![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
125 Cards in this Set
- Front
- Back
|
Linux has a kernel-level packet filter called _____.
|
IPchains
|
|
|
In an IP packet header, the _____ address is the address of the computer or device that is to receive the packet.
|
destination
|
|
|
In an IP packet header, the _____ header length describes the length of the header in 32-bit words and is a 4-bit value.
|
Internet
|
|
|
The default value of the Internet header length in an IP packet header is __.
|
20
|
|
|
The size of the time to live field in an IP packet header is _.
|
8
|
|
|
The size of the flag field in an IP packet header is _.
|
3
|
|
|
The maximum length of an IP packet that can be defined in the total length field is ___,___.
|
165,535
|
|
|
The number in the header's _____ field tells a firewall how to reassemble a data stream that has been divided into packets.
|
identification
|
|
|
The most effective security approach for a stateless packet filter is to deny all except _____ hosts.
|
specified
|
|
|
Criteria that _____ filters can be configured to use include IP header information, TCP or UDP port numbers, and ICMP message type.
|
stateless
|
|
|
A stateless filter compares a packet's header data against its _____ base and forwards only those packets that match a rule.
|
rule
|
|
|
____ ___ ___ includes specifications for six control flags in a TCP header.
|
ITEF RFC 793
|
|
|
Telnet uses port __.
|
23
|
|
|
The protocol number for TCP is _.
|
6
|
|
|
The protocol number for IGMP is _.
|
2
|
|
|
TCP port __ is used to filter out Web traffic.
|
80
|
|
|
A router receiving too much traffic is a possible cause for an ICMP source _____ message.
|
quench
|
|
|
Too many hops to destination is a possible cause of an ICMP time _____ message.
|
exceeded
|
|
|
The single bit of information in a TCP packet that indicates whether a packet is requesting a connection or whether a connection has already been established is the ___.
|
ACK
|
|
|
_____ packet filtering works by controlling the type of transport and the port number being used.
|
Stateful
|
|
|
Some traffic, such as ICMP uses packets that are hard to _____ reliably.
|
filter
|
|
|
Some stateful firewalls are able to examine the contents of packets as well as the headers for signs that they are _____.
|
legitimate
|
|
|
ICMP packets can be easily forged and used to _____ other communication.
|
redirect
|
|
|
____ is the most common command to use ICMP.
|
PING
|
|
|
The ICMP packet filter rule “____ _____” gives your computers the ability to ping external computers.
|
echo request
|
|
|
The ICMP packet filter rule “___ _____” prevents hackers from receiving replies to ping requests.
|
echo reply
|
|
|
The ICMP packet filter rule “____ _____” drops all other ICMP packets after setting your rules.
|
ICMP block
|
|
|
Secure HTTP uses port ___.
|
443
|
|
|
DNS uses port __ for connection attempts.
|
53
|
|
|
FTP uses port __ for the control port.
|
21
|
|
|
_____ is the act of identifying users and providing network services to them based on their identity.
|
Authenticating
|
|
|
Forms of authentication include _____, _____, and _____-_____.
|
basic,centralized, and challenge-response
|
|
|
A physical object such as a smart card is an example of a _____.
|
token
|
|
|
In the firewall _____ process, the firewall intercepts the request and prompts the user for a name and password.
|
authentication
|
|
|
After the user authentication step (in the firewall authentication process), the request is checked against the firewall's ____ base.
|
rule
|
|
|
In the firewall authentication process, after the user submits the proper information to the firewall, the user is _____.
|
authenticated
|
|
|
_____ _____ Firewall-1 provides the following authentications: user, session and client.
|
Check Point
|
|
|
User authentication is useful for employees in _____ offices.
|
branch
|
|
|
_____ authentication will help you establish limits to user access.
|
Client
|
|
|
A standard _____-__ is one in which the client, after being successfully authenticated, is allowed to access whatever resources the user needs.
|
sign-on
|
|
|
A specific sign-on system is one in which the client is required to _____ each time the user wants to access a server.
|
authenticate
|
|
|
_____ authentication calls for authentication to be made whenever a client wants to connect to a network resource and establish a session.
|
Session
|
|
|
Client and session authentication should only be used when a single user is coming from a single __ address.
|
IP
|
|
|
You should use both _____ and _____ authentication when the protocol in use is not HTTP, FTP, HTTPS, rlogin, or Telnet.
|
client and session
|
|
|
You should use _____ authentication when the protocol in use is HTTP, FTP, HTTPS, rlogin, or Telnet.
|
user
|
|
|
You should use _____ authentication when you want to scan the content of IP packets.
|
user
|
|
|
In _____ authentication an ACS alleviates the need to provide each server on the network with a separate database of usernames and passwords.
|
centralized
|
|
|
In centralized authentication ___ levels of trust are involved.
|
two
|
|
|
_____ authentication methods include TACACS+, RADIUS, and Kerberos.
|
Centralized
|
|
|
_____ was developed at MIT.
|
Kerberos
|
|
|
In the _____ system, after the client requests a file or other resource, the client is prompted for a username and password.
|
Kerberos
|
|
|
In the ______ system, after the AS grants the TGT, the TGS grants the session ticket.
|
Kerberos
|
|
|
In the _____ system, after the TGS grants the session ticket, the client gains access.
|
Kerberos
|
|
|
The Kerberos authentication server is also known as the ___.
|
KDC
|
|
|
The typical time length of a Kerberos ticket is _____ hours.
|
eight
|
|
|
_____ developed TACACS+.
|
Cisco
|
|
|
The MD5 algorithm produces a 128-bit code called a _____ digest.
|
message
|
|
|
_____ transmits authentication packets unencrypted across the network.
|
RADIUS
|
|
|
RADIUS uses UDP port ____ for accounting.
|
1813
|
|
|
Hashed passwords are passwords that have been _____.
|
encrypted
|
|
|
Challenge-response and password lists are examples of ___-____ passwords.
|
one-time
|
|
|
In ___-____ authentication, a physical object is required for a user to authenticate.
|
two-factor
|
|
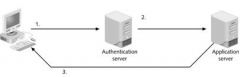
In step 2 in the figure above, the _____ server authorizes the client.
|
authentication
|
|
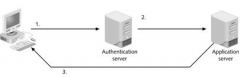
In step 3 in the figure above, the request is checked against the firewall's _____ base.
|
rule
|
|
|
In the predefined IPSec policy - _____ (Respond Only) – level, the computer itself will not initiate communications using IPSec but can participate when another computer requires it.
|
Client
|
|
|
The predefined IPSec policy - _____ (Request Security) – level is being used when a host requests that IPSec be used to communicate but if the other computer is not configured for IPSec the two computers can still communicate.
|
Server
|
|
|
In the predefined IPSec policy - _____ _____ (Require Security) - a host with IPSec enabled only will communicate with other IPSec enabled hosts.
|
Secure Server
|
|
|
IPSec used between a private and a public network via a firewall, requires port Protocol ID __ to be opened if AH is used.
|
51
|
|
|
IPSec used between a private and a public network via a firewall, requires port IP protocol ID __ and UDP port ___ to be opened if ESP is used.
|
50 / 500
|
|
|
Digital _____ are used to authenticate individual users.
|
certificates
|
|
|
When using IPSec, the source gateway address, destination gateway address, and the packet size are _____.
|
unencrypted
|
|
|
_____ encrypts the IP connection between two machines.
|
IPSec
|
|
|
IPSec _____ machines.
|
authenticates
|
|
|
PGP and SSL are _____ applications.
|
encryption
|
|
|
In a 1997 survey by the CIO institute, ____ out of five civilian agency security managers did not know how often they were being attacked or by whom.
|
four
|
|
|
Packet sniffing is a _____ attack that scans for open ports.
|
passive
|
|
|
A man in the middle attack takes place when a hacker _____ part of an encrypted data session to gain control over the data being exchanged.
|
intercepts
|
|
|
The following encrypted _____ are available for use on the Internet: digital signatures, public keys, and private keys.
|
codes
|
|
|
Many organizations make use of ____, which holds publicly available information about digital certificates as well as individual users in the organization and the organization's network.
|
LDAP
|
|
|
A ___ is the framework that enables the distribution of digital certificates and public and private keys.
|
PKI
|
|
|
Digital certificates can be ____ client based and server based.
|
both
|
|
|
A server that is located in the network where people can apply to obtain a digital certificate that they can distribute is called a _____ _____.
|
registration authority
|
|
|
When you install Check Point _____-_ you are prompted to enter one hundred random characters of text.
|
Firewall-1
|
|
|
The use of a KDC is a form of ___ management.
|
key
|
|
|
A session ___ exists only during the length of communication between the hosts.
|
key
|
|
|
Check Point Firewall-1 uses a proprietary encryption scheme called ___.
|
FWZ
|
|
|
When using a _____ key system in an organization of 100 users who all need to exchange information, each user would be required to use one hundred separate keys.
|
symmetric
|
|
|
Asymmetric encryption is _____ than symmetric encryption.
|
slower
|
|
|
The name of the standard set of specifications for assembling and formatting digital certificates and encrypting data within them is _.___.
|
X.509
|
|
|
When you wipe a file with ___, all traces of it are deleted permanently.
|
PGP
|
|
|
If you use PGP or X.509, one aspect of the digital certificate that remains the same is the _____.
|
subject
|
|
|
___ makes use of symmetric and asymmetric keys.
|
SSL
|
|
|
E-mail, web traffic, and FTP file transfers can be protected by _____.
|
IPSec
|
|
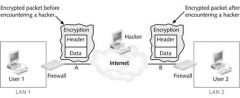
In the figure above, encryption takes place at _ to protect the packet.
|
A
|
|
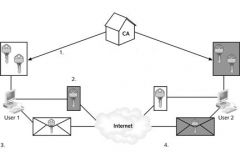
A ___exchange system is displayed in the figure above.
|
key
|
|
|
Other names for _____ servers are proxy service, application proxy, and application-level gateway.
|
proxy
|
|
|
A proxy server has ___ interfaces.
|
two
|
|
|
In a proxy server configuration, the firewall should be directly connected to the _____.
|
Internet
|
|
|
_____ servers can conceal internal clients, block URLs, and block and filter content.
|
Proxy
|
|
|
A proxy server protected network appears to be a _____ machine to an external client.
|
single
|
|
|
Full text URLs are typically _____ by a proxy server.
|
blocked
|
|
|
Your _____ server should filter or block Java applets, executable e-mail attachments, and activeX controls.
|
proxy
|
|
|
Time, IP addresses, and port numbers can be _____ out by a proxy server.
|
filtered
|
|
|
When a firewall log is used to determine whether an unauthorized user has accessed resources that should be protected, its function is to _____ intrusions.
|
detect
|
|
|
When a firewall log can point to ports, machines, or other vulnerable computers through which hackers can gain entry, its function is to uncover _____.
|
weaknesses
|
|
|
Some proxy servers use _____ to notify you if a possible attack is in progress.
|
alerts
|
|
|
One consideration that must be taken into account when choosing a proxy server (as a network grows) is _____.
|
scalability
|
|
|
In _____ _____ no proxy server needs to be specified for FTP and Gopher connections because the browser can use the SOCKS standard.
|
Internet Explorer
|
|
|
HTTP, DNS, and SMTP traffic can be _____ by a proxy server.
|
monitored
|
|
|
___ sharing is a feature of Windows 2000 Advanced Server that allows you to create multiple proxies that are in use simultaneously.
|
Web
|
|
|
_____ overflows are the most common problem a proxy server can fall victim to.
|
Buffer
|
|
|
A _____ firewall combines several different security technologies.
|
hybrid
|
|
|
A _____ proxy can be configured to be totally invisible to an end user.
|
transparent
|
|
|
An _____ proxy requires the client software to be configured to use the proxy server.
|
explicit
|
|
|
_____ is typically used to forward all target traffic to the proxy at a single target port.
|
SOCKS
|
|
|
A _____ consists of an IP address and a port number.
|
socket
|
|
|
Port TCP/____ is the typical target port that SOCKS uses to direct all traffic from the client to the proxy.
|
1080
|
|
|
_____ is the name of the free SOCKS application available from Permeo Technologies.
|
SocksCap
|
|
|
T.REX, WinGate, and Squid are open source _____ applications.
|
proxy
|
|
|
_____ is the most popular proxy server for home and small business environments.
|
WinGate
|
|
|
Symantec Enterprise Firewall filters content using a technology it calls _____.
|
WebNOT
|
|
|
The Windows ____ Server operating system is required to support ISA Server.
|
2000
|
|
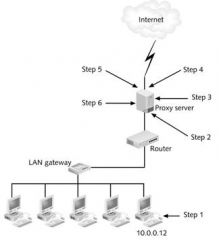
In step 3 of the figure above, the proxy server recreates the packet with a different _____ address.
|
source
|
|
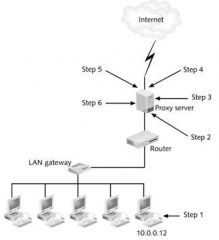
In step 5 of the figure above, the returned packet is inspected and compared against the ____ base.
|
rule
|
|
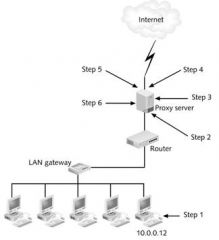
In step 1 of the figure above, an internal host makes a _____ to access a Web site.
|
request
|

