![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
27 Cards in this Set
- Front
- Back
|
A mathematical algorithm, utilizing public and private keys, which is used by PKI to commuinicate securely.
a Public Key Infrastructure (PKI) |
b |
|
|
Typically a dedicated workstation used to install certicates onto smart cards. Can be configured with restricted policies to issue certificates only to specific security groups.
f Smart Cards |
g |
|
|
A server that issues and manages digital certifcates for use in a PKI.
a Public Key Infrastructure (PKI) |
c |
|
|
A CA not integrated with AD that can be taken offline
j Online Certificate Status Protocol (OCSP)
CA = certificate authority |
l |
|
|
Identifies certificates that have been revoked/terminated and the corresponding user, computer, or service.
e Certificate Revocation List (CRL) |
e |
|
|
Allows for two-factor authentication to an AD domain, a website, or other secured resources.
e Certificate Revocation List (CRL) |
f |
|
|
Consists of a number of elements that allow two parties to communicate securely through public key cryptography.
a Public Key Infrastructure (PKI) |
a |
|
|
Allows private keys to be restored if they're lost. Requires the key archival service.
f Smart Cards |
h |
|
|
Certs used by the CA to simplify the issuance and administration of PKI certificates by controlling the security settings associated with each template
l Standalone CA m Enterprise CA
CA = certificate authority |
o |
|
|
A digital document that contains identifying information (certificate holder's name and public key) about a user, computer, service, etc.
a Public Key Infrastructure (PKI) |
d |
|
|
A trusted server that receives and responds to individual clients requrests for information about the status of a cert.
g Enrollment Agents |
i |
|
|
Allows small devices on a network to enroll for certificates that might otherwise not be able to do so.
i Online responder |
k |
|
|
A CA integrated with AD that can't be taken offline but can use certificate templates for certificate autoenrollment and storage within AD
k Network Device Enrollment Service (NDES)
CA = certificate authority |
m |
|
|
A protocol used in place of a traditional CRL to return certificate status information.
g Enrollment Agents
CRL = certificate revocation list |
j |
|
|
An ________ is a list of access control entries (ACE). Each ACE in an _______ identifies a trustee and specifies the access rights allowed, denied, or audited for that trustee.
l Standalone CA m Enterprise CA |
n |
|
|
One or more online responders can be chained together to form a(n) ___________. |
responder array Pg 270 |
|
|
A(n) __________ is a CA that integrates with AD and allows autoenrollment of user and computer certificates through the use of group policy and certificate templates. |
Enterprise Certification Authority Pg 270 |
|
|
The top-level CA in any PKI hierarchy is the ____________. |
Root CA Pg 270 |
|
|
One alternative to public key cryptography is to use a(n) ______________. |
Shared secret key Pg 268 |
|
|
Each PKI certificate consists of a public key that is widely known and a(n) __________ that is known only to the user or computer who holds the certificate. |
private key Pg 268 |
|
|
Users can request certificates via the web using the _____________ service. |
Certification Authority Web Enrollment Pg 278 |
|
|
The most common use of certificates is for user enrollment with autoenrollment permitted. In this case the subject must be granted which of the following permissions (choose 3):
a - full control b - read c - write d - enroll e - autoenroll |
b - read d - enroll e - autoenroll (technet.microsoft.com) |
|
|
(from practice exam) Scenario: Network has one Server 08 AD domain, no PKI*, IPSec is planned, certificates will be used for authentication. You want to deploy certificates for automatic enrollment and only one server is available to run certificate services. What should you do?
a - install a standalone root CA b - install an online responder c - install an enterprise root CA d - install a standalone issuing CA
*public key infrastructure |
c - Enterprise root CA. Automatic enrollment is configured using certificate templates, which are only supported by enterprise CAs due to their dependence on AD. And because you are installing just one CA, it must be a root CA (top-level CA authoritative for all certificate services within the network).
-Standalone CA used in absence of AD -Online responder responds to verification requests - it can't be the only server in a PKI because it must receive a cert from an enterprise issuing CA. |
|
|
You are installing a PKI hierarchy and have 3 servers to work with. Srv1 & 2 are on domain. Srv2 is already a fileserver and so should be used as little as possible. Srv3 is not on the domain. Requirements: -The root CA must be secure -AD domain members must be issued certs automatically -Switches and routers must be able to enroll for certs -Company security policy prohibits HTTP/S from being accepted on a cert server. Which of the following services should you use and on which servers should you put them? 1. cert auth* (standalone) 2. cert auth (enterprise) 3. cert auth web enrollment 4. online responder 5. network device enrollment svc 6. cert enrollment web svc 7. web server (IIS) 8. remote server admin tools * auth=authority |
Srv1 - cert auth (enterprise) Srv2 - network device enrollment svc, web server, remote server admin tools Srv3 - cert auth (standalone)
The root CA should be on an offline server - installed on Srv3 (which is not on the domain).
Automatic enrollment is enabled by the enterprise CA - the issuing CA.
Lastly, Network device enrollment service allows switches and routers to obtain certificates, even though they are not domain members. Since this service requires web server and remote server admin tools to be installed, and thus uses HTTP/S, it can't be installed on a cert server (per company sec policies) - this leaves just one server for the job. |
|
|
(practice exam) Your company is planning to implement smart card authentication and the certificate enrollment must mee the following requirements: - User interaction should be minimized - Certificates must use the cryptographic service provider (CSP) installed by the manufacturer's software. - Smart card certs must be valid for 2+ years and be able to protect email.
You need to create the certificate template that will be used to issue smart card certs. What should you do?
a - Duplicate the existing smart card user cert template. Change the CSP and the validity period. b - Duplicate the existing smart card logon cert template. Change the CSP and the validity period. c - Do the same as (a) + select enroll subject without requiring user input. d - Do the same as (b) + select enroll subject without requiring user input. |
a. Since the predefined smart card user template allows users to log on and protect email with a smart card, most of your work is already done for you. All you'd need to do is change the CSP and the validity of the smart card user cert to be done. |
|
|
(practice exam) Your network consists of a single AD domain. You have installed AD certificate services on a server 08 R2 server named CSServer1 and have a user named David that has been given the responsibility of approving certificate enrollments and revocations. You need to ensure he can perform these tasks while granting only the necessary permissions. What should you do? a - assign him to the account operators group b - assign him the certificate manager role c - assign him the auditor role d - assign him the CA admin role |
B - The cert mgr role will provide him the necessary permissions. - The CA Administrator role would provide him the ability to configure and manage the CA server while not providing him the permissions he needs to approve or revoke certificates. - The account operators group would allow him to log on to servers locally, create and manage user and group accounts, and shut down. |
|
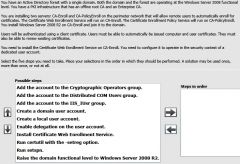
|
1. Create a domain user account (to run the Cert Web Enrollment Service (CWES)) 2. Add the account to the IIS_IUsr group (a required membership before you can select a user account as the security context for CWES). At this point you are ready to install the CWES and select the user account during installation. 3. Install CWES 4. Run setspn to generate a Service Principal Name (SPN) for the service, which will be associated with the user account you create. 5. Enable delegation on the user account (to allow it to act on behalf of the user requesting a cert) Notes: - No reason to raise the forest functional level. Although the CWES is supported only on Server 08R2, it requires only the server 08 functional level to operate. |

