![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
10 Cards in this Set
- Front
- Back
- 3rd side (hint)
|
What are three fundamental approaches to proof of possession of secret?
|
One-time password, encryption (symmetric secret or public key), or hashing (message authentication code).
|
|
|
|
The hash mechanism that provides integrity.
|
Message Authentication Code (MAC) and Message Integrity Code (MIC)
|
|
|
|
What is the pseudocode for a MAC?
|
Msg, nonce, hash(PW , Msg , nonce)
|
|
|
|
Can you use an encryption function as a hashing function?
|
Yes, but you must throw something away.
|
|
|
|
What is the probability of a hash collision of message M2 with message M1 using an n bit hash?
|
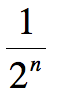
1 / (2^n)
|
|
|
|
How many messages would have to be generated to raise the probability of a hash between any two to ~50%?
|
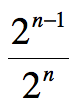
2^(n-1) / 2^n
|
|
|
|
[Cryptool] Look at the “grids” representing a plaintext block and the cipher key. How many bits comprise an AES block?
|
16 blocks * 2 hex chars * 4 bits per hex char = 128
|
|
|
|
[Cryptool] How many total AES rounds are there per plaintext block?
|
10
|
(Note: In class lecture I refer to this concept more generally as iterations. This may be a bit confusing as the presentation confuses the issue a bit. Specifically, do we count the initial round or not? The answer is no, they don’t count the initial round in the total number of rounds.)
|
|
|
[Cryptool] What does the ‘S’ in “S-Box” stand for?
|
Substitution
|
(Note: you find the same kind of thing in the DES algorithm, and others)
|
|
|
[Cryptool] What is the primary source of obscuring the relationship between columns and rows in Rijndael?
|
diffusion
|
|

