![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
10 Cards in this Set
- Front
- Back
|
Which of the following steganography utilities exploits the nature of white space and allows the
user to conceal information in these white spaces? A. Gif-It-Up B. Image Hide C. NiceText D. Snow |
D. Snow
Snow is used to conceal messages in ASCII text by appending whitespace to the end of lines. Because spaces and tabs are generally not visible in text viewers, the message is effectively hidden from casual observers. And if the built-in encryption is used, the message cannot be read even if it is detected. |
|
|
In the context of Trojans, what is the definition of a Wrapper?
A. A tool used to encapsulate packets within a new header and footer B. An encryption tool to protect the Trojan C. A tool used to calculate bandwidth and CPU cycles wasted by the Trojan D. A tool used to bind the Trojan with a legitimate file |
D. A tool used to bind the Trojan with a legitimate file.
Wrappers allow an attacker to take any executable back-door program and combine it with any legitimate executable, creating a Trojan horse without writing a single line of new code |
|
|
When Jason moves a file via NFS over the company's network, you want to grab a copy of it by sniffing. Which of the following tool accomplishes this?
A. nfscopy B. macof C. filesnarf D. webspy |
C. Filesnarf
Filesnarf - sniffs files from NFS traffic. OPTIONS: -i "Interface" (Specify the interface to listen on) -v "Versus" mode. (Invert the sense of matching, to select non-matching files. pattern (Specify regular expression for filename matching.) expression (Specify a tcpdump(8) filter expression to select traffic to sniff.) SEE ALSO Dsniff, nfsd |
|
|
Derek has stumbled upon a wireless network and wants to assess its security. However, he does not find enough traffic for a good capture. He intends to use AirSnort on the captured traffic to crack the WEP key and does not know the IP address range or the AP. How can he generate
traffic on the network so that he can capture enough packets to crack the WEP key? A. Use a session replay on the packets captured B. Use KisMAC as it needs two USB devices to generate traffic C. Use any ARP requests found in the capture D. Use Ettercap to discover the gateway and ICMP ping flood tool to generate traffic |
D. Use Ettercap. By forcing the network to answer to a lot of ICMP messages you can gather enough packets to
crack the WEP key. |
|
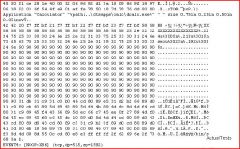
The following is an entry captured by a network IDS. You are assigned the task of analyzing this
entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel A. The attacker is attempting a buffer overflow attack and has succeeded B. The buffer overflow attack has been neutralized by the IDS C. The attacker is creating a directory on the compromised machine D. The attacker is attempting an exploit that launches a command-line shell processor. You figure that the attacker is attempting a buffer overflow attack. You also notice "/bin/sh" in the ASCII part of the output. As an analyst what would you conclude about the attack? |
D. The attacker is attempting an exploit that launches a command line shell.
|
|
|
Bill has started to notice some slowness on his network when trying to update his company's website and while trying to access the website from the Internet. Bill asks the help desk manager if he has received any calls about slowness from the end users, but the help desk manager says that he has not. Bill receives a number of calls from customers that cannot access the company website and cannot purchase anything online. Bill logs on to a couple of his routers and notices that the logs show network traffic is at an all time high. He also notices that almost all the traffic is originating from a specific address.
Bill decides to use Geotrace to find out where the suspect IP is originates from. The Geotrace utility runs a traceroute and finds that the IP is coming from Panama. Bill knows that none of his customers are in Panama so he immediately thinks that his company is under a Denial of Service attack. Now Bill needs to find out more about the originating IP address. What Internet registry should Bill look in to find the IP address? A. RIPE LACNIC B. APNIC C. ARIN D. LACNIC |
LACNIC is the Latin American and Caribbean Internet Addresses Registry that administers IP
addresses, autonomous system numbers, reverse DNS, and other network resources for that region. |
|
|
Bob has been hired to do a web application security test. Bob notices that the site is dynamic and must make use of a back end database. Bob wants to see if SQL Injection would be possible.
What is the first character that Bob should use to attempt breaking valid SQL request? A. Semi Column B. Single Quote C. Exclamation Mark D. Double Quote |
B. Single quote.
In SQL single quotes are used around values in queries, by entering another single quote Bob tests if the application will submit a null value and probably returning an error. |
|
|
Angela is trying to access an education website that requires a username and password to login.
When Angela clicks on the link to access the login page, she gets an error message stating that the page cannot be reached. She contacts the website's support team and they report that no one else is having any issues with the site. After handing the issue over to her company's IT department, it is found that the education website requires any computer accessing the site must be able to respond to a ping from the education website's server. Since Angela's computer is behind a corporate firewall, her computer cannot ping the education website back. What can Angela's IT department do to get access to the education website? A. Use an Internet browser other than the one that Angela is currently using B. Change the settings on the firewall to allow all incoming traffic on port 80 C. Change the IP on Angela's computer to an address outside the firewall D. Change the settings on the firewall to allow all outgoing traffic on port 80 |
C. Change the IP on Angela's computer to an address outside the firewall.
Allowing traffic to and from port 80 will not help as this will be UDP or TCP traffic and ping uses ICMP. The browser used by the user will not make any difference. The only alternative here that would solve the problem is to move the computer to outside the firewall. |
|
|
Null sessions are un-authenticated connections (not using a username or password.) to an NT or
2000 system. Which TCP and UDP ports must you filter to check null sessions on your network? A. 137 and 139 B. 137 and 443 C. 139 and 445 D. 139 and 443 |
C. 139 and 445.
NULL sessions take advantage of "features" in the SMB (Server Message Block) protocol that exist primarily for trust relationships. You can establish a NULL session with a Windows host by logging on with a NULL user name and password. Primarily the following ports are vulnerable if they are accessible: 137-139, 445. While ports 137-139 were known technically as "NBT over IP", port 445 is "SMB over IP". (SMB is known as "Samba" and stands for "Server Message Blocks".) After all of the trouble the personal computer industry has had with Microsoft's original Windows NetBIOS ports 137 through 139, it is difficult to imagine or believe that Microsoft could have actually made things significantly worse with their replacement port 445 . . . but they did. |
|
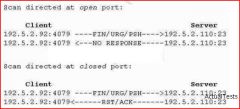
What type of port scan is shown below?
Scan directed at open port: A. Windows Scan B. Idle Scan C. SYN Stealth Scan D. XMAS Scan |
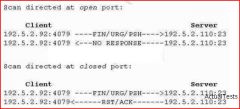
D. XMAS Scan
|

