![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
316 Cards in this Set
- Front
- Back
|
architecture |
is a tool used to conceptually understand the structure and behavior of a complex entity through different views. |
|
|
architecture description |
is a formal description and representation of a system, the components that make it up, the interactions and interdependencies between those components, and the relationship to theenvironment. An architecture provides different views of the system, based upon the needs of the stakeholders of that system. |
|
|
system architecture |
describes the major components of the system and how they interact with each other, with the users,and with other systems. An architecture is at the highest level when it comes to the overall process of system development. |
|
|
development |
refers to the entire lifecycle of a system, including the planning, analysis, design, building, testing,deployment, maintenance, and retirement phases. |
|
|
ISO/IEC/IEEE 42010 |
Systems and software engineering—Architecture description. The standard is evolving and being improved upon. The goal is to internationally standardize how system architecture takes place so that product developers aren’t just “winging it”and coming up with their own proprietary approaches. A disciplined approach tosystem architecture allows for better quality, interoperability, extensibility,portability, and security. is to establish a shared vocabulary among all the stakeholders. |
|
|
Stakeholder |
Individual,team, or organization (or classes thereof) with interests in, or concerns relative to, a system. |
|
|
View |
Representation of a whole system from the perspective of a related set of concerns. |
|
|
Viewpoint |
A specification of the conventions for constructing and using a view. A template from which to develop individual views by establishing the purposes and audience for a view and the techniques for its creation and analysis. |
|
|
COMPUTER ARCHITECTURE |
encompasses all of the parts of a computer system that are necessary for it to function, including the central processing unit, memory chips, logic circuits, storage devices, input and output devices, security components, buses, and networking interfaces. |
|
|
Central Processing Unit (CPU) |
is the brain of a computer.In the most general description possible, it fetches instructions from memory and executes them. Although a CPU is a piece of hardware, it has its own instruction set that is necessary to carry out its tasks. |
|
|
arithmetic logic unit (ALU) |
performs mathematical functions and logical operations on data. The ALU can be thought of as the brain of the CPU, and the CPU as the brain of the computer. |
|
|
When an action needs to take place on the data, the instructions and data memory addresses are passed to.... |
the CPU registers |
|
|
Control Unit |
Dicdates when data is processed by the system's processor |
|
|
General registers |
are used to hold variables and temporary results as the ALU works through its execution steps. The general registers are like the ALU’s scratch pad, which it uses while working. |
|
|
Special registers |
(dedicated registers) hold information such as the program counter, stack pointer, and program status word(PSW). |
|
|
program counter register |
contains the memory address of the next instruction to be fetched. |
|
|
address bus |
is a hard wired connection to the RAM chips in the system and the individual input/output (I/O) devices. |
|
|
fetch request |
The fetch request contains the address of where the needed data is located. |
|
|
Random Access Memory (RAM) |
is a type of temporary storage facility where data and program instructions can temporarily be held and altered. It is used for read/write activities by the operating system and applications. It is described as volatile because if the computer’s power supply is terminated, then all information within this type of memory is lost. |
|
|
Synchronous DRAM (SDRAM) |
Synchronizes itself with the system’s CPU and synchronizes signal input and output on the RAM chip. It coordinates its activities with the CPU clock so the timing of the CPU and the timing of the memory activities are synchronized. This increases the speed of transmitting and executing data. |
|
|
Extended data out DRAM (EDODRAM) |
This is faster than DRAM because DRAM can access only one block of data at a time, where as EDO DRAM can capture the next block of data while the first block is being sent to the CPUfor processing. It has a type of “look ahead” feature that speeds up memory access. |
|
|
Burst EDO DRAM (BEDO DRAM) |
Works like (and builds upon) EDO DRAM in that it can transmit data to the CPU as it carries out a read option, but it can send more data at once (burst). It readsand sends up to four memory addresses in a small number of clock cycles. |
|
|
Double data rate SDRAM (DDRSDRAM) |
Carries out read operations on the rising and falling cycles of a clock pulse. So instead of carrying outone operation per clock cycle, it carries out two and thus can deliver twice the throughput of SDRAM. Basically, it doubles the speed of memory activities,when compared to SDRAM, with a smaller number of clock cycles. |
|
|
Read-Only Memory (ROM) |
is a nonvolatile memory type, meaning that when a computer’s poweris turned off, the data is still held within the memory chips. When data is written into ROM memory chips, the data cannot be altered. Individual ROM chips are manufactured with the stored program or routines designed into it. |
|
|
Programmable read-onlymemory (PROM) |
is a form of ROM that canbe modified after it has been manufactured. PROM can be programmed only one time because the voltage that is used to write bits into the memory cells actually burns out the fuses that connect the individual memory cells. |
|
|
Erasable programmableread-only memory (EPROM) |
can be erased, modified, and upgraded. EPROM holds data that can be electrically erased or written to.To erase the data on the memory chip, you need your handy-dandy ultraviolet(UV) light device that provides just the right level of energy. |
|
|
Flash memory |
is a special type of memory that is used in digital cameras, BIOS chips, memory cards, and video game consoles. It is a solid-state technology, meaning it does not have moving parts and is used more as a type of hard drive than memory. basically moves around different levels of voltages to indicate that a 1 or 0 must be held in aspecific address. |
|
|
Cache Memory |
is a type of memory used for high-speed writing and reading activities. When the system assumes (through its programmatic logic) that it will need to access specific information many times throughout its processing activities, it will store the information in cache memory so it is easily and quickly accessible. |
|
|
absolute addresses |
The physical memory addresses that the CPU uses |
|
|
logical addresses |
The indexed memory addresses that software uses |
|
|
relative addresses |
are based on a known address with an off set value applied. |
|
|
buffer |
is an allocated segment of memory. |
|
|
buffer overflow |
takes place when too much data is accepted as input to a specific process. A buffer can be overflowed arbitrarily with too much data, but for it to be of any use to an attacker, the code inserted into the buffer must be of a specific length, followed up by commands the attacker wants executed. |
|
|
data execution prevention(DEP) |
to help ensure that executable code does not function within memory segments that could be dangerous. |
|
|
garbage collector |
software that runs analgorithm to identify unused committed memory and then tells the operating system to mark that memory as “available. |
|
|
memory leak |
In computer science, a memory leak is a type of resource leak that occurs when a computer program incorrectly manages memory allocations[1] in such a way that memory which is no longer needed is not released. |
|
|
multiprogramming |
which means that more than one program (or process) can be loaded into memory at the same time. This is what allows you to run your antivirus software, word processor, personalfirewall, and e-mail client all at the same time. |
|
|
multitasking |
which means more than one application can be in memory at the same time andthe operating system can deal with requests from these different applications simultaneously |
|
|
A process |
The collection ofthe instructions and the assigned resources |
|
|
instructions |
They are static lines of code that are brought to life when they are initialized and put into memory. |
|
|
Cooperative multitasking |
used in Windows 3.x andearly Macintosh systems, required the processes to voluntarily release resources they were using. This was not necessarily a stable environment because if a programmer did not write his code properly to release a resource when his application was done using it, the resource would be committed indefinitely to his application and thus be unavailable to other processes. |
|
|
preemptive multitasking |
, used in Windows 9x and later versions and in Unix systems, the operating system controls how long a process can use a resource. The system can suspend a process that is using the CPU and allow another process access to it through the use of time sharing. Soin operating systems that used cooperative multitasking, the processes had too much control over resource release, and when an application hung, it usually affected all the other applications and sometimes the operating system itself. |
|
|
process in running state |
(CPU is executing its instructions and data) |
|
|
Process in ready state |
waiting to send instructions to the CPU |
|
|
Process in blocked state |
waiting for input data,such as keystrokes, from a user |
|
|
How does a process knowwhen it can communicate with the CPU? |
This is taken care of byusing interrupts |
|
|
thread |
is made up of an individual instruction set and the data that must be worked on by the CPU. |
|
|
multi-threaded |
A program that has been developed to carry out several different tasks at one time (display, print, interact with other programs) is capable of running several different threads simultaneously. |
|
|
Process isolation |
is a set of different hardware and software technologies[1] designed to protect each process from other processes on the operating system. It does so by preventing process A from writing to process B.is necessary to ensure that processes do not “step on each other’s toes,” communicate in an insecure manner, or negatively affect each other’s productivity. |
|
|
Different methods can beused to enforce process isolation: |
• Encapsulationof objects • Time multiplexing of shared resources • Naming distinctions • Virtual memory mapping |
|
|
When a process is encapsulated |
no other process understands or interacts with its internal programming code. When process Aneeds to communicate with process B, process A just needs to know how to communicate with process B’s interface |
|
|
data hiding |
which means that outside software components will not know how a process works and willnot be able to manipulate the process’s internal code. This is an integrity mechanism and enforces modularity in programming code. |
|
|
Time multiplexing |
is a technology that allows processes to use the same resources. means there are several data sources and the individual data pieces are piped into one communication channel |
|
|
Naming distinctions |
means that the differentprocesses have their own name or identification value. |
|
|
Virtual address memorymapping |
It maps memory addresses used by a program, called virtual addresses, into physical addresses in computer memory. |
|
|
The goals of memorymanagement |
• Providean abstraction level for programmers • Maximizeperformance with the limited amount of memory available • Protect the operating system and applications loaded into memory |
|
|
Abstraction |
means that the details of something are hidden. Developers of applications do not know the amount or typeof memory that will be available in each and every system their code will beloaded on |
|
|
memory manager |
The portion of the operating system that keeps track of how these different types of memory areused is lovingly. Its jobs are to allocate and deallocate different memory segments, enforce access control to ensure processes are interacting only with their own memory segments, and swap memory contents from RAM to the hard drive. |
|
|
Thememory manager has five basic responsibilities |
Relocation Protection Sharing Logical organization Physical organization |
|
|
Relocation |
• Swap contents from RAM to the hard drive as needed (explained later in the “VirtualMemory” section of this chapter) • Provide pointers for applications if their instructions and memory segment have been moved to a different location in main memory |
|
|
Protection: |
• Limit processes to interact only with the memory segments assigned to them • Provide access control to memory segments |
|
|
Sharing |
• Use complex controls to ensure integrity and confidentiality when processes need touse the same shared memory segments • Allow many users with different levels of access to interact with the same application running in one memory segment |
|
|
Logical organization |
• Segmentall memory types and provide an addressing scheme for each at an abstraction level • Allow for the sharing of specific software modules, such as dynamic link library(DLL) procedures |
|
|
Physical organization |
• Segment the physical memory space for application and operating system processes |
|
|
dynamic link library (DLL) |
is a set of functions that applications can call upon to carry out different types of procedures. |
|
|
How can an operating systemmake sure a process only interacts with its memory segment? |
When a process creates athread because it needs some instructions and data processed, the CPU uses two registers. |
|
|
A base register |
contains the beginnin gaddress that was assigned to the process |
|
|
limit register |
contains the ending address that was assigned to the process |
|
|
Memory Protection Issues |
• Every address reference is validated for protection. • Two or more processes can share access to the same segment with potentiallydifferent access rights. • Different instruction and data types can be assigned different levels of protection.• Processes cannot generate an unpermitted address or gain access to an unpermitted segment |
|
|
Secondary storage |
is considered nonvolatile storage media and includes such things as the computer’s hard drive, USB drives, and optical discs |
|
|
virtual memory |
When RAM and secondary storage are combined. The system uses hard drive space to extend its RAM memory space. Swap space is the reserved hard drive space used to extend RAM capabilities. Windows systems use the pagefile.sys file to reserve this space |
|
|
virtual memory paging. |
When a program requests access to this data, it is brought from the hard drive back into memory inspecific units, called pages |
|
|
Input/Output Device Management |
We have covered a lot of operating system responsibilities up to now, and we arenot stopping yet. An operating system also has to control all input/outputdevices. It sends commands to them, accepts their interrupts when they need to communicate with the CPU, and provides an interface between the devices and the applications |
|
|
Operating systems can carryout software I/O procedures in various ways. |
• ProgrammedI/O • Interrupt-drivenI/O • I/Ousing DMA • PremappedI/O • Fullymapped I/Oetur+2C3 |
|
|
rogrammable I/O |
means the CPU sends data toan I/O device and polls the device to see if it is ready to accept more data.If the device is not ready to accept more data, the CPU wastes time by waiting for the device to become ready. |
|
|
Interrupt-Driven I/O |
means the CPU sends acharacter over to the printer and then goes and works on another process’srequest. |
|
|
I/O Using DMA |
Direct memory access (DMA) is a way of transferring data between I/O devices and the system’s memory without using the CPU. This speeds up data transfer rates significantly. When used in I/O activities, the DMA controllerfeeds the characters to the printer without bothering the CPU. This method is sometimes referred to as unmapped I/O. |
|
|
Premapped I/O |
, the CPU sends thephysical memory address of the requesting process to the I/O device, and theI/O device is trusted enough to interact with the contents of memory directly,so the CPU does not control the interactions between the I/O device and memory.The operating system trusts the device to behave properly |
|
|
Fully Mapped I/O |
the operating system does not trust the I/O device.The physical address is not given to the I/O device. Instead, the device workspurely with logical addresses and works on behalf (under the security context) of the requesting process, so the operating system does not trust the device to interact with memory directly. The operating system does not trust the processor device, and it acts as the broker to control how they communicate with each other. |
|
|
data hiding |
, which means that instructions and data (packaged up as procedures) at the various layers do not have direct access to the instructions and data at any other layers. Eachprocedure at each layer has access only to its own data and a set of functions that it requires to carry out its own tasks. trust |
|
|
The basic core definitions of the different architecture types are |
• Monolithic All operating system processes run in kernel mode. • Layered All operating system processes run in a hierarchical model in kernel mode.• Microkernel Core operating system processes run in kernel mode and the remaining ones run in user mode. • Hybrid microkernel All operating system processes run in kernel mode. Core processes run within a microkernel and others run in a client\server model. |
|
|
security policy |
is a strategic tool thatdictates how sensitive information and resources are to be managed andprotected. A security policy expresses exactly what the security level shouldbe by setting the goals of what the security mechanisms are supposed toaccomplish. |
|
|
The trustedcomputing base (TCB) |
is a collection of all thehardware, software, and firmware components within a system that provides sometype of security and enforces the system’s security policy. The TCB does notaddress only operating system components, because a computersystem is not made up of only an operating system. |
|
|
trusted path |
is a communication channelbetween the user, or program, and the TCB. |
|
|
trusted shell |
meansthat someone who is working in that shell (command interpreter) cannot “bustout of it” and other processes cannot “bust into it.” |
|
|
execution domain |
This means they reside inring 0, their instructions are executed in privileged state, and no lesstrusted processes can directly interact with them. |
|
|
security perimeter |
isa boundary that divides the trusted from the untrusted. For the system to stayin a secure and trusted state, precise communication standards must bedeveloped to ensure that when a component within the TCB needs to communicatewith a component outside the TCB, the communication cannot expose the system tounexpected security compromises. This type of communication is handled andcontrolled through interfaces. |
|
|
Reference Monitor |
is an abstract machine thatmediates all access subjects have to objects, both to ensure that the subjectshave the necessary access rights and to protect the objects from unauthorizedaccess and destructive modification. provides direction on howall access control decisions should be made and controlled in a central,concerted manner within a system. |
|
|
Security Kernel |
is made up of hardware,software, and firmware components that fall within the TCB, and it implementsand enforces the reference monitor concept. The security kernel mediates allaccess and functions between subjects and objects. The security kernel is thecore of the TCB and is the most commonly used approach to building trustedcomputing systems. |
|
|
Thesecurity kernel has three main requirements: |
• Itmust provide isolation for the processes carrying out the reference monitorconcept, and the processes must be tamperproof. • Itmust be invoked for every access attempt and must be impossible to circumvent.Thus, the security kernel must be implemented in a complete and foolproof way. • Itmust be small enough to be tested and verified in a complete and comprehensivemanner. |
|
|
multilevel securitypolicies |
Security policies thatprevent information from flowing from a high security level to a lower securitylevel |
|
|
SECURITY MODELS |
maps the abstract goals ofthe policy to information system terms by specifying explicit data structuresand techniques necessary to enforce the security policy. A security model isusually represented in mathematics and analytical ideas, which are mapped tosystem specifications and then developed by programmers through programmingcode. |
|
|
Bell-LaPadula Model |
is a state machine model used for enforcing access control in government and military applications. Enforces the confidentiality. Simple Security Propert (no read-up), Star-property (no write-down) |
|
|
Limitations Of Bell-LaPadula Model |
* Only addresses confidentiality, control of writing (one form of integrity), *-property and discretionary access control * Covert channels are mentioned but are not addressed comprehensively * The tranquility principle limits its applicability to systems where security levels do not change dynamically. It allows controlled copying from high to low via trusted subjects. *The state-transition model does not contain any state invariants. *The overall process may take more time. |
|
|
Biba Model |
is a formal state transition system of computer security policy that describes a set of access control rules designed to ensure data integrity. Data and subjects are grouped into ordered levels of integrity. The model is designed so that subjects may not corrupt objects in a level ranked higher than the subject, or be corrupted by objects from a lower level than the subject. Simple Integrity - (no read down), The * (star) Integrity - (no write up) |
|
|
Clark-Wilson Model |
The model is primarily concerned with formalizing the notion of information integrity. Information integrity is maintained by preventing corruption of data items in a system due to either error or malicious intent. An integrity policy describes how the data items in the system should be kept valid from one state of the system to the next and specifies the capabilities of various principals in the system. The model defines enforcement rules and certification rules. A distinctive feature ofthe Clark-Wilson model is that it focuses on well-formed transactions and separation of duties.A well-formed transaction is a series of operations thattransform a data item from one consistent state to another. |
|
|
Clark-Wilson Model uses the following elements: |
• Users Activeagents • Transformationprocedures (TPs) Programmed abstract operations,such as read, write, and modify • Constraineddata items (CDIs) Can be manipulated only by TPs • Unconstraineddata items (UDIs) Can be manipulated by users viaprimitive read and write operations • Integrityverification procedures (IVPs) Check the consistencyof CDIs with external reality |
|
|
Noninterference Model |
This concept is implemented to ensure any actions that take place at a higher security level do not affect,or interfere with, actions that take place at a lower level. In simple terms, a computer is modeled as a machine with inputs and outputs. Inputs and outputs are classified as either low (low sensitivity, not highly classified) or high (sensitive, not to be viewed by uncleared individuals). A computer has the non-interference property if and only if any sequence of low inputs will produce the same low outputs, regardless of what the high level inputs are.That is, if a low (uncleared) user is working on the machine, it will respond in exactly the same manner (on the low outputs) whether or not a high (cleared) user is working with sensitive data. The low user will not be able to acquire any information about the activities (if any) of the high user. |
|
|
Covert Channels |
A covert channel isa way for an entity to receive information in an unauthorized manner. These communications can be very difficult to detect. Covert channels are of two types: storage and timing. In a covert storage channel, processes are able to communicate through some type of storage space on the system. In a covert timingchannel, one process relays information to another by modulating its use ofsystem resources. |
|
|
INFORMATION FLOW MODEL |
The Information Flow Model describes howinformation may flow in a secure system. Both Bell-LaPadula and Biba use theinformation flow model. Bell-LaPadula states “no read up” and “no write down.”Information flow describes how unclassified data may be read up to secret, forexample, and then written up to top secret. Biba reverses the information flowpath to protect integrity. |
|
|
NONINTERFERENCE |
The noninterference model ensures that data atdifferent security domains remain separate from one another. By implementingthis model, the organization can be assured that covert channel communicationdoes not occur because the information cannot cross security boundaries. Eachdata access attempt is independent and has no connection with any other dataaccess attempt. |
|
|
ACCESS CONTROL MATRIX |
An access control matrix is a table that definesaccess permissions between specific subjects and objects. A matrix is a datastructure that acts as a table lookup for the operating system. |
|
|
Brewer and Nash Model |
also called the Chinese Wall model, states that asubject can write to an object if, and only if, the subject cannot read anotherobject that is in a different dataset. Was constructed to provide information security access controls that can change dynamically. This security model, also known as the Chinese wall model, was designed to provide controls that mitigate conflict of interest in commercial organizations. The main goal of the modelis to protect against conflicts of interest by users’ access attempts. |
|
|
Graham-Denning Model |
is a computer security model that shows how subjects and objects should be securely created and deleted. It also addresses how to assign specific access rights. It is mainly used in access control mechanisms for distributed systems. There are three main parts to the model: A set of subjects, a set of objects, and a set of eight rules. A subject may be a process or a user that makes a request to access a resource. An object is the resource that a user or process wants to access. |
|
|
Harrison-Ruzzo-Ullman Model |
is an operating system level computer security model which deals with the integrity of access rights in the system. It is an extension of the Graham-Denning model, based around the idea of a finite set of procedures being available to edit the access rights of a subject on an object . It is named after its three authors, Michael A. Harrison, Walter L. Ruzzo and Jeffrey D. Ullman.[1] |
|
|
Common Criteria |
is a framework within which users specify their security requirements and vendors make claims about how they satisfy those requirements, and independent labs can verify those claims. ISO/IEC 15408 |
|
|
Evaluation Assurance Level (EAL) |
• EAL1 Functionally tested • EAL2 Structurally tested • EAL3 Methodically tested and checked • EAL4 Methodically designed, tested, and reviewed • EAL5 Semi formally designed and tested • EAL6 Semi formally verified design and tested • EAL7 Formally verified design and tested |
|
|
protection profiles |
describes the environmental assumptions, the objectives, and the functional and assurance level expectations. Each relevant threat is listedalong with how it is to be controlled by specific objectives. The protection profile also justifies the assurance level and requirements for the strength of each protection mechanism. |
|
|
Aprotection profile typically contains the following sections: |
• Security problem description Lays out the specific problems(i.e., threats) that any compliant product must address. • Security objectives Lists the functionality (i.e., controls)that compliant products must provide in order to address the security problems. • Security requirements These are very specific requirements for compliant products. They are detailed enough for implementation by system developers, and for evaluation by independent laboratories. |
|
|
Target ofevaluation (TOE) |
Product proposed to provide a needed security solution. |
|
|
Security target |
Vendor’s written explanation of the security functionality and assurance mechanisms that meet the needed security solution—in other words, “This is what our product does and how it does it.” |
|
|
Security functionalrequirements |
Individualsecurity functions that must be provided by a product. |
|
|
Security assurancerequirements |
Measures taken during development and evaluation of the product to assure compliance with the claimed security functionality. |
|
|
Packages—EALs |
Functional and assurance requirements are bundled into packages for reuse. This component describes whatmust be met to achieve specific EAL ratings |
|
|
ISO/IEC 15408 |
is the international standard that is used as the basis for the evaluation of security properties ofproducts under the CC framework. |
|
|
Certification |
is the comprehensive technical evaluation of the security components and their compliance for the purposeof accreditation. A certification process may use safeguard evaluation, riskanalysis, verification, testing, and auditing techniques to assess the appropriateness of a specific system. |
|
|
Accreditation |
is the formal acceptance ofthe adequacy of a system’s overall security and functionality by management.The certification information is presented to management, or the responsiblebody, and it is up to management to ask questions, review the reports andfindings, and decide whether to accept the product and whether any correctiveaction needs to take place. Once satisfied with the system’s overall securityas presented, management makes a formal accreditation statement. By doing this,management is stating it understands the level of protection the system will provide in its current environment and understands the security risks associated with installing and maintaining this system. |
|
|
THE RING MODEL |
The ring model is a form of CPUhardware layering that separates and protects domains (such as kernel mode anduser mode) from each other. Many CPUs, such as the Intel ×86 family, have fourrings, ranging from ring 0 (kernel) to ring 3 (user) |
|
|
SECURITY DOMAINS |
A security domain is the list ofobjects a subject is allowed to access. More broadly defined, domains aregroups of subjects and objects with similar security requirements.Confidential, Secret, and Top Secret are three security domains used by theU.S. Department of Defense (DoD), for example. With respect to kernels, twodomains are user mode and kernel mode. |
|
|
Kernel mode |
is where the kernel lives, allowing low-levelaccess tomemory, CPU, disk, etc. It is the most trusted andpowerful part of the system |
|
|
User mode |
is where user accounts and their processes live. |
|
|
Open Systems |
Systems described as open are built up on standards, protocols, and interfaces that have published specifications. This type of architecture provides interoperability between products created by different vendors. |
|
|
Closed Systems |
Systems referred to as closed use an architecture that does not follow industry standards. Interoperability and standard interfaces are not employed to enable easy communication between different types of systems and add-on features. Closed systems are proprietary, meaning the system can only communicate with like systems. |
|
|
distributed system |
isa system in which multiple computing nodes, interconnected by a network,exchange information for the accomplishment of collective tasks. |
|
|
Cloud computing |
is the use of shared,remote computing devices for the purpose of providing improved efficiencies,performance, reliability, scalability, and security. |
|
|
Software as a Service(SaaS) |
Theuser of SaaS is allowed to use a specific application that executes on the service provider’s environment. An example of this would be subscribing to a word processing application that you would then access via a web interface. |
|
|
Platform as a Service(PaaS) |
In this model, the user gets access to a computing platform that is typically built on a server operating system. An example of this would be spawning an instance of Windows Server 2012R2 to provide a web server. The service provider is normally responsible for configuring and securing the platform, however, so the user normally doesn’t get administrative privileges over the entire platform. |
|
|
Infrastructure as a Service(IaaS) |
If you want full, unfettered access to (and responsibility for securing) the clouddevices, you would need to subscribe under an IaaS model. Following up on theprevious example, this would allow you to manage the patching of the Window sServer 2012R2 instance. The catch is that the service provider has noresponsibility for security; it’s all on you. |
|
|
Parallel Computing |
is the simultaneous use of multiple computers to solve a specific task by dividing it among the available computers. |
|
|
Instruction-levelparallelism |
allows two or more program instructions to be executed simultaneously |
|
|
Task-level parallelism |
takes place at a higherlevel of abstraction. In it we divide a program into tasks or threads and runeach in parallel. |
|
|
data parallelism |
describes the distributionof data among different nodes that then process it in parallel. It is relatedto task parallelism, but is focused on the data. can leverage the advantagesof cloud computing in that you can easily spin up hundreds of instances ofcomputing nodes only for the specific time you need them in order to processyour data. This provides tremendous capability at a fraction of the cost ofdoing it in house. |
|
|
Aggregation |
Aggregationhappens when a user does not have the clearance or permission to accessspecific information, but she does have the permission to access components ofthis information. is the act of combining informationfrom separate sources. The combination of the data forms new information, whichthe subject does not have the necessary rights to access. The combined informationhas a sensitivity that is greater than that of the individual parts.i |
|
|
inference |
whichis the intended result of aggregation. The inference problem happens when asubject deduces the full story from the pieces he learned of throughaggregation. This is seen when data at a lower security level indirectlyportrays data at a higher level. is the ability to derive informationnot explicitly available. |
|
|
Programmable logiccontrollers (PLCs) |
are computers designed tocontrol electromechanical processes such assembly lines, elevators, rollercoasters, and nuclear centrifuges. The idea is that a PLC can be used in oneapplication today and then easily reprogrammed to control something elsetomorrow. |
|
|
Distributed Control System(DCS) |
isa network of control devices within fairly close proximity that are part of oneor more industrial processes. DCS usage is very common in manufacturing plants,oil refineries, and power plants, and is characterized by decisions being madein a concerted manner, but by different nodes within the system. |
|
|
Time-of-Check/Time-of-Use Attacks (TOC/TOU) |
Specificattacks can take advantage of the way a system processes requests and performstasks. A time-of-check/time-of-use (TOC/TOU) attack deals withthe sequence of steps a system uses to complete a task. This type of attacktakes advantage of the dependency on the timing of events that take place in amultitasking operating system. |
|
|
To avoid TOC/TOU |
itis best if the operating system can apply software locks to the items it willuse when it is carrying out its “checking” tasks. So if a user requests accessto a file, while the system is validating this user’s authorization, it shouldput a software lock on the file being requested. This ensures the file cannotbe deleted and replaced with another file. Applying locks can be carried outeasily on files, but it is more challenging to apply locks to databasecomponents and table entries to provide this type of protection. |
|
|
A race condition |
is when two differentprocesses need to carry out their tasks on one resource |
|
|
Cryptography |
isa method of storing and transmitting data in a form that only those it isintended for can read and process. It is considered a science of protectinginformation by encoding it into an unreadable format. Cryptography is aneffective way of protecting sensitive information as it is stored on media ortransmitted through untrusted network communication paths. |
|
|
Substitution cipher |
is a method of encoding by which units of plaintext are replaced with ciphertext, according to a fixed system; the "units" may be single letters (the most common), pairs of letters, triplets of letters, mixtures of the above, and so forth. The receiver deciphers the text by performing the inverse substitution. |
|
|
Transposition cipher |
In cryptography, a transposition cipher is a method of encryption by which the positions held by units of plaintext (which are commonly characters or groups of characters) are shifted according to a regular system, so that the ciphertext constitutes a permutation of the plaintext. That is, the order of the units is changed (the plaintext is reordered). Mathematically a bijective function is used on the characters' positions to encrypt and an inverse function to decrypt. |
|
|
Polyalphabetic cipher |
A polyalphabetic cipher is any cipher based on substitution, using multiple substitution alphabets. |
|
|
Vigenère cipher |
The Vigenère cipher is a method of encrypting alphabetic text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution. |
|
|
Encryption |
is a method of transforming readable data, called plaintext, into a form that appears to be random and unreadable, which is called ciphertext. |
|
|
PlaintextQ |
is in a form that can be understood either by a person (a document) or by a computer (executable code) |
|
|
Cryptosystem |
is a suite of cryptographic algorithms needed to implement a particular security service, most commonly for achieving confidentiality (encryption) |
|
|
algorithm |
is a self-contained step-by-step set of operations to be performed. Algorithms perform calculation, data processing, and/or automated reasoning tasks. |
|
|
Kerckhoffs’ Principle |
Auguste Kerckhoffs published a paper in 1883 stating that the only secrecy involvedwith a cryptography system should be the key. He claimed that the algorithm should be publicly known. He asserted that if security were based on too many secrets, there would be more vulnerabilities to possibly exploit. |
|
|
The Strength of the Cryptosystem |
The strength ofan encryption method comes from the algorithm, the secrecy of the key, thelength of the key, the initialization vectors, and how they all work togetherwithin the cryptosystem. When strength is discussed in encryption, it refers tohow hard it is to figure out the algorithm or key, whichever is not madepublic. |
|
|
work factor |
whichis an estimate of the effort and resources it would take an attacker topenetrate a cryptosystem. |
|
|
Cryptosystem scan provide the following services: |
• Confidentiality Renders the information unintelligible except by authorized entities.• Integrity Datahas not been altered in an unauthorized manner since it was created,transmitted, or stored.• Authentication Verifiesthe identity of the user or system that created the information.• Authorization Uponproving identity, the individual is then provided with the key or password that will allow access to some resource. • Nonrepudiation Ensures that the sender cannot deny sending the message. |
|
|
One-Time Pad |
isa perfect encryption scheme because it is considered unbreakable if implementedproperly. It was invented by Gilbert Vernam in 1917, so sometimes it isreferred to as the Vernam cipher. |
|
|
XOR |
is an operation that isapplied to 2 bits and is a function commonly used in binary mathematics andencryption methods. When combining the bits, if both values are the same, theresult is 0 (1 XOR 1 = 0). If the bits are different from each other, theresult is 1 (1 XOR 0 = 1). |
|
|
For a one-time pad encryption scheme to be considered unbreakable, each pad in the scheme must be |
• Made up of truly random values • Used only one time • Securely distributed to its destination • Secure dat sender’s and receiver’s sites • At least as long as the message |
|
|
running key cipher |
could use a key that doesnot require an electronic algorithm and bit alterations, but cleverly usescomponents in the physical world around you. For instance, the algorithm couldbe a set of books agreed upon by the sender and receiver. |
|
|
concealment cipher |
also called a null cipher, is a typeof steganography method. |
|
|
Steganography |
is a method of hiding datain another media type so the very existence of the data is concealed. |
|
|
Frequency analysis |
is the study of the frequency of letters or groups of letters in a ciphertext. The method is used as an aid to breaking classical ciphers. |
|
|
Key Derivation Functions(KDFs) |
are used to generate keys that are made up of random values. Different values can be used independently or together as random key material. The algorithm is created to use specifichash, password, and/or salt values, which will go through a certain number ofrounds of mathematical functions dictated by the algorithm. The more roundsthat this keying material goes through, the more assurance and security for the cryptosystem overall. |
|
|
Symmetric Cryptography |
also called secret keys are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. The keys may be identical or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. This requirement that both parties have access to the secret key is one of the main drawbacks of symmetric key encryption |
|
|
The equation used tocalculate the number of symmetric keys needed |
N(N– 1)/2 = number of keys |
|
|
Symmetric Cryptography Strengths: |
• Much faster (less computationally intensive) than asymmetric systems. • Hard to break if using a large key size. |
|
|
Symmetric Cryptography Weaknesses: |
• Requiresa secure mechanism to deliver keys properly. • Eachpair of users needs a unique key, so as the number of individuals increases, sodoes the number of keys, possibly making key management overwhelming. • Provides confidentiality but not authenticity or nonrepudiation. |
|
|
examples of symmetricalgorithms |
• Data Encryption Standard (DES) • Triple-DES(3DES) • Blowfish • International Data Encryption Algorithm (IDEA) • RC4,RC5, and RC6 • Advanced Encryption Standard (AES) |
|
|
Asymmetric Cryptography |
is any cryptographic system that uses pairs of keys: public keys which may be disseminated widely, and private keys which are known only to the owner. This accomplishes two functions: authentication, which is when the public key is used to verify that a holder of the paired private key sent the message, and encryption, whereby only the holder of the paired private key can decrypt the message encrypted with the public key. |
|
|
open message format |
Encrypting data with the sender’s private key |
|
|
Asymmetric Cryptography Strengths: |
• Better key distribution than symmetric systems. • Betterscalability than symmetric systems. • Can provide authentication and nonrepudiation. |
|
|
Asymmetric Cryptography Weaknesses: |
• Works much more slowly than symmetric systems. • Mathematically intensive tasks. |
|
|
Thefollowing are examples of asymmetric key algorithms: |
• Rivest-Shamir-Adleman(RSA) • Ellipticcurve cryptosystem (ECC) • Diffie-Hellman • ElGamal • Digital Signature Algorithm (DSA) |
|
|
DifferencesBetween Symmetric and Asymmetric Systems |
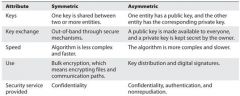
|
|
|
The two main types ofsymmetric algorithms |
Block and Stream Ciphers |
|
|
block cipher |
is used for encryption and decryption purposes, the message is divided into blocks of bits. These blocksare then put through mathematical functions, one block at a time. |
|
|
A strong cipher containsthe right level of two main attributes: |
confusion and diffusion |
|
|
Confusion |
is commonly carried out through substitution. Confusion is provided bycarrying out complex substitution functions so the eavesdropper cannot figure out how to substitute the right values and come up with the original plaintext. |
|
|
diffusion |
is carried out by using transposition. takes place as individual bits of a block are scrambled, or diffused, throughout that block |
|
|
Stream Ciphers |
is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystream, to give a digit of the ciphertext stream. Since encryption of each digit is dependent on the current state of the cipher, it is also known as state cipher. In practice, a digit is typically a bit and the combining operation an exclusive-or (XOR) |
|
|
Stream Ciphers vs. One-Time Pads |
Stream ciphers were developed to provide the same type of protection one-time pads do,which is why they work in such a similar manner. In reality, stream ciphers cannot provide the level of protection one-time pads do, but because stream ciphers are implemented through software and automated means, they are much more practical. |
|
|
Initialization Vectors |
are random values that are used with algorithms to ensure patterns are not created during the encryption process. |
|
|
A strong and effective stream cipher contains the following characteristics: |
• Easy to implement in hardware Complexity in the hardware design makes it more difficult to verify the correctness of the implementation and can slow it down. • Long periods of no repeating patterns within keystream values Bits generated by the keystream are not truly random in most cases, which will eventually lead to the emergence of patterns; we want these patterns to berare. • A key stream not linearly related to the key If someone figures out the keystream values, that does not mean she now knows the key value. • Statisticallyunbiased keystream (as many zeroes as ones) Thereshould be no dominance in the number of zeroes or ones in the keystream. |
|
|
Session Keys |
is a single-use symmetric key that is used to encrypt messages between two users during a communication session. A session key is no different from the symmetric key described in the previous section, but it is only good for one communication session between users. provides more protection than static symmetric keys because it is valid for only one session between two computers. If an attacker were able to capture the session key, she would have a very small window of time to use it to try to decrypt messages being passed back and forth. |
|
|
SymmetricData Encryption Standard(DES) |
Is a symmetric-key algorithm for the encryption of electronic data. Although now considered insecure. DES uses a 64-bit key, but eight of those bits are used for parity checks, effectively limiting the key to 56-bits. Hence, it would take a maximum of 2^56 . DES also uses a key to customize the transformation, so that decryption can supposedly only be performed by those who know the particular key used to encrypt. The Data Encryption Standard is a block cipher, meaning a cryptographic key and algorithm are applied to a block of data simultaneously rather than one bit at a time. |
|
|
DES Modes |
• ElectronicCode Book (ECB) • CipherBlock Chaining (CBC) • CipherFeedback (CFB) • OutputFeedback (OFB) • Counter(CTR) |
|
|
Electronic Code Book (ECB)Mode |
The message is divided into blocks, and each block is encrypted separately. The disadvantage of this method is that identical plaintext blocks are encrypted into identical ciphertext blocks; thus, it does not hide data patterns well. In some senses, it doesn't provide serious message confidentiality, and it is not recommended for use in cryptographic protocols at all. |
|
|
Someimportant characteristics of ECB mode encryption are as follows: |
• Operationscan be run in parallel, which decreases processing time. • Errors are contained. If an error takes place during the encryption process, it only affects one block of data. • Itis only usable for the encryption of short messages. • Itcannot carry out preprocessing functions before receiving plaintext. |
|
|
Cipher Block Chaining (CBC) |
In CBC mode, each block of plaintext is XORed with the previous ciphertext block before being encrypted. This way, each ciphertext block depends on all plaintext blocks processed up to that point. To make each message unique, an initialization vector must be used in the first block. Note that a one-bit change in a plaintext or IV affects all following ciphertext blocks. Decrypting with the incorrect IV causes the first block of plaintext to be corrupt but subsequent plaintext blocks will be correct. If we choose a different IVeach time we encrypt a message, even if it is the same message, the ciphertextwill always be unique. |
|
|
Cipher Feedback (CFB) Mode |
Sometimes block ciphers canemulate a stream cipher, a close relative of CBC, makes a block cipher into a self-synchronizing stream cipher. Operation is very similar; in particular, CFB decryption is almost identical to CBC encryption performed in reverse, is great to use when youneed to send large chunks of data at a time. |
|
|
Output Feedback (OFB) Mode |
makes a block cipher into a synchronous stream cipher. It generates keystream blocks, which are then XORed with the plaintext blocks to get the ciphertext. Just as with other stream ciphers, flipping a bit in the ciphertext produces a flipped bit in the plaintext at the same location. This property allows many error correcting codes to function normally even when applied before encryption. Each output feedback block cipher operation depends on all previous ones, and so cannot be performed in parallel. However, because the plaintext or ciphertext is only used for the final XOR, the block cipher operations may be performed in advance, allowing the final step to be performed in parallel once the plaintext or ciphertext is available. |
|
|
Counter (CTR) Mode |
Counter(CTR) mode is very similar to OFBmode, but instead of using a randomly unique IV value to generate the keystreamvalues, this mode uses an IV counter that increments for each plaintext blockthat needs to be encrypted. The unique counter ensures that each block is XORedwith a unique keystream value.Theother difference is that there is no chaining involved, which means no ciphertext is brought forward to encrypt the next block. Since there is nochaining, the encryption of the individual blocks can happen in parallel, which increases the performance. The main reason CTR mode would be used instead ofthe other modes is performance. |
|
|
Synchronous vs. Asynchronous |
Synchronous cryptosystemsuse keystreams to encrypt plaintext one bit at a time. The keystream values are“in sync” with the plaintext values. An asynchronous cryptosystemuses previously generated output to encrypt the current plaintext values. So astream algorithm would be considered synchronous, while a block algorithm using chaining would be considered asynchronous. |
|
|
SymmetricTriple-DES |
is a symmetric-key block cipher, which applies the Data Encryption Standard (DES) cipher algorithm three times to each data block. 3DESuses 48 rounds in its computation, which makes it highly resistant to differential cryptanalysis. However, because of the extra work 3DES performs,there is a heavy performance hit. It can take up to three times longer than DESto perform encryption and decryption. |
|
|
3DES can work in differentmodes |
• DES-EEE3 Usesthree different keys for encryption, and the data is encrypted, encrypted,encrypted. • DES-EDE3 Usesthree different keys for encryption, and the data is encrypted, decrypted,encrypted. • DES-EEE2 Thesame as DES-EEE3, but uses only two keys, and the first and third encryptionprocesses use the same key. • DES-EDE2 Thesame as DES-EDE3, but uses only two keys, and the first and third encryptionprocesses use the same key. |
|
|
The following fivealgorithms were the finalists of NIST: |
• MARS Developedby the IBM team that created Lucifer • RC6 Developedby RSA Laboratories• Serpent Developedby Ross Anderson, Eli Biham, and Lars Knudsen • Twofish Developedby Counterpane Systems• Rijndael Developedby Joan Daemen and Vincent Rijmen |
|
|
SymmetricAdvanced Encryption Standard |
Also known as Rijndael (its original name), is a specification for the encryption of electronic data established by the (NIST). Rijndaelworks well when implemented in software and hardware in a wide range of products and environments. It has low memory requirements and has been constructed to easily defend against timing attacks. |
|
|
Advanced Encryption Standard key lengths |
128, 192 and 256 bits. |
|
|
AES The number of roundsdepends upon the size of the block and the key length: |
• If both the key and block size are 128 bits, there are 10 rounds. • If both the key and block size are 192 bits, there are 12 rounds. • If both the key and block size are 256 bits, there are 14 rounds. |
|
|
SymmetricInternational DataEncryption Algorithm (IDEA) |
is a block cipher and operates on 64-bit blocks of data. The64-bit data block is divided into 16 smaller blocks, and each has eight rounds of mathematical functions performed on it. The key is 128 bits long, and IDEA is faster than DES when implemented in software. IDEA is used in PGP and other encryption software implementations. |
|
|
Symmetric Blowfish |
is a block cipher that works on 64-bit blocks of data. The key length can be anywhere from 32 bits upto 448 bits, and the data blocks go through 16 rounds of cryptographic functions. |
|
|
SymmetricRC4 |
is one of the most commonly implemented stream ciphers. It has a variable key size, is used in the Secure Sockets Layer (SSL) protocol, and was (improperly) implemented in the 802.11WEP protocol standard. The algorithm is verysimple, fast, and efficient, which is why it became so popular. But it isvulnerable to modification attacks. This is one reason that IEEE 802.11i moved from the RC4 algorithm to the AES algorithm. |
|
|
Symmetric RC5 |
RC5 is a block cipher that has a variety of parameters it can use for block size, key size, and the number of rounds used.It was created by Ron Rivest. The block sizes used in this algorithm are 32,64, or 128 bits, and the key size goes up to 2,048 bits. The number of rounds used for encryption and decryption is also variable. The number of rounds cango up to 255. |
|
|
Symmetric RC6 |
RC6 is a block cipher that was built upon RC5, soit has all the same attributes as RC5. The algorithm was developed mainly to be submitted as AES, but Rijndael was chosen instead. There were some modifications of the RC5 algorithm to increase the overall speed, the result of which is RC6. |
|
|
Asymmetric Diffie-Hellman Algorithm |
is a specific method of securely exchanging cryptographic keys over a public channel and was one of the first public-key protocols. D–H is one of the earliest practical examples of public key exchange implemented within the field of cryptography. is vulnerable to a man-in-the-middle attack, because no authentication occurs before public keys are exchanged. The countermeasure to this type of attack is to have authentication take place before accepting someone’s public key. |
|
|
Asymmetric RSA |
RSA is one of the first practical public-key cryptosystems and is widely used for secure data transmission. In such a cryptosystem, the encryption key is public and differs from the decryption key which is kept secret. The security of this algorithm comes from the difficulty of factoring large numbers into theiroriginal prime numbers. The public and private keys are functions of a pair oflarge prime numbers, and the necessary activity required to decrypt a message from ciphertext to plaintext using a private key is comparable to factoring a product into two prime numbers. |
|
|
AsymmetricOne-Way Functions |
is a mathematical functionthat is easier to compute in one direction than in the opposite direction. |
|
|
AsymmetricEl Gamal |
is a public key algorithm that can be used for digital signatures, encryption, and key exchange. It is based not on the difficulty of factoring large numbers, but on calculating discrete logarithms in a finite field. provides the same type of functionality as some of the other asymmetric algorithms, its main drawback is performance. When compared to other algorithms, this algorithm is usually the slowest. |
|
|
Asymmetric Elliptic Curve Cryptosystems |
ECC leverages a one-way function that uses discrete logarithms as applied to elliptic curves. Solving this problem is harder than solving discrete logarithms, so algorithms based on Elliptic Curve Cryptography (ECC) are much stronger per bit than systems using discrete logarithms (and also stronger than factoring prime numbers). ECC requires less computational resources because shorter keys can be used compared to other asymmetric methods. ECC is often used in lower power devices for this reason. An elliptic curve cryptosystem (ECC) provides much of the same functionality RSA provides: digital signatures, secure key distribution, and encryption. One differing factor is ECC’s efficiency. ECC is more efficient than RSA and any other asymmetric algorithm. |
|
|
The One-Way Hash |
is a function that takes avariable-length string (a message) and produces a fixed-length value called ahash value. |
|
|
message authentication code(MAC). |
is an authentication scheme derived by applying a secret key to a message in some form. |
|
|
three basic types of MACfunctions: |
a hash MAC (HMAC), CBC-MAC, and CMAC. |
|
|
hash MAC (HMAC) |
is a specific type of message authentication code (MAC) involving a cryptographic hash function (hence the 'H') in combination with a secret cryptographic key. An iterative hash function breaks up a message into blocks of a fixed size and iterates over them with a compression function. For example, MD5 and SHA-1 operate on 512-bit blocks. The size of the output of HMAC is the same as that of the underlying hash function (128 or 160 bits in the case of MD5 or SHA-1, respectively), although it can be truncated if desired. |
|
|
CBC-MAC |
is being used, the message is encrypted with a symmetric block cipher in CBC mode, and the output of thefinal block of ciphertext is used as the MAC. |
|
|
the goal of using a one-wayhash function |
is to provide a fingerprint of the message. If two different messages produce the same hash value, it would be easier for an attacker to break that security mechanism because patterns would be revealed. A strong one-hash function should not provide the same hash value fortwo or more different messages. |
|
|
MD4 |
MD4 is a one-way hash function designed by RonRivest. It also produces a 128-bit message digest value. It was used forhigh-speed computation in software implementations and was optimized for micro processors. It is no longer considered secure. |
|
|
MD5 |
MD5 was also created by Ron Rivest and is thenewer version of MD4. It still produces a 128-bit hash, but the algorithm ismore complex, which makes it harder to break. MD5 added a fourth round ofoperations to be performed during the hashing functions and makes several ofits mathematical operations carry out more steps or more complexity to providea higher level of security. |
|
|
SHA-1 |
SHA was designed by NSA and published by NIST to be used with theDigital Signature Standard (DSS), produces a 160-bit hash value, or message digest. This is then inputted into an asymmetric algorithm,which computes the signature for a message. It has some extra mathematical functions and produces a 160-bit hash. was found to be vulnerable to collisions and is no longer considered secure for applications requiring collision resistance. |
|
|
SHA-2 |
A family of two similar hash functions, with different block sizes, known as SHA-256 and SHA-512. They differ in the word size; SHA-256 uses 32-bit words where SHA-512 uses 64-bit words. There are also truncated versions of each standard, known as SHA-224, SHA-384, SHA-512/224 and SHA-512/256. These were also designed by the NSA. |
|
|
birthday attack |
This attack is based on the mathematical birthday paradox that exists in standard statistics. |
|
|
Digital Signatures |
is a hash value that hasbeen encrypted with the sender’s private key. The act of signing meansencrypting the message’s hash value with a private key |
|
|
Public key infrastructure(PKI) |
consists of programs, dataformats, procedures, communication protocols, security policies, and public key cryptographic mechanisms working in a comprehensive manner to enable a wide range of dispersed people to communicate in a secure and predictable fashion. In other words, a PKI establishes a level of trust within an environment. PKI provides authentication, confidentiality, nonrepudiation, and integrity of the messages exchanged |
|
|
certificate authority (CA). |
is an entity that issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. In this model of trust relationships, a CA is a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate. The most commonly encountered public-key infrastructure (PKI) schemes are those used to implement https on the world-wide web. All these are based upon the X.509 standard and feature CAs. |
|
|
registration authority (RA) |
When a person requests a certificate, the registration authority (RA) verifies that individual’s identity and passes the certificate request off to the CA. The registration authority (RA) performs the certification registration duties. The RA establishes and confirms the identity of an individual, initiates the certification process with a CA on behalf of an end user, and performs certificate life-cycle management functions. The RA cannot issue certificates,but can act as a broker between the user and the CA. When users need new certificates, they make requests to the RA, and the RA verifies all necessary identification information before allowing a request to go to the CA. |
|
|
acertificate revocationlist (CRL). |
This is a list of every certificate that has been revoked. This list is maintained and updated periodically. |
|
|
certificate |
is the mechanism used to associate a public key with a collection of components in a manner that issufficient to uniquely identify the claimed owner. |
|
|
Trusted Platform Module(TPM) |
is a microchip installed onthe motherboard of modern computers and is dedicated to carrying out securityfunctions that involve the storage and processing of symmetric and asymmetrickeys, hashes, and digital certificates. is essentially a securely designed micro controller with added modules to perform cryptographic functions.These modules allow for accelerated and storage processing of cryptographic keys, hash values, and pseudo number sequences. |
|
|
Ciphertext-Only Attacks |
Inthis type of attack, the attacker has the ciphertext of several messages. Each of the messages has been encrypted using the same encryption algorithm. The attacker’s goal is to discover the key used in the encryption process. Once the attacker figures out the key, she can decrypt all other messages encrypted with the same key. |
|
|
Known-Plaintext Attacks |
the attacker has the plaintext and corresponding ciphertext of one or more messages. Again, the goal is to discover the key used to encrypt the messagesso other messages can be deciphered and read. |
|
|
Chosen-Plaintext Attacks |
the attacker has the plaintext and ciphertext, but can choose the plaintext that gets encrypted tosee the corresponding ciphertext. This gives the attacker more power andpossibly a deeper understanding of the way the encryption process works so shecan gather more information about the key being used. |
|
|
Chosen-Ciphertext Attacks |
theattacker can choose the ciphertext to be decrypted and has access to theresulting decrypted plaintext. Again, the goal is to figure out the key. Thisis a harder attack to carry out compared to the previously mentioned attacks,and the attacker may need to have control of the system that contains the cryptosystem. |
|
|
Differential Cryptanalysis |
This type of attack alsohas the goal of uncovering the key that was used for encryption purposes. This attack looks at ciphertext pairs generated by encryption of plaintext pairs with specific differences and analyzes the effect and result of those differences. |
|
|
Linear Cryptanalysis |
is another type of attackthat carries out functions to identify the highest probability of a specifickey employed during the encryption process using a block algorithm. |
|
|
Side-Channel Attacks |
is any attack based on information gained from the physical implementation of a cryptosystem, rather than brute force or theoretical weaknesses in the algorithms (compare cryptanalysis). |
|
|
Replay Attacks |
is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and re-transmits it, possibly as part of a masquerade attack by IP packet substitution. |
|
|
Algebraic Attacks |
analyze the vulnerabilities in the mathematics used within the algorithm and exploit the intrinsic algebraic structure. |
|
|
Analytic Attacks |
identify algorithm structural weaknesses or flaws, as opposed to brute-force attacks,which simply exhaust all possibilities without respect to the specific properties of the algorithm. Examples include the Double DES attack and RSA factoring attack. |
|
|
Statistical Attacks |
identify statistical weaknesses in algorithm design for exploitation—for example, if statistical patterns are identified, as in the number of zeros compared to the number ofones. For instance, a random number generator (RNG) may be biased. If keys aretaken directly from the output of the RNG, then the distribution of keys would also be biased. The statistical knowledge about the bias could be used to reduce the search time for the keys . |
|
|
Pipelining
|
combines multiple steps into one combined process, allowing simultaneous fetch, decode, execute, and write steps for different instructions. Each part is called a pipeline stage; the pipeline depth is the number of simultaneous stages that may be completed at once.
|
|
|
IPSEC
|
is a suite of protocols that provide a cryptographic layer to both IPv4 and IPv6. It is one of the methods used to provide Virtual Private Networks (VPN), which allow you to send private data over an insecure network, such as the Internet (the data crosses a public network, but is “virtually private”). IPsec includes two primary protocols: Authentication Header (AH) andEncapsulating Security Payload (ESP).
|
|
|
AH and ESP
|
Authentication Header provides authentication and integrity for each packet of network data. AH provides no confidentiality; it acts as a digital signature for the data. AH also protects against replay attacks, where data is sniffed off a network and resent, often in an attempt to fraudulently reuse encrypted authentication credentials.Encapsulating Security Payload primarily provides confidentiality by encrypting packet data. It may also optionally provide authentication and integrity.
|
|
|
IPSEC Tunnel mode
|
is used by security gateways (which can provide point-to-point IPsec tunnels). ESP Tunnel mode encrypts the entire packet, including the original packet headers.
|
|
|
IPSEC Transport mode
|
ESP Transport mode only encrypts the data (and not the original headers); this is commonly used when the sending and receiving system can “speak” IPsec natively.AH authenticates the original IP headers, so it is often used (along with ESP) in transport mode, because the original headers are not encrypted.
|
|
|
IKE
|
IPsec can use a variety of encryption algorithms, such as MD5 or SHA-1 for integrity, and triple DES or AES for confidentiality. The Internet Key Exchange negotiates the algorithm selection process. Two sides of an IPsec tunnel will typically use IKE to negotiate to the highest and fastest level of security, selecting AES over single DES for confidentiality if both sides support AES, for example.
|
|
|
PGP
|
Pretty Good Privacy (PGP) brought asymmetric encryption to the masses. Phil Zimmerman created a controversy when he released PGP in 1991. For the first time, an average computer user could easily leverage the power of asymmetric encryption, which allows strangers (including criminals) to securely communicate without pre-sharing a key.
|
|
|
S/MIME
|
MIME (Multipurpose Internet Mail Extensions) provides a standard way to format email, including characters, sets, and attachments. S/MIME (Secure/MIME) leverages PKI to encrypt and authenticate MIME-encoded email. The client or client’s email server (called an S/MIME gateway) may perform the encryption.
|
|
|
ESCROWED ENCRYPTION
|
Escrowed encryption means a third-party organization holds a copy of a public/private key pair. The private key is often divided into two or more parts, each held in escrow by different trusted third-party organizations, which will only release their portion of the key with proper authorization, such as a court order. This provides separation of duties.
|
|
|
Clipper Chip
|
The Clipper Chip was the name of the technology used in the Escrowed Encryption Standard (EES), an effort announced in 1993 by the United States government to deploy escrowed encryption in telecommunications devices. The effort created a media firestorm, and was abandoned by 1996.
|
|
|
Perimeter Defenses
|
Perimeter defenses help prevent, detect, and correct unauthorized physical access. Buildings, like networks, should employ defense-in-depth. Any one defense may fail: so critical assets should be protected by multiple physical security controls, such as fences, doors, walls, locks, etc. The ideal perimeter defense is safe, prevents unauthorized ingress, and when applicable offers both authentication and accountability.
|
|
|
FENCES
|
Fences may range from simple deterrents (such as 3-foot/1-meter tall fencing) to preventive devices, such as an 8-foot (2.4 meter) tall fence with barbed wire on top. Fences should be designed to steer ingress and egress to controlled points, such as exterior doors and gates.
|
|
|
BOLLARDS
|
A traffic bollard is a strong post designed to stop a car. The term derives from the short/strong posts (called mooring bollards) used to tie ships to piers when docked
|
|
|
LIGHTS
|
Lights can act as both a detective and deterrent control. A light that allows a guard to see an intruder is acting as a detective control. Criminals will usually favor a poorly lighted target over a more visible one, so light can also act as a deterrent.
|
|
|
CCTV
|
Closed Circuit Television (CCTV) is a detective device used to aid guards in detecting the presence of intruders in restricted areas. CCTVs using the normal light spectrum require sufficient visibility to illuminate the field of view that is visible to the camera. Infrared devices can “see in the dark” by displaying heat.
|
|
|
LOCKS
|
Locks are a preventive physical security control, used on doors and windows to prevent unauthorized physical access. Locks may be mechanical, such as key locks or combination locks, or electronic, which are often used with smart cards or magnetic stripe cards.
|
|
|
Key Locks
|
Key locks require a physical key to unlock. Keys may be shared or sometimes copied, which lowers the accountability of key locks. Also, many keys contain the “combination,” (called a bitting code) printed right on the bow of the key.
|
|
|
Lock Picking
|
Lock picking is the art of opening a lock without a key.
|
|
|
SMART CARDS
|
A smart card is a physical access control device that is often used for electronic locks, credit card purchases, or dual-factor authentication systems. “Smart” means the card contains a computer circuit; another term for a smart card is “Integrated Circuit Card” (ICC).
|
|
|
TAILGATING/PIGGYBACKING
|
Tailgating (also known as piggybacking) occurs when an unauthorized person follows an authorized person into a building after the authorized person unlocks and opens the door. Policy should forbid employees from allowing tailgating and security awareness efforts should describe this risk.
|
|
|
MANTRAPS
|
A mantrap is a preventive physical control with two doors. The first door must close and lock before the second door may be opened. Each door typically requires a separate form of authentication to open; a common combination is PIN (Personal Identification Number) and biometrics. The intruder is trapped between the doors after entering the mantrap.
|
|
|
Turnstiles
|
are designed to prevent tailgating by enforcing a “one person per authentication” rule, just as they do in subway systems. Secure data centers often use floor-to-ceiling turnstiles with interlocking blades to prevent an attacker from going over or under the turnstile. Secure revolving doors perform the same function.Both mantraps and turnstiles must be designed to allow safe egress in case of emergency. No system should require authentication for egress during emergencies.
|
|
|
Environmental Controls
|
Environmental controls are designed to provide a safe environment for personnel and equipment. Power, HVAC, and fire safety are considered environmental controls.
|
|
|
Electrical Faults
|
Electrical faults involve short and long-term interruption of power, as well as various cases of low and high voltage. All types of electrical faults can impact availability and integrity. A blackout may affect availability of the system, for example, but can also impact integrity if a hard disk is damaged due to sudden loss of power.
|
|
|
The following are common types of electrical faults:
|
• Blackout: prolonged loss of power • Brownout: prolonged low voltage • Fault: short loss of power • Surge: prolonged high voltage • Spike: temporary high voltage • Sag: temporary low voltage |
|
|
Surge Protectors
|
Surge Protectors protect equipment from damage due to electrical surges. They contain a circuit or fuse that is tripped during a power spike or surge, shorting the power or regulating it down to acceptable levels.
|
|
|
Uninterruptible Power Supplies
|
Uninterruptible Power Supplies (UPSs) provide temporary backup power in the event of a power outage. They may also “clean” the power, protecting against surges, spikes, and other forms of electrical faults.
|
|
|
Generators
|
Generators are designed to provide power for longer periods of times than UPSs, and will run as long as fuel is available. Sufficient fuel should be stored onsite for the period the generator is expected to provide power. Refueling strategies should consider a disaster’s effect on fuel supply and delivery.
|
|
|
EMI
|
Electricity generates magnetism, so any electrical conductor emits Electromagnetic Interference (EMI). This includes circuits, power cables, network cables, and many others. Network cables that are poorly shielded or run too closely together may suffer crosstalk, where magnetism from one cable “crosses” over to another nearby cable.
|
|
|
HVAC
|
HVAC (heating, ventilation, and air conditioning) controls keep the air at a reasonable temperature and humidity. They operate in a closed loop, recirculating treated air. This helps reduce dust and other airborne contaminants.
|
|
|
Positive Pressure and Drains
|
All HVAC units should employ positive pressure and drainage. This means air and water should be expelled from the building. Untreated air should never be “inhaled” into the building, and water should drain away from the building.A common malfunction of HVAC units is condensation of water pooling into the building, often going under raised floors where it may not be detected. Positive drains are designed to avoid this problem. Location of all gas and water lines, as well as all drains, should be formally documented.
|
|
|
Heat and Humidity
|
Data center HVAC units are designed to maintain optimum heat and humidity levels for computers. Humidity levels of 40–55% are recommended. A commonly recommended “set point” temperature range for a data center is 68–77°F (20–25°C).
|
|
|
Heat Detectors
|
Heat detectors alert when temperature exceeds an established safe baseline. They may trigger when a specific temperature is exceeded or when temperature changes at a specific rate (such as “10°F in less than 5 minutes”).
|
|
|
Smoke Detectors
|
Smoke detectors work through two primary methods: ionization and photoelectric. Ionization-based smoke detectors contain a small radioactive source that creates a small electric charge. Photoelectric sensors work in a similar fashion, except that they contain an LED (Light Emitting Diode) and a photoelectric sensor that generates a small charge while receiving light. Both types of alarm alert when smoke interrupts the radioactivity or light, lowering or blocking the electric charge.Dust should always be avoided in data centers. Small airborne dust particles can trigger smoke detectors just as smoke does, leading to false alarms.
|
|
|
Flame Detectors
|
Flame detectors detect infrared or ultraviolet light emitted in fire. One drawback to this type of detection is that the detector usually requires line-of-site to detect the flame; smoke detectors do not have this limitation.
|
|
|
Evacuation Routes
|
Evacuation routes should be prominently posted, as they are in hotel rooms. All personnel should be advised of the quickest evacuation route from their areas. Guests should be advised of evacuation routes as well.All sites should use a meeting point, where all personnel will meet in the event of emergency. Meeting points are critical: tragedies have occurred where a person outside the front of a building does not realize another is outside the back, and reenters the building for attempted rescue.
|
|
|
Evacuation Roles and Procedures
|
The two primary evacuation roles are safety warden and meeting point leader.
|
|
|
safety warden
|
ensures that all personnel safely evacuate the building in the event of an emergency or drill.
|
|
|
meeting point
|
The meeting point leader assures that all personnel are accounted for at the emergency meeting point. Personnel must follow emergency procedures, and quickly follow the posted evacuation route in case of emergency or drill.
|
|
|
Dry Powder
|
Extinguishing a fire with dry powder (such as sodium chloride) works by lowering temperature and smothering the fire, starving it of oxygen. Dry powder is primarily used to extinguish metal fires. Flammable metals include sodium, magnesium, and many others.
|
|
|
Wet Chemical
|
Wet chemicals are primarily used to extinguish kitchen fires (type K fires in the U.S.; type F in Europe), but may also be used on common combustible fires (type A). The chemical is usually potassium acetate mixed with water. This covers a grease or oil fire in a soapy film that lowers the temperature.
|
|
|
CO2
|
CO2, oxygen, and nitrogen are what we breathe as air. Fires require oxygen as fuel, so removing oxygen smothers fires: this is how CO2 fire suppression works.A risk associated with CO2 is it is odorless and colorless, and our bodies will breathe it as air. By the time we begin suffocating due to lack of oxygen, it is often too late.
|
|
|
Halon and Halon Substitutes
|
Halon extinguishes fire via a chemical reaction that consumes energy and lowers the temperature of the fire. Halon is being phased out, and a number of replacements with similar properties are now used.
|
|
|
Halon Replacements
|
Recommended replacements for Halon include the following systems: • Argon • FE-13 • FM-200 • Inergen |
|
|
Sprinkler Systems
|
All sprinkler systems should be combined with a fire alarm that alerts people to evacuate the premises in case of fire. Safe evacuation is the primary goal of fire safety.
|
|
|
Wet Pipe
|
Wet pipes have water right up to the sprinkler heads: the pipes are “wet.” The sprinkler head contains a metal (common in older sprinklers) or small glass bulb designed to melt or break at a specific temperature. Once that occurs, the sprinkler head opens and water flows.
|
|
|
Dry Pipe
|
Dry pipe systems also have closed sprinkler heads: the difference is the pipes are filled with compressed air. The water is held back by a valve that remains closed as long as sufficient air pressure remains in the pipes. As the dry pipe sprinkler heads open, the air pressure drops in each pipe, allowing the valve to open and send water to that head.Dry pipes are often used in areas where water may freeze, such as parking garages.
|
|
|
Deluge
|
Deluge systems are similar to dry pipes, except the sprinkler heads are open and larger than dry pipe heads. The pipes are empty at normal air pressure; a deluge valve holds the water back. The valve is opened when a fire alarm (that may monitor smoke or flame sensors) triggers.
|
|
|
Pre-Action
|
Pre-action systems are a combination of wet, dry, or deluge systems, and require two separate triggers to release water. Single interlock systems release water into the pipes when a fire alarm triggers. The water releases once the head opens. Double interlock systems use compressed air (same as dry pipes): the water will not fill the pipes until both the fire alarm triggers and the sprinkler head opens. This allows manual intervention before a full discharge of water on the equipment occurs. This is currently the most recommended water system for a computer room.
|
|
|
Portable Fire Extinguishers
|
All portable fire extinguishers should be marked with the type of fire they are designed to extinguish.Portable extinguishers should be small enough to be operated by any personnel who may need to use one. This means those old brass monster extinguishers are not a recommended control.
|
|
|
Natural environmental threats
|
Floods, earthquakes, storms and tornadoes, fires, extreme temperature conditions, and so forth
|
|
|
Supply system threats
|
Power distribution outages, communications interruptions, and interruption of other resources such as water, gas, air filtration, and so on
|
|
|
Manmade threats
|
Unauthorized access (both internal and external), explosions, damage by disgruntled employees, employee errors and accidents, vandalism, fraud, theft, and others
|
|
|
Politically motivated threats
|
Strikes, riots, civil disobedience, terrorist attacks, bombings, and so forth
|
|
|
layered defense models
|
which means that physical controls should work together in a tiered architecture. The concept is that if one layer fails, other layers will protect the valuable asset. Layers would be implemented moving from the perimeter toward the asset.
|
|
|
collusion
|
in which two or more people work together to carry out fraudulent activity.
|
|
|
An organization’s physical security program should address the following goals:
|
• Crime and disruption prevention through deterrence Fences, security guards, warning signs, and so forth • Reduction of damage through the use of delaying mechanisms Layers of defenses that slow down the adversary, such as locks, security personnel, and barriers • Crime or disruption detection Smoke detectors, motion detectors, CCTV, and so forth • Incident assessment Response of security guards to detected incidents and determination of damage level • Response procedures Fire suppression mechanisms, emergency response processes, law enforcement notification, and consultation with outside security professionals |
|
|
Crime Prevention Through Environmental Design
|
Design (CPTED) is a discipline that outlines how the proper design of a physical environment can reduce crime by directly affecting human behavior. It provides guidance in loss and crime prevention through proper facility construction and environmental components and procedures. Provides guidelines on items some of us might not consider.
|
|
|
Target hardening
|
focuses on denying access through physical and artificial barriers (alarms, locks, fences, and so on). focuses on denying access through physical and artificial barriers (alarms, locks, fences, and so on).
|
|
|
CPTED provides three main strategies to bring together the physical environment and social behavior to increase overall protection:
|
natural access control, natural surveillance, and natural territorial reinforcement.
|
|
|
Natural Access Control
|
Natural access control is the guidance of people entering and leaving a space by the placement of doors, fences, lighting, and even landscaping. For example, an office building may have external bollards with lights in them
|
|
|
Natural Surveillance
|
Surveillance can also take place through organized means (security guards), mechanical means (CCTV), and natural strategies (straight lines of sight, low landscaping, raised entrances). The goal of natural surveillance is to make criminals feel uncomfortable by providing many ways observers could potentially see them and to make all other people feel safe and comfortable by providing an open and well-designed environment.
|
|
|
Natural Territorial Reinforcement
|
which creates physical designs that emphasize or extend the company’s physical sphere of influence so legitimate users feel a sense of ownership of that space. Territorial reinforcement can be implemented through the use of walls, fences, landscaping, light fixtures, flags, clearly marked addresses, and decorative sidewalks. The goal of territorial reinforcement is to create a sense of a dedicated community.
|
|
|
facility safety officer
|
whose main job is to understand all the components that make up the facility and what the company needs to do to protect its assets and stay within compliance. This person should oversee facility management duties day in and day out, but should also be heavily involved with the team that has been organized to evaluate the organization’s physical security program.
|
|
|
physical security program
|
is a collection of controls that are implemented and maintained to provide the protection levels necessary to be in compliance with the physical security policy. The policy should embody all the regulations and laws that must be adhered to and should set the risk level the company is willing to accept.
|
|
|
Deterrence of criminal activity
|
A. Fences B. Warning signs C. Security guards D. Dogs |
|
|
Delay of intruders to help ensure they can be caught
|
A. Locks B. Defense-in-depth measures C. Access controls |
|
|
Detection of intruders
|
A. External intruder sensors B. Internal intruder sensors |
|
|
Assessment of situations
|
A. Security guard procedures B. Damage assessment criteria |
|
|
Response to intrusions and disruptions
|
A. Communication structure (calling tree) B. Response force C. Emergency response procedures D. Police, fire, medical personnel |
|
|
mantrap
|
is a small room with two doors. The first door is locked; a person is identified and authenticated by a security guard, biometric system, smart card reader, or swipe card reader. Once the person is authenticated and access is authorized, the first door opens and allows the person into the mantrap. The first door locks and the person is trapped. The person must be authenticated again before the second door unlocks and allows him into the facility.
|
|
|
fail-safe
|
A fail-safe setting means that if a power disruption occurs that affects the automated locking system, the doors default to being unlocked. Fail-safe deals directly with protecting people. If people work in an area in which there is a fire or the power is lost, it is not a good idea to lock them in
|
|
|
A fail-secure
|
A fail-secure configuration means that the doors default to being locked if there are any problems with the power. If people do not need to use specific doors for escape during an emergency, then these doors can most likely default to fail-secure settings.
|
|
|
Window Types
|
• Standard No extra protection. The cheapest and lowest level of protection. • Tempered Glass is heated and then cooled suddenly to increase its integrity and strength.• Acrylic A type of plastic instead of glass. Polycarbonate acrylics are stronger than regular acrylics. • Wired A mesh of wire is embedded between two sheets of glass. This wire helps prevent the glass from shattering. • Laminated The plastic layer between two outer glass layers. The plastic layer helps increase its strength against breakage. • Solar window film Provides extra security by being tinted and offers extra strength due to the film’s material. • Security film Transparent film is applied to the glass to increase its strength. |
|
|
Internal partitions
|
are used to create barriers between one area and another. These partitions can be used to segment separate work areas, but should never be used in protected areas that house sensitive systems and devices.
|
|
|
Data centers, server rooms, and wiring closets should be located:
|
in the core areas of a facility, near wiring distribution centers. Strict access control mechanisms and procedures should be implemented for these areas.
|
|
|
The data processing center
|
should be constructed as one room rather than different individual rooms. The room should be away from any of the building’s water pipes in case a break in a line causes a flood. The vents and ducts from the HVAC system should be protected with some type of barrier bars and should be too small for anyone to crawl through and gain access to the center. The data center must have positive air pressure, so no contaminants can be sucked into the room and into the computers’ fans.Smoke detectors or fire sensors should be implemented, and portable fire extinguishers should be located close to the equipment and should be easy to see and access
|
|
|
ROT13
|
("rotate by 13 places", sometimes hyphenated ROT-13) is a simple letter substitution cipher that replaces a letter with the letter 13 letters after it in the alphabet. ROT13 is an example of the Caesar cipher, developed in ancient Rome.
|
|
|
The Caesar cipher
|
is a simple substitution cipher that involves shifting the alphabet three positions to the right. In cryptography, a Caesar cipher, also known as Caesar's cipher, the shift cipher, Caesar's code or Caesar shift, is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a left shift of 3, D would be replaced by A, E would become B, and so on. The method is named after Julius Caesar, who used it in his private correspondence.
|
|
|
Polyalphabetic cipher
|
refers to using multiple alphabets at a time. A polyalphabetic cipher is any cipher based on substitution, using multiple substitution alphabets. The Vigenère cipher is probably the best-known example of a polyalphabetic cipher, though it is a simplified special case.
|
|
|
Transposition cipher
|
In cryptography, a transposition cipher is a method of encryption by which the positions held by units of plaintext (which are commonly characters or groups of characters) are shifted according to a regular system, so that the ciphertext constitutes a permutation of the plaintext. That is, the order of the units is changed. See the reference below for multiple examples of Transpositio Ciphers.
|

