![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
100 Cards in this Set
- Front
- Back
|
Jack and John are investigation a computer breach that costs in the area of $75,000 in damages and needs to be handled on the same day the incident occurred. What incident level would this be classified as?
a) This incident would be classified as a high level incident. b) This would be considered a low level incident. c) This incident would be classified as an immediate level incident. d) This situation would be classified as a mid-level incident. |
d) This situation would be classified as a mid-level incident.
|
|
|
Which type of password cracking is similar to a dictionary attack but adds numbers and symbols to the words from the dictionary to try and crack the passwords?
a) Hybrid b) Brute force c) Syllable Attack d) Rule Based Attack |
a) Hybrid
|
|
|
Which command will cause an attacker to be able to gain a command shell on the victim if the command is run on the victim machine on port 56?
a) nc -p 56 -p -e cmd.exe b) nc -L 56 -t -e cmd.exe c) nc -port 56 -s cmd.exe d) nc -r 56 -c cmd.exe |
b) nc -L 56 -t -e cmd.exe
|
|
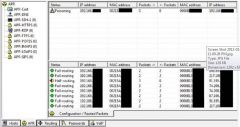
The tool Shown in the graphic is widely used for ARP Poisoning attacks. What is the name of the tool?
a) Beat Infector b) Poison Ivy c) Web Arp Infector d) Cain and Able |
d) Cain and Able
|
|
|
Which of the following usually can't be performed using an email tracking software? (may also be called tracking probe)
a) Time spent on reading emails b) Whether or not the recipient visited any links sent in the email c) GPS Location of the email recipient d) Remote control the users email client application and hijack traffic e) When the email was received and read f) Send destructive emails g) Track PDF's and other types of attachments |
d) Remote control the users email client application and hijack traffic
|
|
|
Which nslookup command would allow you to extract hinfo records from a dns server?
a) set dns=hinfo b) configure type=hinfo c) set record=hinfo d) set type=hinfo |
d) set type=hinfo
|
|
|
Which TCP flag instructs the sending system to send all buffered data immediately?
a) FIN b) PSH c) SYN d) ACK |
b) PSH
|
|
|
Which techniques are effective for evading IDS during a port scan? (select up to 4)
a) Use source routing when possible b) Overload the IDS with junk traffic to mask your scan c) Use fragmented IP packets d) Connect to proxy servers or trojaned machines to launch scans e) Spoof your ip address then sniff responses from the server being scanned |
a) Use source routing when possible
c) Use fragmented IP packets d) Connect to proxy servers or trojaned machines to launch scans e) Spoof your ip address then sniff responses from the server being scanned |
|
|
Which of the following is an example of Rogue Security Software?
a) Based on social engineering technique which lures a victim to bogus sites. b) Software that disables security features like firewalls and AV c) A fake AV program that claims to rid a computer of malware, but instead installs spyware or other malware on the computer. |
c) A fake AV program that claims to rid a computer of malware, but instead installs spyware or other malware on the computer.
|
|
|
What can an attacker do with whois records? (select all that apply)
a) An attacker can attempt phishing and social engineering on targeted individuals using the information from whois records b) Search engines like Google and Bing will expose information listed on the whois records c) Spammers can send unsolicited emails to addresses listed in the whois record d) IRS Agents will use this information in the whois records |
a) An attacker can attempt phishing and social engineering on targeted individuals using the information from whois records
c) Spammers can send unsolicited emails to addresses listed in the whois record |
|
|
Sniffing on a switched network is called ______________ sniffing
a) Grass b) Passive c) Sneaky d) Active |
d) Active
|
|
|
You cannot COMPLETELY block attackers doing password cracking attempts against web resources if they are constantly switching proxies.
a) True b) False |
a) True
|
|
|
Neil used a fake ID badge and uniform to follow other employees into a target organization. What technique did he use?
a) Piggybacking b) Being smart c) Lizard Licking attack d) Tailgating |
d) Tailgating
|
|
|
What is the length of an MD5 hash?
a) 48 bit b) 128 bit c) 68 bit d) 32 bit |
d) 32 bit
|
|
|
You have compromised a 2003 Server using a SMB exploit. Which command could you enter from the command line to disable auditing?
a) EnterPol /nolog b) EventViewer -NoService c) stoplog -d d) auditpol.exe /disable |
d) auditpol.exe /disable
|
|
|
What two things will happen if a router receives an ICMP packet, which has a TTL value of 1, and the destination host is several hops away? (select 2)
a) The router will decrement the value b) The router will send a time exceeded message to the source host c) The router will send an ICMP redirect message d) The router will increment the value e) The router will discard the packet |
b) The router will send a time exceeded message to the source host
e) The router will discard the packet |
|
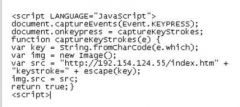
What will the code in the graphic do?
a) It is a piece of Javascript that will place a specific image on every page of an RSS feed b) Send a message to a server whenever the ESC key is pressed c) Use a Webbug to send messages d) Log all keystrokes |
d) Log all keystrokes
|
|
|
One way to verify the authenticity of emails is to do what?
a) Fake email uses extensive images. If there are a lot of images, it is probably fake b) Verify the digital signature attached to the email. A fake email will not have a digital signature that matches the faked domain c) Check the sender ID against the National Spam Database d) Fake mail will have spelling and grammatical errors. |
b) Verify the digital signature attached to the email. A fake email will not have a digital signature that matches the faked domain
|
|
|
Which type of sniffing technique is generally referred to as a MiTM attack?
a) MAC Flooding b) ARP Spoofing c) Password Sniffing d) DHCP Sniffing |
b) ARP Spoofing
|
|
|
What port does NTP use?
a) 125 b) 126 c) 123 d) 124 |
c) 123
|
|
|
It is a common technique to use Steganography to hide the true content of attachments sent out via email. One example of this is hiding an Excel file named infosec.xls inside a image file named photo1.jpg, then emailing it. Would you say this statement is true or false?
a) This is somewhat true but, not completely since you can only hide text in image files when using Steganography b) This is true, period c) This is not true |
b) This is true, period
|
|
|
What type of password cracking table consists of pre-computed hashes?
a) Moon Tables b) Rainbow Tables c) Storm Tables d) Sun Tables |
b) Rainbow Tables
|
|
|
How would you keep Google from storing your search keywords? (so your search history doesn't show up when you start typing in the search bar in Google).
a) Block Google cookies by applying privacy and security settings in your browser b) Use Mac OSX instead of Windows 7 c) Do not use Google, but use Bing! Because it doesn't store anything (nor does it find anything) d) Disable Google cookies using Google's advanced search options |
settings in your browser
|
|
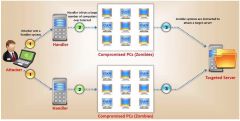
What type of attack is shown in the graphic?
a) Cluster Service Attack b) Distributed Denial of Service c) Bandwitch Exhaust Attack d) Denial of Service |
b) Distributed Denial of Service
|
|
|
In what part of the OSI model does ARP poisoning occur?
a) Network Layer b) Datalink Layer c) Physical Layer d) Application Layer |
b) Datalink Layer
|
|
|
At what layer does TCP Session Hijacking occur?
a) Network Layer b) Application Layer c) Session Layer d) Transport Layer |
d) Transport Layer
|
|
|
Someone sent you a link that supposedly goes to cnn.com. The page looks like CNN but the URL says CNIN.com. How would you verify if the site is authentic or not?
a) Visit the site using SSL b) Navigate to the site by visiting various blogs and forums for authentic links c) Enable caching on your web browser and look for popup warnings d) Visit the site by clicking on a link that you find when doing a google search for REAL domain |
d) Visit the site by clicking on a link that you find when doing a google search for REAL domain
|
|
|
Which Trojan would be considered "Botnet Command and Control Center"?
a) Damen Rock b) Matten Kit c) YOUkill Doom d) Poison Ivy |
d) Poison Ivy
|
|
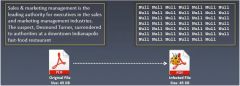
Which type of virus is shown in the graphic
a) Sparse Infector Virus b) Metamorphic Virus c) Boot Sector Virus d) Cavity Virus |
d) Cavity Virus
|
|
|
Your company only allows traffic over ports 80 and 443. You want to use an FTP server. How would you accomplish this with the current firewall rules.
a) Use the TOR network b) Use a Reverse Proxy c) Use Proxy chaining d) Use HTTP Tunneling |
d) Use HTTP Tunneling
|
|
|
How would you exploit TCP using a TCP SYN Attack?
a) Flood with TCP RST packets with random source addresses b) Flood TCP SYN packets with random source addresses towards the victim c) Flood with TCP ACK packets with random source addresses |
b) Flood TCP SYN packets with random source addresses towards the victim
|
|

In the graphic, which packet represents the completion of the three-way handshake?
a) 6th Packet b) 8th Packet c) 5th Packet d) 4th Packet |
c) 5th Packet
|
|

Study the graphic scenario/process. In which stage would you engage a forensic investigator?
a) 5 b) 3 c) 4 d) 1 |
c) 4
|
|
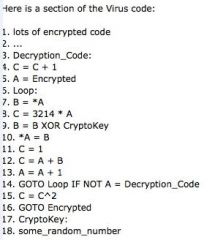
Study the snippet of virus code in the graphic. What type of virus do you think this is?
a) Metamorphic b) Shuttle c) Stealth d) Polymorphic |
d) Polymorphic
|
|
|
Which statement is INCORRECT concerning vulnerability scanners?
a) They can validate compliance without deviations from organizational security policies b) Vulnerability scanners can help identify missing patches, out of date software, and system upgrades c) Vulnerability scanners can identify vulnerabilities and also fix and patch these vulnerabilities without intervention d) Vulnerability scanners attempt to identify vulnerabilities in hosts being scanned |
c) Vulnerability scanners can identify vulnerabilities and also fix and patch these vulnerabilities without intervention
|
|
|
Which of the following represent weak passwords? (select up to 2)
a) Passwords that contain only special characters b) Passwords that contain special characters and numbers c) Passwords that contain only letters. for example; QWERTY d) Passwords that contain Uppercase/Lowercase from a dictionary list. For example; ApPle |
c) Passwords that contain only letters. for example; QWERTY
d) Passwords that contain Uppercase/Lowercase from a dictionary list. For example; ApPle |
|
|
Social Engineering is NOT part of the CEH Scanning lifecycle?
a) True b) False |
a) True
|
|
|
The easiest way to get users to install Trojans is have them download games, files and screensavers from internet sites?
a) True b) False |
a) True
|
|
|
Packets transmitted in either direction after the initial three-way handshake will have the PSH flag bit set.
a) True b) False |
b) False
|
|
|
In which stage of the Virus lifecycle does a stealth virus get activiated?
a) Elimination b) Incorporation c) Launch d) Design |
c) Launch
|
|
|
What is the default password hash algorithm used by NTLMv2?
a) MD4 b) DES c) SHA d) MD5 |
d) MD5
|
|
|
What port does Syslog Daemons listen on?
a) 312 b) 330 c) 120 d) 514 |
d) 514
|
|
|
What privilege does a rootkit usually require to successfully infect a user machine?
a) User Level priv b) Kernel Level priv c) Ring 3 priv d) System Level priv |
b) Kernel Level priv
|
|
|
Which of the following is the correct filter to look for people using facebook?
a) List.display.facebook b) traffic.content==facebook c) display==facebook d) tcp contains facebook |
d) tcp contains facebook
|
|
|
Which hping command would generate a packet that would appear to originate from 10.0.0.8?
a) hping3 -0 10.0.0.8 -S springvalley -c 2 -p 80 b) hping3 -T 10.0.0.8 -S springvalley -c 2 -p 80 c) hping3 -a 10.0.0.8 -S springvalley -c 2 -p 80 d) hping3 -Y 10.0.0.8 -S springvalley -c 2 -p 80 |
c) hping3 -a 10.0.0.8 -S springvalley -c 2 -p 80
|
|
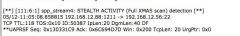
Based on the SNORT IDS rule shown in the graphic, which hping command would you suspect generated the alert?
a) hping -S -R -P -A -F -U 192.168.2.56 -p 22 -c 5 -t 118 -y b) hping -S -R -M -F -A -U 192.168.2.56 -p 22 -c 5 -t 118 -y c) hping -S -P -F -O -s -A 192.168.2.56 -p 22 -c 5 -t 118 -y d) hping -S -A -SA -P -Q -F 192.168.2.56 -p 22 -c 5 -t 118 -y |
a) hping -S -R -P -A -F -U 192.168.2.56 -p 22 -c 5 -t 118 -y
|
|
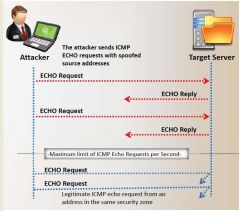
Which of the following statements defines an ICMP flood attack? (select all that apply)
a) Bogus ECHO reply packets are flooded on the network spoofing the IP and MAC address b) The ICMP packets signal the victim system to reply and the combination of traffic saturates the bandwith of the victim's network c) A DDoS ICMP flood attack occurs when the zombies send large volumes of ICMP_ECHO_REPLY packets to the victim system d) ECHO packets are flooded on the network saturating the bandwith of the subnet causing denial of service |
c) A DDoS ICMP flood attack occurs when the zombies send large volumes of ICMP_ECHO_REPLY packets to the victim system
d) ECHO packets are flooded on the network saturating the bandwith of the subnet causing denial of service |
|
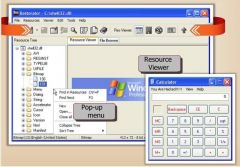
Based on the graphic, what type of Trojan is shown?
a) E-Mail Trojan b) Denial of Service Trojan c) RAT Trojan d) Destructing Trojan e) Defacement Trojan |
e) Defacement Trojan
|
|
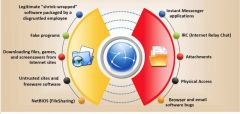
Trojan horse attacks pose one of the most serious types of threats to computer security. Based on the graphic, which is the easiest and most convincing way to infect a computer?
a) Legitimate "shrink-wrapped" software packaged by a disgruntled employee b) IRC (Internet Relay Chat) c) Netbios File Sharing d) Downloading files, games and screensavers from Internet sites. |
d) Downloading files, games and screensavers from Internet sites.
|
|
|
Which of the following is not part of the CEH Scanning Methodology?
a) Scan for vulnerabilities b) Checking for open ports c) Social Engineering attacks d) Draw network diagrams e) Banner Grabbing f) Check for live systems g) Prepare proxies |
c) Social Engineering attacks
|
|
|
TCP packets transmitted in either direction after the initial three-way handshake will have which of the following bits set?
a) ACK b) XMAS Flag c) FIN d) SYN/ACK |
a) ACK
|
|

In this type of Man-in-The-Middle (MiTM) attack, packets and authentication tokens are captured using a sniffer. Once the relevant information is extracted, the tokens are placed back on the network to gain access. (see the graphic).
a) Shoulder surfing attack b) Rainbow and hash generation attacks c) Dumpster Diving attack d) Token Injection Replay attacks |
d) Token Injection Replay attacks
|
|
|
One defense against DDoS is Throttling. What is Throttling?
a) Providers can increase bandwith on critical connections to prevent them from going down in the event of an attack b) Load balance each server in a multiple-server architecture c) Replicating servers that can provide additional failsafe protection d) Set up routers that access a server with logic to adjust incoming traffic to levels that will be safe for the server to process |
d) Set up routers that access a server with logic to adjust incoming traffic to levels that will be safe for the server to process
|
|
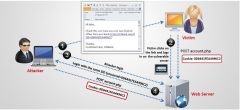
What type of session hijacking is shown in the graphic?
a) Token sniffing attack b) Session Fixation attack c) SQL Injection d) Cross-site scripting attack |
b) Session Fixation attack
|
|
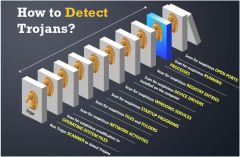
Your computer has been infected by an email tracking and spying Trojan. This Trojan infects your computer with a single file emos.sys. Which step would you perform to detect this type of trojan? (see graphic for clarification)
a) Scan for suspicious startup programs using msconfig b) Scan for suspicious network activities using Wireshark c) Scan for suspicious open ports using netstat d) Scan for suspicious drivers in c:\windows\system32\drivers |
d) Scan for suspicious drivers in c:\windows\system32\drivers
|
|
|
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
a) Buffer Overflow attack b) Cross-Site-Scripting attack c) SQL Injection d) URL Traversal attack |
b) Cross-Site-Scripting attack
|
|
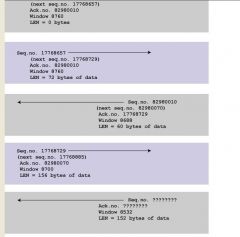
Based on the graphic, what are the next sequence and acknowledgement numbers that the router will send to the victim machine?
a) Sequence number: 82980070 Acknowledgement number: 17768885 b) Sequence number: 82980010 Acknowledgement number: 17768885 c) Sequence number: 17768729 Acknowledgement number: 82980070 d) Sequence number: 87000070 Acknowledgement number: 85320085 |
a) Sequence number: 82980070 Acknowledgement number: 17768885
|
|
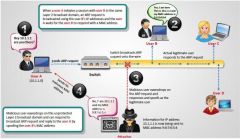
How would you defend against ARP poisoning attacks? View the graphic for clarification on the attack. (select all that apply)
a) Enable Dynamic ARP Inspection b) Enable DHCP Snooping Binding Table c) Enable MAC snooping Table d) Restrict ARP Duplicates |
a) Enable Dynamic ARP Inspection
b) Enable DHCP Snooping Binding Table |
|
|
A competitor could find job openings in your company, prepare someone to pass your interview, have you hire that person, and then they're inside your company. What's one way to prevent this?
a) Hire people through third party job agencies who will vet them for you b) Investigate their social networking profiles c) It is impossible to block these attacks d) Have thorough background checks performed on job applicants before engaging or hiring them. |
d) Have thorough background checks performed on job applicants before engaging or hiring them.
|
|

Study the SQL code in the graphic. How would you delete the OrdersTable using SQL Injection?
a) cmdshell'; 'del c:\sql\mydb\OrdersTable' // b) Chicago'; drop table OrdersTable -- c) EXEC; SELECT * OrdersTable > DROP -- d) Delete table 'blah'; OrdersTable -- |
b) Chicago'; drop table OrdersTable --
|
|
|
This attack technique is used when the Web application is vulnerable to SQL Injection, but the results of the injection are not visible to the attacker.
a) Blind SQL Injection b) Generic SQL Injection c) Unique SQL Injection d) Double SQL Injection |
a) Blind SQL Injection
|
|
|
You want to perform advanced SQL Injection against a vulnerable website. You are unable to perform command shell hacks on this server. What must be enabled in SQL Server to launch these attacks?
a) EXEC master access b) System services c) xp_cmdshell d) RDC |
c) xp_cmdshell
|
|
|
What IV size is used in WPA2?
a) 24 bit b) 128 bit c) 48 bit d) 32 bit |
c) 48 bit
|
|
|
Annie Ann has performed a XSS attack against a site and succeeded in stealing a secure cookie. She is able to replay the cookie even while the session is valid on the server. Why is this possible?
a) Any cookie can be replayed irrespective of session status b) It works because encryption in this case is performed at the application layer (single encryption key) c) It works because encryption is performed at the network layer (layer 1 encryption) d) This scenario is invalid as a secure cookie cannot be replayed |
b) It works because encryption in this case is performed at the application layer (single encryption key)
|
|
|
What type of encryption does WPA2 use?
a) SHA 160 bit b) DES 64 bit c) AES-CCMP 128 bit d) MD5 48 bit |
c) AES-CCMP 128 bit
|
|

What type of virus is shown in the graphic?
a) Cavity virus b) Metamorphic virus c) Sparse Infector virus d) Boot Sector virus e) Macro virus |
c) Sparse Infector virus
|
|

Jason is trying to analyze traffic using Wireshark. He has created the filter shown in the graphic. Based on the filter what is he trying to accomplish (capture).
a) RST, PSH/URG, FIN b) ACK, ACK, SYN, URG c) SYN, FIN, URG, and PSH d) SYN, SYN/ACK, ACK |
d) SYN, SYN/ACK, ACK
|
|

Identify the correct statement related to the Web Server installation in the graphic.
a) Lack of proper security policy, procedures and maintenance b) Misconfigured SSL certificates and encryption c) Unpatched security flaws in the server software, OS and applications d) Installing the server with default settings e) Improper file and directory permissions |
d) Installing the server with default settings
|
|
|
June is wondering if she can use anti-virus to protect herself from polymorphic viruses. Jake tells her that Anti-virus is not effective against polymorphic viruses because of how they change after each infection. Is Jake's statement true or false?
a) True b) False |
a) True
|
|
|
Which port when configured on a switch receives a copy of every packet that passes through it?
a) SPAN port b) Monitor port c) MIRROR port d) R-DUPE port |
a) SPAN port
|
|
|
If you wanted to change the password policy on your 2003 Active Directory Domain so that users could not change their passwords at regular frequency, what policies would you need to enable and enforce in Group Policy? (select two)
a) Adjust the "Enforce User Change at Next Logon" policy b) Change the "Enforce Password History" setting in the Group Policy settings module c) Adjust the "Maximum Password Age" policy d) Enforce the "Minimum Password Age" setting |
b) Change the "Enforce Password History" setting in the Group Policy settings module
d) Enforce the "Minimum Password Age" setting |
|
|
What are some reasons you would use Anonymizer when browsing the web? (select all that apply)
a) Increase your web browsing bandwith speed using Anonymizer is speed blast mode b) Post negative entries in blogs without revealing your IP identity c) To bypass blocking applications that would prevent access to web sites or parts of sites that you want to visit d) To protect your privacy and identity on the Internet |
b) Post negative entries in blogs without revealing your IP identity
c) To bypass blocking applications that would prevent access to web sites or parts of sites that you want to visit d) To protect your privacy and identity on the Internet |
|

Based on the graphic, which file has the user browsed to on the target web server?
a) file.txt b) robots.txt c) blocklist.txt d) spf.txt |
b) robots.txt
|
|
|
dDisgruntled employees are marked by several symtoms including leaving work early, calling in late or sick, being confrontational, extra time browsing the web, and always negative while finding fault with everything. They are also a big security risk. How would you deal with the disgruntled employee threat?
a) Organizations must ensure that their corporate data is centrally managed and delivered to users only when needed b) Limit Internet access, email communications, access to social networking sites and job hunting portals c) By implementing virtualization technology from the desktop to the data center, organizations can isolate different environments with varying levels of access and security to various employees d) Limit access to the applications they can run on their desktop computers and enforce strict work hour rules |
a) Organizations must ensure that their corporate data is centrally managed and delivered to users only when needed
c) By implementing virtualization technology from the desktop to the data center, organizations can isolate different environments with varying levels of access and security to various employees |
|
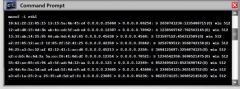
Switches maintain a CAM table that maps individual MAC addresses on the network to physical ports on a switch. The graphic shows a MAC flooding attack. What happens when a CAM table becomes full?
a) Evey packet is dropped and the switch sends out SNMP alerts to the IDS port b) The CAM overflow table will cause the switch to crash causing a Denial of Service c) the switch replaces outgoing frame switch factory default MAC address of FF:FF:FF:FF:FF:FF d) The switch then acts as a hub by broadcasting packets to all machines on the network |
d) The switch then acts as a hub by broadcasting packets to all machines on the network
|
|
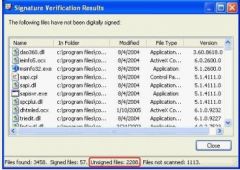
The graphic shows a Microsoft tool that verifies signed vs unsigned critical files. This is one way to verify integrity of files. Which tools perform this action and shows the output in the graphic?
a) verifier.exe b) signverif.exe c) msverif.exe d) sigverif.exe |
d) sigverif.exe
|
|

Which nmap command produced the output shown in the graphic? Assume you were trying to gain banner, server, and OS information.
a) nmap -F -sV -p 21,110,123 10.0.0.5 b) nmap -O -sV -p 21,110,123 10.0.0.5 c) nmap -T -sv -p 21,110,123 10.0.0.5 d) nmap -A -sV -p 21,110,123 10.0.0.5 |
b) nmap -O -sV -p 21,110,123 10.0.0.5
|
|
|
When viewing a SOA record, the zone Version is always the first value in the record?
a) True b) False |
a) True
|
|
|
What software can be used in War Driving to auto-map GPS coordinates to Access Points?
a) GPSmap b) GPSdrive c) Winpcap d) Microsoft Mappoint |
b) GPSdrive
|
|
|
You should prevent using which of the following C/C++ functions to help prevent buffer overflows? (select all that apply)
a) strcpy() b) strsock() c) strcat() d) streadd() |
a) strcpy()
c) strcat() d) streadd() |
|
|
Which tool can be used to recover a password protected Outlook archive?
a) Outlook Revealer b) PstPassword c) PwdRecover d) Restore |
b) PstPassword
|
|
|
What is sheepdig?
a) Process of checking physical media for virus before being used in a production computer b) Used to coordinate honeypots c) None of the above d) Used to emulate a honeypot |
a) Process of checking physical media for virus before being used in a production computer
|
|
|
What tool is used to disect html forms?
a) Whoop that trick b) Rip c) Looker d) Form Scapal |
d) Form Scapal
|
|
|
Which level in the packet signature mechanism in Netware forces the signing of all packets?
a) 2 b) 1 c) 0 d) 3 |
d) 3
|
|
|
Which is the default user account created for Oracle databases?
a) Admin b) Root c) OUTLN d) Sysop |
c) OUTLN
|
|
|
___________________ has the ability to crack smb passwords by simply listening to traffic.
a) John the Ripper b) Snapple Cracker and Popper c) L0phtcrack d) Morpheus |
c) L0phtcrack
|
|
|
Nmap and Queso can both be used for OS guessing.
a) True b) False |
a) True
|
|
|
What are the six types of social engineering?
a) Commitment b) Friendship c) Slickin it d) Reciprocation e) Social validation f) Authority g) Scarcity |
a) Commitment
b) Friendship d) Reciprocation e) Social validation f) Authority g) Scarcity |
|
|
Which exploit uses the functionality of DHTML in Internet Explorer and Microsoft Outlook?
a) Reaper Exploit b) RPC Dcom c) Corn Shell Exploit d) None of the above |
a) Reaper Exploit
|
|
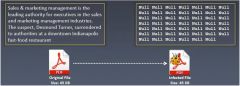
What type of virus is shown here?
a) Cavity virus b) Stealth virus c) Polymorphic virus d) Macro virus |
a) Cavity virus
|
|
|
What would you use to disable file extensions in Apache?
a) Lib_changes b) Stop_files c) mod_negotiation d) Disable_ext |
c) mod_negotiation
|
|
|
What can you enable on a switch to protect against DHCP starvation?
a) DHCP filters b) DHCP-BLOCK 1 c) ARP-Block d) DHCP snooping |
d) DHCP snooping
|
|
|
Which specially configured port on a switch can receive every packet that passes through the switch?
a) Copy Cat port b) R_DUPE port c) SPAN port d) Monitor port |
c) SPAN port
|
|
|
Which technique is used to prevent SPAM? The technique consists of slowing down responses to outside SMTP servers?
a) Spam Blocking b) Teergrubbing c) Chaining d) Sender Policy Framework |
b) Teergrubbing
|
|
|
You can examine the SOA record on a DNS server to see how long a dns cache poisoning attack would last. Essentially the TTL value.
a) This is completely true b) This is incorrect c) SOA has nothing to do with DNS d) This is partially true |
a) This is completely true
|
|
|
Which type of virus appears to be something else?
a) Polymorphic virus b) Rootkit c) Melissa Type virus d) Camouflage virus |
d) Camouflage virus
|
|
|
Concerning Netware, there is no such thing as a status of being logged in as Administrator.
a) True b) False |
a) True
|
|
|
The process of distributing incorrect IP addresses/names with the intent of diverting traffic is called what?
a) DNS poisoning b) Scanning c) Aliasing d) Arping |
a) DNS poisoning
|
|
|
Billy Joe scans his network using an XMAS scan. None of the ports scanned respond back with anythnig. What can you infer from this?
a) The ports are in stealth mode b) The ports are in state of shock c) All ports must be open because there's no response to a XMAS scan when ports are open d) If a port does not respond to an XMAS scan, the port is closed |
c) All ports must be open because there's no response to a XMAS scan when ports are open
|
|

Study the graphic. What is this ASP code vulnerable to?
a) Traversal b) Cross Site Scripting c) SQL Injection d) Parameter Injection |
b) Cross Site Scripting
|

