![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
10 Cards in this Set
- Front
- Back
|
Feature Driven Development |
Develop Overall Model - High level walk-through of system scope and context involving the creation of domain models. One or more (combination) of these models is used to become the model for each domain area. Build Feature List - Models created in the first stage are used to compile a list of features. Features should take no longer than two weeks to complete. Plan by Feature - Development plan is produced and ownership of features is assigned. Design by Feature - A design package is produced for each feature. Sequence diagrams are worked out for each feature. Class and method prologues are written followed by a design inspection. Build by Feature - Class owners develop code for their classes. Unit testing and code inspection follow. Each completed feature is promoted to the main build. |
|
|
Test Driven Development Lifecycle |
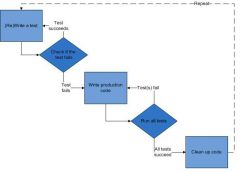
The purpose is to test each component thoroughly before release. |
|
|
MVC Data Handling |
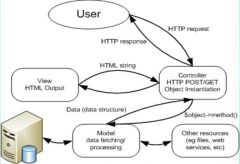
|
|
|
Encryption |
To transform data to keep it secret from others. The goal is to ensure that the data cannot be seen by anyone other than the recipient(s). This process uses a secret key, the plaintext and the algorithm operation. The ciphertext, algorithm and key are all needed to return the plaintext. Algorithms: AES, Blowfish, RSA |
|
|
Hashing |
Hashing is the process of turning text into a fixed length string of characters that is unintelligible. These cannot be decrypted. Algorithms: SHA-3, MD5 |
|
|
HTTP and Sessions |
HTTP is stateless, meaning that it does not require the server to retain session information or status about each communications partner for the duration of multiple requests. Sessions are employed to overcome this. It acts as a workaround to support session state over a stateless protocol. This is achieved through the use of HTTP cookies. These are small pieces of data sent from the website to the user's computer. |
|
|
Session and Cookie Security Risks |
Cookie Theft - Can be done through XSS by posting malicious code to a website. The code could make a button appear that would (once clicked) send cookie information to a malicious web page. DNS Cache Poisoning - |
|
|
Definition: Web Service |
An application developed as loosely coupled software components that is remotely available over TCP/IP. |
|
|
Web Services: Advantages |
Deployability: Deployed over standard Internet technologies with SSL built in. - Interoperability: Web services allow applications to talk and share data with each other. - Low Cost for Communication: SOAP over HTTP. Low cost option. |
|
|
Web Services: Disadvantages |
- Vulnerable to DoS Attacks: The services can be overloaded with too many requests over a short space of time. - Stateless: No information is retained by either sender or receiver. Sessions can be used to work around this. |

