![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
30 Cards in this Set
- Front
- Back
|
Application layer
|
Hold network applications and many related protocols (HTTP for requesting and/or transferring files, SMTP for email, FTP for transferring files between two end systems, SSL, etc.) Another key application-layer protocol, DNS (Domain Name System), works to give Internet end systems more user-friendly names.
|
|
|
Transport layer
|
Data transfer between processes. Deliver messages from the application layer to the other endpoint(s). Uses either the TCP (connection-focused) or UDP (bandwidth-focused) protocols.
|
|
|
Network layer
|
Relays datagrams, or network-layer packets, between hosts. Follows the lone IP protocol to ensure that end systems and routers work to receive datagrams. However, also follows many available routing protocols to decide transport paths between sources. Provides logical communication between hosts.
|
|
|
Link layer
|
Helps the network layer transport a packet from one node to the next. These nodes can include hosts or routers, which are where the link layer takes over from the network layer. These different links may follow different protocols (Ethernet, Wifi, etc.)
|
|
|
Physical layer
|
Within the link layer, the physical layer works to deliver each bit of data across the link. Depending on the link, different protocols might come into play.
|
|
|
What are the two key network-layer functions?
(most important in datagram network) |
* Routing: determine route taken by packets from source to destination (like planning a trip from the source to the destination)
* Forwarding: move packets from router’s input to appropriate router output (like the process of getting through a single interchange) |
|
|
Some network architectures have a 3rd important function. What is it?
(this and the other two = the three most important in a virtual-circuit network) |
* Connection setup: before datagrams flow, two end hosts AND intervening routers establish a virtual connection
In network layer: between two hosts (may also include intervening routers) In transport layer: between two processes |
|
|
Network service model
|
service model for a "channel" transporting datagrams from sender to receiver
|
|
|
Example services for individual datagrams
Example services for a flow of datagrams |
individual datagrams: guaranteed delivery, guaranteed delivery with less than 40 msec delay
flow: In-order datagram delivery, guaranteed minimum bandwidth to flow, restrictions on changes in interpacket spacing |
|
|
Describe the forwarding tables for both datagram networks and virtual-circuit networks.
|
Datagram forwarding tables use a routing algorithm and the packet’s destination address to decide the output link.
VC forwarding tables have four sets of data: incoming interface, incoming VC#, outgoing interface, and outgoing VC#. The first two determine the last two. |
|
|
Compare and contrast link-state and distance-vector routing algorithms.
|
Link-state routing uses Djikstra’s algorithm to look at all paths and calculate the least-cost paths from a source to the destination. Distance-vector routing uses dynamic programming in the form of the Bellman-Ford Equation: each node periodically sends a distance vector estimate to each of its neighbors. The equation looks at these distances to determine the least-cost path. A malfunctioning router has a different effect in both algorithms. In link-state routing, an error (particularly a node that gives an incorrect link cost) remains with the node and doesn’t propagate. With distance-vector routing, however, the incorrect information would be passed to other nodes.
|
|
|
Inter-autonomous-system routing
(Inter-AS protocol) |
The (multiple) administrators want to control how exactly traffic is routed and who routes through the network. Policy can even take precedence over performance.
|
|
|
Intra-autonomous-system routing
(Intra-AS protocol) |
Only one administrator, more focused on performance
|
|
|
When a host joins a multicast group, must it change its IP address to that of the multicast group it is joining?
|
No, the host maintains its own IP address.
|
|
|
Suppose that routers were subject to conditions that might cause them to fail fairly often. Would this argue in favor of a VC or a datagram architecture? Why?
|
Datagram, because it has “elastic” service and superior flexibility that would be more accommodating to router failure. Datagram architectures provide a connectionless service.
|
|
|
Suppose that a source node and a destination require that a fixed amount of capacity always be available at all routers on the path between the source and destination node, for the exclusive use of traffic flowing between this source and destination node. Would this argue in favor of a VC or a datagram architecture? Why?
|
VC, because it allows stricter requirements than datagram architecture. VC architectures provide a connection-focused service that allows the fixed capacity described above.
|
|
|
Suppose that the links and routers in the network never fail and that routing paths used between all source/destination pairs remains constant. In this scenario, does a VC or datagram architecture have more control traffic overhead? Why?
|
Datagram architecture will have more traffic overhead because packets between the same source and destination may take different paths. VC architecture will be more consistent: its connection-based architecture will produce no overhead in this kind of scenario.
|
|
|
How big is the MAC address space? The IPv4 address space? The IPv6 address space?
|
MAC: 6 bytes / 48 bits
IPv4: 32 bits IPv6: 128 bits |
|
|
Virtual circuits
|
“source-to-dest path behaves much like
telephone circuit” performance-wise network actions along source-to-dest path call setup, teardown for each call before data can flow each packet carries VC identifier (not destination host address) every router on source-dest path maintains “state” for each passing connection link, router resources (bandwidth, buffers) may be allocated to VC (dedicated resources = predictable service) |
|
|
Virtual circuit implementation
a VC consists of 3 things: |
1. path from source to destination
2. VC numbers, one number for each link along path 3. entries in forwarding tables in routers along path |
|
|
Datagram vs VC end systems
|
VC: “dumb” end systems
Datagram: “smart” end systems (computers) can adapt, perform control, error recovery simple inside network, complexity at “edge” many link types different characteristics uniform service difficult |
|
|
Two key router functions
|
1) run routing algorithms/protocol (RIP, OSPF, BGP)
2) forward datagrams from incoming to outgoing link |
|
|
switching rate
|
rate at which packets can transfer from inputs to outputs
often measured as multiple of input/output line rate N inputs: switching rate N times line rate desirable |
|
|
Three types of switching fabrics
|
Switching Via Memory - first generation routers. traditional computers with switching under
direct control of CPU Switching Via a Bus - datagram from input port memory Switching Via An Interconnection Network - overcome bus bandwidth limitations |
|
|
Head-of-the-Line (HOL) blocking
|
queued
datagram at front of queue prevents others in queue from moving forward |
|
|
An IP address is a 32-bit identifier for...
|
a host and the router interface
subnet part = high order bits host part = low order bits |
|
|
Subnet
|
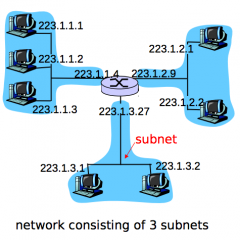
device interfaces with same subnet part of IP address
can physically reach each other without intervening router |
|
|
CIDR
|
CIDR: Classless InterDomain Routing
subnet portion of address of arbitrary length address format: a.b.c.d/x, where x is # bits in subnet portion of address |
|
|
DHCP
|
Dynamic Host Configuration Protocol
dynamically get address from a server “plug-and-play” can return more than just address |
|
|
address format: a.b.c.d/x, where x is
|
# of bits in
subnet portion of address |

