![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
35 Cards in this Set
- Front
- Back
|
The following address (2001:0002:0000:0000:0000:abcd:0bcd:0fea) can be simplified to __________ |
2001:2::abcd:bcd:fea |
|
|
How will a stateful packet inspection (SPI) firewall handle an incoming packet containing a TCP SYN segment |
Process it through the Access Control List (ACL) |
|
|
The Frequency Spectrum is divided into _________ which are further divided into _________ |
Service bands, channels |
|
|
Attackers only need to find a single weakness to break in. Consequently, companies must ________ |
Have comprehensive security |
|
|
Which offers stronger security? WPA, 802.11i or both are equal |
802.11i |
|
|
Modern Ethernet networks use which kind of topology? |
Hierarchical Star |
|
|
What IEEE working group creates wireless LAN standards? |
IEEE 802.11 |
|
|
You are setting up an Ethernet LAN in a small office space. The longest run of cabling you need is 70 meters. Your network needs a rated speed of 1 Gbps. You are considering using either 100Base-TX, 1000Base-T or 1000Base-SX. Which one(s) will work with your setup? |
1000Base-T and 1000Base-SX |
|
|
In digital signaling there is (are) ________ state(s) |
A finite number of |
|
|
If an 802.11n access point and an 802.11g client communicate, the communicate using _________ |
802.11g |
|
|
A wireless host located at Company A sends a packet to a server on Company A's wired Ethernet LAN via an access point. How many frames will be involved in this one-way transmission? |
2 |
|
|
Which of the following is usually optional in access point operation? |
RTS/CTS |
|
|
When a wireless computer wishes to communicate with a server, _________ can secure the communication against evil twin attacks |
VPN |
|
|
Name and describe two of the five wireless propagation problems we discussed |
Absorptive attenuation - the more moisture, the weaker the signal. |
|
|
What happens if two nearby access points use the same channel? |
The will interfere with each other |
|
|
A binary signal is also a digital signal |
True |
|

The following network design is acceptable for a given 3-site company; however, it needs to be updated to ensure no network interruptions will occur if one of the 3 transmission lines goes down. Based on the textbook and class discussions, you need to figure out how to change the capacity on these transmission lines to support a possible failure on the 55Mbps transmission line (Jensen - Sallyn). Describe your modification by stating the new capacities for the three links. |
Smith - Jensen: 3.055Gbps |
|
|
A channel extends from 55MHz to 60MHz. Its bandwidth is _________ |
None are correct (55, 60, 65) |
|
|
An attacker must break through two firewalls to get to a host. This illustrates the principle called ___________ |
Defense in depth |
|
|
When one pair in a UTP cord interferes with signals in other pairs, this is ___________ |
Crosstalk interference |
|
|
As a signal propagates down a UTP cord, greater propagation distance will result in more noise errors, even if the average noise level is constant |
True |
|
|
Users of an access point share the transmission capacity of the access point. The throughput the share is called __________ |
Aggregate throughput |
|
|
We discussed two advantages of using the 5GHz frequency over the 2.4GHz frequency. What is one of the advantages? |
Larger bandwidth |
|
|
What does the Wi-Fi Alliance call 802.11i? |
WPA2 |
|
|
How will a stateful packet inspection (SPI) firewall handle an incoming packet containing a TCP segment which is an acknowledgement? |
Pass it if it is part of an approved connection |
|
|
When untwisting wire pairs in UTP, we do not untwist more than 1.25cm (a half inch) at their ends. This helps reduce a type of interference known as _____________ |
Terminal crosstalk interference |
|
|
In the IPv4 address 1.2.3.4, what is the network part? |
We cannot say |
|
|
How many wires will you find in a Cat 5e UTP cord? |
8 |
|
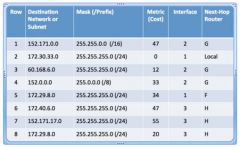
A packet with destination IP address 152.171.6.12 arrives at a router. Using the routing table below, which row will the router select to determine where to send the packet? |
1 |
|
|
Name and describe the primary propagation problem with Multimode Fiver Optic transmission lines? |
Modal dispersion - light rays enter the cord at different angles (modes) and therefore, travel different distances as they bounce around. The signals may overlap and arrive out of order. This can cause them to be unreadable |
|
|
IEEE 802.11n uses what two unlicensed bands for data transmission? |
2.4GHz and 5GHz |
|
|
In what mode of 802.11i operation is a central authentication server used? |
802.1X mode |
|
|
An arriving packet has the destination IP address 152.143.180.14. What is the result if we mask it with 255.255.224.0? |
152.143.160.0 |
|
|
The 20.4GHz band supports _________ nonoverlapping 20MHz channels. |
3 |
|
|
What IEEE working group creates Ethernet LAN standards? |
IEEE 802.3 |

