![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
81 Cards in this Set
- Front
- Back
|
CIA
|
Confidentiality
Privacy Integrity |
|
|
Confidentiality
|
Data Confidentiality
-Assures that private or confidential information is not made available or disclosed to unauthorized individuals. Privacy -Assures that individuals control or influence what information related to them may be collected and stored and by whom and to whom that information may be disclosed. |
|
|
Integrity
|
Data Integrity
-Assures that information and programs are changed only in a specified and authorized System Integrity -Assures that a system performs its intended function in an unimpaired manner, free from deliberate or inadvertent unauthorized manipulation of the system. |
|
|
Avalability
|
Assures that systems work promptly and service is not denied to authorized users.
|
|
|
Low Breaches and Impacts
|
The loss could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals. A limited adverse effect means that, for example, the loss of confidentiality, integrity, or availability might:
(i) cause a degradation in mission capability to an extent and duration that the organization is able to perform its primary functions, but the effectiveness of the functions is noticeably reduced; (ii) result in minor damage to organizational assets; (iii) result in minor financial loss; or (iv) result in minor harm to individuals. |
|
|
Medium Breaches and Impacts
|
The loss could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. A serious adverse effect means that, for example, the loss might
(i) cause a significant degradation in mission capability to an extent and duration that the organization is able to perform its primary functions, but the effectiveness of the functions is significantly reduced; (ii) result in significant damage to organizational assets; (iii) result in significant financial loss; or (iv) result in significant harm to individuals that does not involve loss of life or serious, life-threatening injuries. |
|
|
High Breaches and Impacts
|
The loss could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals. A severe or catastrophic adverse effect means that, for example, the loss might
(i) cause a severe degradation in or loss of mission capability to an extent and duration that the organization is not able to perform one or more of its primary functions; (ii) result in major damage to organizational assets; (iii) result in major financial loss; or (iv) result in severe or catastrophic harm to individuals involving loss of life or serious life-threatening injuries. |
|
|
Methods of prohibiting attacks
|
Encipherment
Digital Signature Access Control Data Integrity Authentication Exchange Traffic Padding Routing Control Notarization |
|
|
Threat
|
A potential for violation of security, which exists when there is a circumstances, capability, action, or event, that could breach security and cause harm. That is, a threat is a possible danger that might exploit a vulnerability.
|
|
|
Vulnerability
|
A flaw or weakness in a system's design, implementation, or operation and management that could be exploited to violate the system's security policy.
|
|
|
Adversary
|
Threat Agent
An entity that attacks, or is a threat to, a system. |
|
|
Security Concepts and Relationships
|
Figure 1.2
|
|
|
Corrupted
|
Does the wrong thing or gives wrong answers
|
|
|
Vulnerability: Leaky
|
-someone who should not have access to some or all of the info available through the network obtains such access
Unavailable -Using the system or network becomes impossible or impractical. |
|
|
Vulnerability: Unavailable
|
Using the system or network becomes impossible or impractical.
|
|
|
Attack: Active
|
An attempt to alter system resources or affect their operation
|
|
|
Attack: Passive
|
An attempt to learn or make use of information from the system that does not affect system resources
|
|
|
Attack: Inside
|
Initiated by an entity inside the security perimeter. Authorized access but uses them for unintended use.
|
|
|
Attack: Outside
|
Initiated from outside the perimeter. Unauthorized and/or illegal
|
|
|
Unauthorized Disclosure
|
A circumstance or event whereby an entity gains access to data for which the entity is not authorized.
|
|
|
Unauthorized Disclosure Threat Action
|
Exposure
Interception Inference Intrusion |
|
|
Deception
|
A circumstance or event that may result in an authorized entity receiving false data and believing it to be true.
|
|
|
Deception Threat Action
|
Masquerade
-An unauthorized entity gains access to a system or performs a malicious act by posing as an authorized entity Falsification -False data deceive an authorized entity Repudiation -An entity deceives another by falsely denying responsibility for an act. |
|
|
Disruption
|
A circumstance or event that interrupts or prevents the correct operation of system services and functions.
|
|
|
Disruption Threat Action
|
Incapacitation
Corruption Obstruction |
|
|
Usurpation
|
A circumstance or event that results in control of system services or functions by an unauthorized entity.
|
|
|
Usurpation Threat Action
|
Misappropriation
-An entity assumes unauthorized logical or physical control of a system resource Misuse -Causes a system component to perform a function or service that is detrimental to system security. |
|
|
Passive Attack
|
The nature of eavesdropping on, or monitoring of, transmissions.
The goal of the attacker is to obtain info that is being transmitted, resulting in the release of message contents or traffic analysis. |
|
|
Active Attacks
|
involve some modification of the data stream or the creation of a false stream and can be subdivided into four categories:
Replay Masquerade Modification of messages Denial of service |
|
|
Balance between security and IT/business function
|
• Ease of use versus security: Virtually all security measures involve some pen- alty in the area of ease of use. The following are some examples. Access control mechanisms require users to remember passwords and perhaps perform other access control actions. Firewalls and other network security measures may reduce available transmission capacity or slow response time. Virus-checking software reduces available processing power and introduces the possibility of system crashes or malfunctions due to improper interaction between the secu- rity software and the operating system.
• Cost of security versus cost of failure and recovery: In addition to ease of use and performance costs, there are direct monetary costs in implementing and maintaining security measures. All of these costs must be balanced against the cost of security failure and recovery if certain security measures are lacking. The cost of security failure and recovery must take into account not only the value of the assets being protected and the damages resulting from a security violation, but also the risk, which is the probability that a particular threat will exploit a particular vulnerability with a particular harmful result. |
|
|
Symmetric Encryption (SE)
|
Conventional Encryption
Single-Key Encryption Only type of encryption in use prior to the introduction of public-key encryption in the late 1970s |
|
|
5 Ingredients of SE
|
Plaintext
Encryption Algorithm Secret Key Ciphertext Decryption Algorithm |
|
|
Plaintext
|
This is the original message or data that is fed into the algorithm as input
|
|
|
Encryption algorithm
|
The encryption algorithm performs various substitutions and transformations on the plaintexts
|
|
|
Secret Key
|
The secret key is also input into the encryption algorithm. The exact substitutions and transformations performed by the algorithms depend on the key.
|
|
|
Ciphertext
|
This is the scrambled message produced as output. It depends on the plaintext and the secret key. For a given message, two different keys will produce two different ciphertexts.
|
|
|
Decryption Algorithm
|
This is essentially the encryption algorithm run in reverse. It takes the ciphertext and the secret key and produces the original plaintext.
|
|
|
Methods of SE Attack
|
Cryptanalysis
Brute-force Attack |
|
|
Cryptanalysis
|
Rely on the nature of the algorithm plus perhaps some knowledge of the general characteristics of the plaintext or even some plaintext-ciphertext pairs.
|
|
|
Brute-Force Attack
|
Try to every possible key on a piece of ciphertext until an intelligible translation into plaintext is obtained.
|
|
|
Relationship between Key length and Computing.
|
The first concern refers to the possibility that cryptanalysis is possible by exploiting the characteristics of the DES algorithm. Over the years, there have been numerous attempts to find and exploit weaknesses in the algorithm, making DES the most-studied encryption algorithm in existence. Despite numerous approaches, no one has so far reported a fatal weakness in DES.
With a key length of 56 bits, there are 2^56 possible keys, which is approximately 7.2x10^16 keys. Thus, on the face of it, a brute- force attack appears impractical. Assuming that, on average, half the key space has to be searched, a single machine performing one DES encryption per microsecond would take more than a thousand years to break the cipher. Add more machines, it gets faster until its possible in seconds. |
|
|
Data Encryption Standard
|
DES
Most widely used encryption scheme that was adopted in 1977 by the National Bureau of Standards, now the National Institute of Standards and Technology (NIST) Takes a plaintext block of 64 bits and a key of 56 bits, to produce a ciphertext block of 64 bits. |
|
|
Advanced Encrytion Standard
|
AES
|
|
|
Triple DES
|
3DES
Repeats the basic DES algorithm three times, using either two or three unique keys, for a key size of 112 or 168 bits. Standardized for use in financial applications an ANSI and standard X9.17 in 1985. Usually sluggish in software Not a reasonable capable |
|
|
Block Cipher
|
A block cipher processes the input one block of elements at a time, producing an output block for each input block.
More common |
|
|
Stream Cipher
|
A stream cipher processes the input elements continuously, producing output one element at a time, as it goes along.
Less common but sometimes more suitable to the circumstance. |
|
|
MAC
|
Message Authentication Key
The use of a secret key to generate a small block of data that is appended to the message The message plus code are transmitted to the intended recipient. The recipient performs the same calculation on the received message, using the same secret key, to generate a new message authentication code. The received code is compared to the calculated code. If we assume that only the receiver and the sender know the identity of the secret key, and if the received code matches the calculated code, then the receiver is assured the message has not been altered and is from the alleged sender. |
|
|
One-way Hash Function
|
A hash function accepts a variable-size message M as input and produces a fixed-size message digest H(M) as output.
A hash function does not also take a secret key as input. |
|
|
Public Key
|
Public-key encryption, first publicly proposed by Diffie and Hellman in 1976, is the first truly revolutionary advance in encryption in literally thousands of years.
Public-key algorithms are based on mathematical functions rather than on simple operations on bit patterns, such as are used in symmetric encryption algorithms. |
|
|
Private Key
|
As the names suggest, the public key of the pair is made public for others to use, while the private key is known only to its owner
|
|
|
Random Numbers
|
Traditionally, the concern in the generation of a sequence of allegedly random numbers has been that the sequence of numbers be random in some well-defined statistical sense. The following two criteria are used to validate that a sequence of numbers is random:
• Uniform distribution: The distribution of numbers in the sequence should be uniform; that is, the frequency of occurrence of each of the numbers should be approximately the same. • Independence:No one value in the sequence can be inferred from the others. |
|
|
Pseudorandom Numbers
|
If the algorithm is good, the resulting sequences will pass many reasonable tests of randomness.
|
|
|
Process of Authentication
|
Identification step: Presenting an identifier to the security system. (Identifiers should be assigned carefully, because authenticated identities are the basis for other security services, such as access control service.)
Verification step: Presenting or generating authentication information that corroborates the binding between the entity and the identifier. |
|
|
User Authentication
|
Something the individual knows:
Something the individual possesses: Something the individual is (static biometrics): Something the individual does (dynamic biometrics): |
|
|
Password-based Authentication
|
Virtually all multiuser systems, network-based servers, Web-based e-commerce sites, and other similar services require that a user provide not only a name or identifier (ID) but also a password
|
|
|
Password Vulnerabilities
|
Offline Dictionary Attack
Specific Account Attack Popular password Attack Password Guessing against Single User Workstation Hijacking Exploiting User Mistakes Exploiting multiple password use Electronic Monitoring |
|
|
Unix
|
Operating system
Uses hashed passwords Something about salt scheme Unix (officially trademarked as UNIX) is a multitasking, multi-user computer operating system that exists in many variants |
|
|
OpenBSD,
|
A widely used open source UNIX with the most secure version of the UNIX hash/salt scheme that was developed
|
|
|
Password Length/Complexity
|
The first concern refers to the possibility that cryptanalysis is possible by exploiting the characteristics of the DES algorithm. Over the years, there have been numerous attempts to find and exploit weaknesses in the algorithm, making DES the most-studied encryption algorithm in existence. Despite numerous approaches, no one has so far reported a fatal weakness in DES.
With a key length of 56 bits, there are 2^56 possible keys, which is approximately 7.2x10^16 keys. Thus, on the face of it, a brute- force attack appears impractical. Assuming that, on average, half the key space has to be searched, a single machine performing one DES encryption per microsecond would take more than a thousand years to break the cipher. Add more machines, it gets faster until its possible in seconds. |
|
|
Controlling access to password file
|
The hashed passwords are kept in a separate file from the user IDs, referred to as a shadow password file
|
|
|
Pro-active password checking
|
In this scheme, a user is allowed to select his or her own password. How- ever, at the time of selection, the system checks to see if the password is allowable and, if not, rejects it. Such checkers are based on the philosophy that, with suffi- cient guidance from the system, users can select memorable passwords from a fairly large password space that are not likely to be guessed in a dictionary attack.
|
|
|
Smart Cards
|
• Physical characteristics: Smart tokens include an embedded microprocessor. A smart token that looks like a bank card is called a smart card. Other smart tokens can look like calculators, keys, or other small portable objects.
• Interface: Manual interfaces include a keypad and display for human/token interaction. Smart tokens with an electronic interface communicate with a compatible reader/writer. |
|
|
Memory Cards
|
Memory cards can store but not process data. The most common such card is the bank card with a magnetic stripe on the back. A magnetic stripe can store only a simple security code, which can be read (and unfortunately reprogrammed) by an inexpensive card reader. There are also memory cards that include an internal electronic memory.
(Example: Hotel Key) |
|
|
Biometric Physical Characteristics Used
|
Facial Characteristics
Fingerprints Hand Geometry Retinal Pattern Iris Signature Voice Ears* |
|
|
Biometrics Function
|
Hard to fake
Used for Verification or identification |
|
|
Biometrics Accuracy
|
High accuracy, especially when user also has a PIN #
|
|
|
RFC 2828
|
Measures that implement and assure security services in a computer system, particularly those that assure access control service
|
|
|
DAC
|
Discretionary Access Control
Controls access based on the identity of the requestor and on access rules (authorizations) stating what requestors are (or are not) allowed to do. This policy is termed discretionary because an entity might have access rights that permit the entity, by its own volition, to enable another entity to access some resource. |
|
|
MAC
|
Mandatory Access Control
Controls access based on comparing security labels (which indicate how sensitive or critical system resources are) with security clearances (which indicate system entities are eligible to access certain resources). This policy is termed mandatory because an entity that has clearance to access a resource may not, just by its own volition, enable another entity to access that resource. |
|
|
RBAC
|
Role-Based Access Control
Controls access based on the roles that users have within the system and on rules stating what accesses are allowed to users in given roles. |
|
|
Access Control Requirements
|
Reliable Input
Support for fine and coarse secifications Least privilege Separation of Duty Open and Closed Policies Policy Combinations and Conflict Resolution Administrative Policies Dual Control |
|
|
Access Control Matrix
|
Processes
Devices Memory Locations or Regions Subjects |
|
|
Benefits of Relational DB for ACL
|
[SAND94] proposes a data structure that is not sparse, like the access matrix, but is more convenient than either ACLs or capability lists (Table 4.1). An autho- rization table contains one row for one access right of one subject to one resource. Sorting or accessing the table by subject is equivalent to a capability list. Sorting or accessing the table by object is equivalent to an ACL. A relational database can easily implement an authorization table of this type.
|
|
|
Access Control System Commands
|
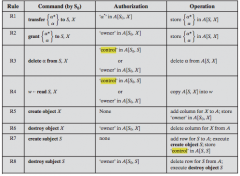
|
|
|
FIPS
|
Federal Information Processing Standards
|
|
|
CIA
|
Confidentiality
Integrity Availability |
|
|
5 Threat Vectors*
|
Direct
Network Virtual PMMD Supply Change |
|
|
Role Heirarchies
|
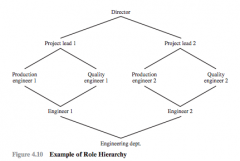
General
Limited |
|
|
General role hierarchies
|
Allow an arbitrary partial ordering of the role hierarchy. In particular, this type supports multiple inheritance, in which a role may inherit permissions from multiple subordinate roles and more than one role can inherit from the same subordinate role.
|
|
|
Limited role hierarchies:
|
Impose restrictions resulting in a simpler tree structure. The limitation is that a role may have one or more immediate ascendants but is restricted to a single immediate descendant.
|
|
|
RBAC
|
Object
Operation Permission |

