSM Subscriber Identity is used for authentication and session key distribution using the Global System for Mobile Communications (GSM) Subscriber Identity Module (SIM). EAP-SIM is defined in RFC 4186. ---wikipedia--- |
|
|
EAP-AKA
|
EAP-AKA --
(EAP for UMTS Authentication and Key Agreement) is used for authentication and session key distribution using the Universal Mobile Telecommunications System (UMTS) Universal Subscriber Identity Module (USIM). EAP AKA is defined in RFC 4187. |
|
|
BSS
|
Basic Service Set
|
|
|
BSSID
|
Basic Service Set ID - 48 bit hex value -- MAC of AP.
|
|
|
ESS
|
Extended Service Set ---consists of two or more BSSs that share the same SSID
|
|
|
ESSID
|
Extended Service Set ID ---
denotes a group of BSSs sharing a common SSID within which a station can roam seamlessly. ---CWNA studies p333--- |
|
|
SSID
|
Service Set Identifier
|
|
|
Beacons
|
Beacons are frames sent from the acces point to stations (in infrastructure networks) or station-to-station (ad-hoc)
---CWNA studies--- |
|
|
Active Mode
|
when a station is in ACTIVE MODE, it stays awake 100 percent of the time.
---CWNA studies--- |
|
|
active scanning
|
ACTIVE SCANNING involves the sending of a probe request frame from a CLIENT STATION to an access point.
---CWNA studies--- |
|
|
passive scanning
|
PASSIVE SCANNING is the process of listening for beacons on each channel for a specific period of time.
---CWNA studies--- |
|
|
TIM
|
Traffic Indication Map -- TIM is used as an indicator of which stations operating in power-save mode have packets queued at the access point.
---CWNA studies--- |
|
|
Open System Authentication
|
The sender and the recipient do not share a secret key. Each party generates its own key-pair and asks the receiver to accept the (usually randomly) generated key. Once accepted, this key is used for a short time only, then a new key is generated and agreed upon.
---Netgear--- |
|
|
Shared Key Authentication
|
The following steps occur when two devices use Shared Key Authentication:
1. The station sends an authentication request to the access point. 2. The access point sends challenge text to the station. 3.The station uses its configured 64-bit or 128-bit default key to encrypt the challenge text, and it sends the encrypted text to the access point. 4. The access point decrypts the encrypted text using its configured WEP key that corresponds to the station's default key. The access point compares the decrypted text with the original challenge text. If the decrypted text matches the original challenge text, then the access point and the station share the same WEP key, and the access point authenticates the station. 5. The station connects to the network. ---Netgear--- |
|
|
Association
|
Associated is the state at which a client is a member of a particular infrastructure BSS.
The process of association involves only four frames. ---CWNA studies p342--- |
|
|
DTIM
|
Delivery Traffic Indication Message
|
|
|
ATIM
|
Announcement Traffic Indication Message
|
|
|
CSMA/CA
|
Carrier Sense, Multiple Access, with COLLISION AVOIDANCE
================= CSMA/CA belongs to a class of protocols called multiple access methods. CSMA/CA stands for: Carrier Sense Multiple Access With Collision Avoidance. In CSMA/CA, a station wishing to transmit has to first listen to the channel for a predetermined amount of time so as to check for any activity on the channel. If the channel is sensed "idle" then the station is permitted to transmit. If the channel is sensed as "busy" the station has to defer its transmission. This is the essence of the "collision avoidance" part of the protocol. ===answers.com=== |
|
|
RTS
|
Request to Send
|
|
|
CTS
|
Clear to Send
|
|
|
initialization vector
|
(IV) A continuously changing number used in combination with a secret key to encrypt data. Initialization vectors (IVs) are used to prevent a sequence of text that is identical to a previous sequence from producing the same exact ciphertext when encrypted. For example, packets have address fields that are generally fixed in location within the header of the packet. If attackers view the same encrypted data over and over, it provides them with clues to interpret their original values.
-------TechWeb------- |
|
|
RC4
|
RC4 is a symmetric stream cipher with an arbitrary key size. RC4 was created by Ron Rivest of RSA Security in 1987.
-------- This is the same cipher that is used in other crypto systems such as Secure Sockets Layer (SSL) (HTTPS). -------- WEP utilizes the RC4 Stream Cipher from RSA. This is the same cipher that is used in other crypto systems such as Secure Sockets Layer (SSL) (HTTPS). The problem with WEP is that, again, the 802.11 protocol did not define how to implement IVs. As mentioned earlier, the key used in the RC4 cipher is a combination of a shared secret and an IV. The IV is a 24-bit binary number. Many manufacturers will claim to have 64-bit or 128-bit WEP, which is somewhat misleading, since 24 bits of each of these keys are the IV that is sent in clear text. Technically, the shared secret portions of the keys are really only 40 or 104 bits long. ---- Again, the issue with WEP is not the RC4 Cipher—it's how RC4 is implemented. |
|
|
802.1p
|
IEEE 802.1p is a standard that provides traffic class expediting and dynamic multicast filtering. Essentially, it provides a mechanism for implementing Quality of Service (QoS) at the MAC (Media Access Control) level. -------
Eight different classes of service are available, expressed through the 3-bit user_priority field in an IEEE 802.1Q header added to the frame. The way traffic is treated when assigned to any particular class is undefined and left to the implementation. The IEEE however has made some broad recommendations. ------- 802.1p is used within the IEEE 802.1D and IEEE 802.1Q standards. |
|
|
802.1x
|
This brings us to the IEEE 802.1x standard, which is simply a standard for passing EAP over a wired or wireless LAN. With 802.1x, you package EAP messages in Ethernet frames and don't use PPP. It's authentication and nothing more. That's desirable in situations in which the rest of PPP isn't needed, where you're using protocols other than TCP/IP, or where the overhead and complexity of using PPP is undesirable.
|
|
|
DCF
|
Distributed Coordinated Function --- uses RF carrier sense, IFS, and Random Back-off/Contention Windows.
|
|
|
IFS
|
Interframe spacing
|
|
|
split-mac architecture
|

...shifts some of the functions traditionally on the autonomous AP to a central device.
|
|
|
edcf
|
enhanced distributed coordination function (used by 802.11e and its WMM subset)
|
|
|
WMM
|
Wifi MultiMedia - created during standardization process of 802.11e
|
|
|
Where are "non-real-time" functions handled in spli-mac-arch ?
|

Wireless Lan Controller --
(cisco ONT cert guide P.239) |
|
|
where are REAL-time-functions handled in a split-MAC architecture?
|

at the LWAP (lightweight AP) --
(cisco ONT cert guide P.239) |
|
|
LWAPP
|
lightweight access point protocol (ietf draft standard 57)
|
|
|
QoS Marking Mapping Table
|
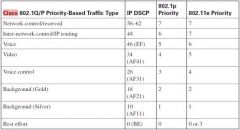
see jpeg
|
|
|
Mapping of 8211e Priority levels to WMM Access Categories
|
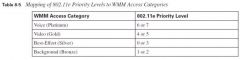
see jpeg
|

