![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
33 Cards in this Set
- Front
- Back
|
Reasons to use VLANS:
|
To create more flexible designs that group users by department, or by groups that work together, instead of by physical location
|
|
|
Reasons to use VLANS:
|
To segment devices into smaller LANs (broadcast domains) to reduce overhead caused to each host in the VLAN
|
|
|
Reasons to use VLANS:
|
To reduce the workload for the Spanning Tree Protocol (STP) by limiting a VLAN to a single access switch
|
|
|
Reasons to use VLANS:
|
To enforce better security by keeping hosts that work with sensitive data on a separate VLAN
|
|
|
Reasons to use VLANS:
|
To separate traffic sent by an IP phone from traffic sent by PCs connected to the phones
|
|
|
VLAN header is removed from a frame before it is put out the destination port.
|
VLAN trunking is used on the segments between switches. VLAN trunking uses VLAN tagging by wich the sending switch adds another header before sending it over the trunk.
|
|
|
VLAN ID field is inserted into the VLAN header. It tells the recieving switch which VLAN the frame belongs in.
|
The use of trunking allows swithces to pass frames from multiple VLANS over a single physical connection.
|
|
|
ISL Trunking:
Proprietary CISCO trunking created before 802.1Q. Can ONLY be used between CISCO switches that support it. |
ISL fully encapsulates each frame in an ISL header and trailer. The original frame inside the ISL header and trailer remains unchanged.
|
|
|
ISL includes a VLAN field containing the VLAN ID in the header.
|
The source and destination addresses in the ISL header use the MAC addresses of the sending and receiving switch INSTEAD of the sending and receiving devices.
|
|
|
802.1Q is an IEEE standardized trunking protocol.
|
802.1Q is the more popular trunking protocol. Some Cisco switches have no support for ISL but do support 802.1Q.
|
|
|
802.1Q does NOT encapsulate the frame with a VLAN header. Instead it inserts a VLAN ID into the original Ethernet header of the frame and recalculates the FCS field.
|
Both trunking protocols have VLAN ID's within them.
|
|
|
Both protocols support the same number of VLANS 2 ^12 (4096) VLAN ID's minus 2 reserved values (0 and 4095).
|
VLAN's 1 - 1005 are normal range VLANs. Higher then 1005 are called extended range VLANs.
|
|
|
ISL and 802.1Q both support separate instances of STP.
|
802.1Q defines one VLAN on each trunk as a native VLAN. ISL does not include a Native Vlan.
|
|
|
802.1Q by default VLAN1 is the native Vlan. The native VLAN does NOT get a VLAN ID added to its header.
|
A native VLAN enables a trunking switch to be connected to a switch that does not understand trunking.
|
|
|
Each VLAN must be its own subnet.
|
VLAN is a layer 2 concept, subnet is a layer 3 concept.
|
|
|
For a host to forward packets between subnets a router MUST be involved.
A Layer 3 switch can replace the router. |
VTP - Vlan Trunking Protocol is a Cisco proprietary protocol used so that CISCO switches can exchange VLAN configuration information.
|
|
|
VTP advertises about the existence of each VLAN based on its VLAN ID but NOT the details about which switch interfaces are assigned to each vlan.
|
VTP is a layer 2 messaging protocol.
|
|
|
3 VTP modes:
server, client and transparent mode. |
To disable VTP you enable VTP transparent mode. Otherwise CISCO switches cannot disable VTP.. Transparent
|
|
|
Only switches in server mode can be used to configure VLAN information
|
In transparent mode a switch ignores the information but forwards it.
|
|
|
Name the 4 fields in the 802.1Q Trunking header
|
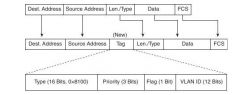
Type (16 bit) | Priority (3 bit) | flag (1 bit) | VLAN ID (12 bits)
|
|
|
VTP servers and clients choose whether to react to a received VTP update, and update their VLAN configurations based on whether the VLAN database configuration revision number increases.
|
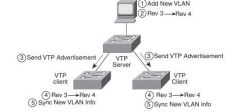
Someone configures a new VLAN from the command-line interface (CLI) of a VTP server.
The VTP server updates its VLAN database revision number from 3 to 4. The server sends VTP update messages out its trunk interfaces, stating revision number 4. The two VTP client switches notice that the updates list a higher revision number (4) than their current revision numbers (3). The two client switches update their VLAN databases based on the server's VTP updates. |
|
|
The complete process by which a server changes the VLAN configuration, and all VTP switches learn the new configuration, resulting in all switches knowing the same VLAN IDs and name, is called synchronization.
|
VTP servers and clients also send periodic VTP messages every 5 minutes,
|
|
|
The VTP domain name provides a design tool by which engineers can create multiple groups of VTP switches, called domains, whose VLAN configurations are autonomous.
|
A VTP password is never transmitted in clear text
|
|
|
Transparent mode gives a switch autonomy from the other switches. VTP Autonomous mode is used instead of a shutdown command.
|
VTP transparent mode switches do forward VTP updates to connected switches.
|
|
|
To forward traffic for a VLAN, a switch needs to know the VLAN's VLAN ID and its VLAN name. VTP's job is to advertise these details, with the full set of configuration for all VLANs being called the VLAN configuration database, or simply VLAN database.
|
VLAN configuration is stored in flash memory as vlan.dat. It is NOT stored in startup.config.
|
|
|
Command to delete vlan database: delete flash:vlan.dat
Command to delete startup: erase startup-config |
Commands to completely delete information off a switch:
delete flash:vlan.dat erase startup-config |
|
|
Default Vlan Configuration
VTP Server mode No VTP domain name VLAN1, VLANs 1002 - 1005 are automaticaly configured and cannot be deleted All acess interfaces are assigned to VLAN1 (an implied switchport access vlan 1 command) |
The Allowed VLAN list feature provides a mechanism for engineers to administratively disable a VLAN from a trunk:
switchport trunk allowed vlan {add | all | except | remove} vlan-list |
|
|
Reasons a switch would not allow a VLAN's traffic:
A VLAN has been removed from the trunks allowed VLAN list. A VLAN does not exist or is not active in the switches VLAN database (as seen with the SHOW VLAN command). A VLAN has been automatically pruned by VTP A VLANs STP instance has placed the trunk interface into a state other than a forwarding state. |
A VLAN can be administratively shut down on any switch by using the SHUTDOWN VLAN VLAN-ID global configuration command.
|
|
|
Cisco IP phones use Ethernet to connect to the IP network for the purpose of sending Voice
over IP (VoIP) packets. |
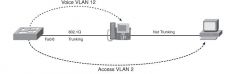
CIsco IP phones include a LAN Switch that allows a trunk onto the phone.
|
|
|
For Cisco IP phones 802.1Q trunking is used and the local PC to the phone and the phone should be in different VLANs.
|
Voice VLAN: Vlan for Cisco IP phones
Access VLAN: Data Vlan (traditional) |
|
|
The Voice VLAN is configured with the:
switchport voice vlan vlan-id interface subcommand |
Cisco Recommended VLAN security configurations:
Administratively disable the unused interface, using the shutdown interface subcommand. Prevent trunking from being negotiated when the port is enabled by using the switchport nonegotiate interface subcommand to disable negotiation or the switchport mode access interface subcommand to statically configure the interface as an access interface. Assign the port to an unused VLAN sometimes called a parking lot VLAN using the switchport access vlan number interface subcommand. |
|
|
VLANs logically divide a switch into multiple, independent switches at Layer 2.
Each VLAN is its own broadcast domain. Each VLAN should be in its own subnet. |
Know the advantages of VLANs:
. Increase the number of broadcast domains while reducing their size. .Provide additional security. . Increase the flexibility of network equipment. .Allow a logical grouping of users by function, not location. .Make user adds, moves, and changes easier. |
|
|
Switchport port security features must be enabled on each interface by typing the
switchport port-security command. Unfortunately, switchport port security cannot be enabled on a global basis |
Switchport port security features must be enabled on each interface by typing the
switchport port-security command. Unfortunately, switchport port security cannot be enabled on a global basis |

