![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
52 Cards in this Set
- Front
- Back
|
What is the OSI reference model |
It's primary purpose is to allow different vendors' networks to interoperate |
|
|
When was the OSI model developed |
1. Work began in 1977 by ISO and OSI and was developed by 1985 2. TCP/ IP work began in 1973 to 1985 by DARPA which replaced OSI as it started getting predominance from vendors by 1985 |
|
|
Expand ISO |
International Organization of Standards |
|
|
Expand OSI |
Open Systems Interconnections |
|
|
Expand DARPA |
Defence advanced research projects |
|
|
What is the purpose of OSI model |
1. It divides network connections into smaller and simpler components, facilitating component design, development and troubleshooting 2. It allowed multiple vendor development through standardization of network components 3. It encouraged industry standardization by clearly defining what functions occur at each Layer of the model 4. It allowed various hardware and software to communicate 5. It allowed changes in one layer from affecting change in other layers |
|
|
What is bonding |
Software that maps on to another layer's protocols is called bonding |
|
|
How many layers are there in the OSI model |
7 |
|
|
What are the OSI layers |
Application, presentation, session, transport, network, data link, physical |
|
|
What are some examples of communication protocols |
DHCP, DNS, SMTP, HTTP, TFTP, SNM, RDP |
|
|
What are some examples of compression |
JPEG, GIF, mp3, WAV |
|
|
What are the different types of communication s |
Simplex, half duplex, full duplex |
|
|
What is a simplex connection |
It is a one way communication e.g. pager |
|
|
What is a half duplex communication |
2 way communication but at one direction at a time e.g. walkie talkie |
|
|
What is a full duplex connection |
2 way connection that happens both ways simultaneously e.g. mobile phones |
|
|
Which devices work on all layers? |
Network Management systems, web + server application servers, Gateweays, Network Hosts |
|
|
What is the Application Layer |
1. Provides a user interface and set of protocolsused for communication e.g. DHCP, DNS, SMTP, HTTP, TFTP( reside in applicationlayer), FTP (reside in application layer), SNMP, RDP (remote desktop) 2. Applications do not reside in the applicationlayer, it only provides an interface with the Application Layer Protocols |
|
|
What is the Presentation Layer |
1. Provides data translation and code formatting 2. How it works: Successful data transmission canoccur by converting data into standard format before transmission 2. Computers receive the formatted data andtranslate it back to the native state to read it. E.g. Extended Binary CodedDecimal Interchange Code (EBCDIC) to ASCII American Standard Code forInformation Interchange· 3. Handles process such as encryption, translation,conversion, compression e.g. JPEG, GIF, mp3 |
|
|
How does data translation and code formatting work at the Presentation Layer? |
1. Successful data transmission can occur by converting data into standard format before transmission 2.Computers receive the formatted data and translate it back to the native state to read it. E.g. Extended Binary Coded Decimal Interchange Code (EBCDIC) to ASCII American Standard Code for Information Interchange |
|
|
What is the Session Layer? |
1. Keeps different application’s data separate· 2. Keeps an eye on all sessions and downloads andmakes sure messages arrive at the right place 3. Manages connections (opens and closesconnections) 4. Dialogue between devices 5. Communication between different applicationsoccurs in 3 different modes - simplex, half duplex and full duplex |
|
|
What is the Transport Layer? |
1. Provides reliable (TCP) or unreliable (UDP)end-to-end data transport 2. Can establish a logical connection between thesending host and the destination host onan internetwork 3. Provides end to end connection by multiplexingupper-layer applications, establishing sessions, tearing down virtual circuits 4. Can provide transparent data transfer or hidedetails of network-dependent information from higher levels 5. Performs error correction before retransmit 6. segmentsand reassembles data into a single data stream i.e. services located at thislayer take all the various data from upper-layer applications, then combinethem into the same, concise data stream. 7. Works in tandem with the session layer to separatedata from different applications, also known as ‘session multiplexing.’ E.g.when you click multiple links, the client data from each browser session mustbe separate when the server application receives it. |
|
|
What is a Connection Oriented communication? |
For a reliable transport to occur, a device thatwants to transmit must first establish a connection-oriented communicationsession a remote device known as call setup or three-way handshake |
|
|
How does a Connection Oriented communication work? |
1. A virtual circuit, or a 3 way handshake, isestablished 2. It uses sequencing 3. It uses acknowledgements 4. It uses flow controls |
|
|
How does a 3 way handshake work? |
1. Steps1: Syn -> (this step requests its peerto synchronize) 2. Step 2: Syn/Ack <- (this step acknowledgesthe request and sets parameters between the hosts) 3. Ack -> (notifies the destination host thatthe connection agreement has been established and the actual connection hasbeen established) |
|
|
Draw the diagram of a 3 way handshake |

|
|
|
What are the protocols in a 3 way handshake? |
1. The segments delivered are acknowledged back to thesender upon their reception 2. Any segment not acknowledged are sent back 3. Segments are sequenced back into their properorder upon arrival at the destination 4. A manageable data flow is maintained in order toavoid congestion, overloading, or data loss |
|
|
What is a buffer? |
1. When the machine receives a flood of datagramtoo quickly for it to process (in this case the receiver), it stores them in a temporary memory section called buffer |
|
|
What is Flow control? |
1. This is a failsafe against data loss 2. It ensures data integrity at the Transport layerby allowing applications to request reliable data transport between systems |
|
|
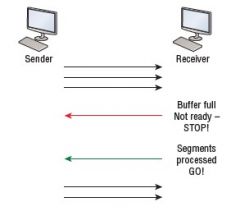
How does Flow control work? |
1. Is a safety against overflowing buffers, byproviding a way for the receiving device to control the amount of data sent bythe sender 2. In case of flood, instead of dumping and losingdata, the Transport layer can send a ‘not ready’ indicator to the sender 3. After the peer processes the data in its buffer,it sends a ‘ready’ transport indicator 4. The sender upon receiving the confirmationbegins to resend data |
|
|
Draw the diagram of a Flow control |
|
|
|
What is windowing? |
1. The quantity of data segments (in bytes), that the transmitting machine is allowed tosend without receiving an acknowledgement is called Windowing 2. If the host fails to receive all the bytes itshould acknowledge, the host can improve the communication session bydecreasing the window size E.g. for window size 1 = send1 -> <-ack1;send2-> <-ack 2; |
|
|
Draw a diagram of windowing |

|
|
|
What are Acknowledgements? |
Reliabledata delivery can be done through positive acknowledgement with retransmission |
|
|
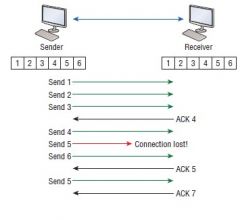
How does Acknowledgements work? |
1. the receiving machine communicates to the senderby sending an acknowledge back when it receives data 2. After sending a segment of bytes, the senderwill start a timer and will resend the data if ack is not received in theallocated time 3. E.g. Send1 -> Send 2 -> Send 3 -><-Ack 4; Send 4 -> Send 5 -> Send 6 -> <- Ack 5; Send 5 -><- Ack 7;Fragmen |
|
|
Draw the diagram for Acknowledgements |
|
|
|
What is the Network Layer? |
1. Provides logical address, which routers use forpath determination 2. IP Address: Can be expressed in binary ordecimal format, are logical identifiers. There are used when hosts reside ondifferent LAN segments or subnets 3. Provides Routing services 4. Manages device addressing and Tracks location ofdevices on the network to transport traffic between devices that aren’t locallyattached |
|
|
How does a router work? |
1. When a packet is received on a router interface,the destination IP will be checked 2. If the packet isn’t destined for that particularrouter, it will look up the packet’s destination network address in the routingtable. Once the router choses an exit interface, the packet will be sent tothat interface to be framed, and sent out on the local network. 3. If the router can not find an entry for thepacket’s destination network in the routing table, it will drop the packet. |
|
|
What are the different packets in a Network Layer? |
Dataand Route update packets are the two type of packets used at the Network Layer |
|
|
How does Data packet work? |
1. Used to transport user data through theinternetwork 2. Protocols used to support data traffic arecalled routed protocols, e.g. IPv4 and IPv6 |
|
|
How does Route Update packet work? |
1. The packets are used to update neighboringrouters about the networks connected to all the routers within the internetwork 2. Protocols that send route update packets arecalled routing protocols e.g. RIP, RIPv2, EIGRP, OSPF 3. Routing protocols are used to help build andmaintain routing tables |
|
|
What is a Network Address? |
1. A router must maintain a routing table forindividual routing protocols because each routed protocols keeps track of anetwork with a different address scheme 2. E.g. routing tables for IP and IPv6are completely different |
|
|
What is an Interface? |
It is the exit interface a packet will take whendestined for a specific network |
|
|
What is Metric? |
1. The distance to the remote network 2. Different routing protocols use different waysto calculate it e.g. RIP (routing interface protocol) uses hop count i.e. thenumber of routers a packet passes through en route to a remote network |
|
|
What is Data Link layer? |
1. It provides for the physical transmission of thedata and handles error notification, network topology, flow control i.e. ensurethat messages are delivered to the proper place on a LAN using hardware addressand will translate messages from the network layer into bits for the Physicallayer to transmit 2. Combines packets into bytes, and bytes intoframes. It adds a customized header containing the hardware destination andsource address 3. Provides access to media using MAC address 4. IEEE Ethernet Data Link layer has two sub layers |
|
|
What are the two sub layers of Data Link layer? |
MAC layer and Logical Link control layer |
|
|
What is MAC layer? |
§ Defines how packets are placed on the media i.e.physical address as well as logical topology |
|
|
What is MAC address? |
Hexadecimal number identifying the physicaladdress of a host |
|
|
What is LLC? |
1. Responsible for identifying network layerprotocols and then encapsulating them. An LLC header tells the Data Link Layerwhat to do with a packet once a frame is received e.g. a host receives a frameand looks at the LLC header to see where the packet is destined e.g. the IPprotocol at the Network Layer 2. Provides flow control and sequencing of bits,error detection |
|
|
· How does a switch/bridge work? |
1. It reads each frame that passes through thenetwork 2. Puts the source hardware address in a filtertable and keeps track of which port the frame as received on 3. This information is what helps the machinedetermine the location of the specific sending device 4. The frames get forwarded only to the segmentwhere the destination hardware address is located 5. If the destination device is on the same segmentas the frame, the switch will block the segment from going to any othersegment. If the destination is on a different segment, the frame can betransmitted only to that segment (this is called transparent bridging) 6. If a frame with destination hardware address isn’tfound in the filter table, it will forward the frame to all connected segments 7. If the unknown device replies, the switch will updateits location in its table. |
|
|
What is the Physical layer? |
1. Moves bits between devices (sends and receives) 2. Specific voltage, wirespeed, and pinout ofcables 3. Hubs, repeaters 4. Physical topology 5. Communicates directly with the various types ofactual communication media e.g. audio tones, state transitions. Specificprotocols are needed for each type of media to describe the proper bit patternsto be used, how data is encoded into media signals, and the various qualitiesof the physical media’s attachment interface 6. The Physical Layer specifies the electrical,mechanical, procedural, and functional requirements for activating,maintaining, and deactivating physical link between end systems 7. Identification between Data Terminal Equipment(DTE) and Data Communication Equipment (DCE) |
|
|
What are Data Terminal Equipment (DTE) and Data Communication Equipment (DCE) |
1. DCE is usually located at the service provider 2. DTE is the attached equipment 3. The services available to the DTE are most oftenaccessed via a modem or channel service unit/data service unit (CSU/DSU) |
|
|
What are hubs? |
A hub is a multiport receiver i.e. receives a digitalsignal, reamplifies or regenerates the signal, then forwards the signal out theother ports without looking at the data, except to the one from which it was received |

