![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
105 Cards in this Set
- Front
- Back
|
Infrequent or specialized transactions
|
General (ch 2)
|
|
|
Repetitive transactions
E.g., sales transactions |
Specialized (ch 2)
|
|
|
Summary level data for each:
Asset, liability, equity, revenue, and expense |
General (ch 2)
|
|
|
Detailed data for a General Ledger (Control) Account that has individual sub-accounts
Accounts Receivable Accounts Payable |
Subsidiary (ch 2)
|
|
|
ERP Advantages
|
integration, done once, monitoring, control, standardizes proc., customer service, manufacturing:
Integration of an organization’s data and financial information Data is captured once Greater management visibility, increased monitoring Better access controls Standardizes business operating procedures Improved customer service More efficient manufacturing (ch 2) |
|
|
ERP Disadvantages
|
Time, cost, disruptive, complex, resistance:
Time-consuming to implement Cost Changes to an organization’s existing business processes can be disruptive Complex Resistance to change (ch 2) |
|
|
Entity consists of:
|
attributes
fields records file (ch 2) |
|
|
Define entity, attributes, fields records and file
|
entity is a Person, place, or thing (Noun) and something an organization wishes to store data about
Attributes - Facts about the entity Fields - Where attributes are stored Records - Group of related attributes about an entity File - Group of related Records (ch 2) |
|
|
Items numbered consecutively
|
Sequence
(ch 2) |
|
|
Specific range of numbers are associated with a category
10000–199999 = Electric Range |
Block
(ch 2) |
|
|
Positioning of digits in code provide meaning
|
Group
(ch 2) |
|
|
Letters and numbers
Easy to memorize Code derived from description of item |
Mnemonic
(ch 2) |
|
|
Type of block coding
|
Chart of accounts
(ch 2) |
|
|
Infrequent or specialized transactions
|
General
(ch 2) |
|
|
Repetitive transactions
E.g., sales transactions |
Specialized
(ch 2) |
|
|
Summary level data for each:
Asset, liability, equity, revenue, and expense |
General
(ch 2) |
|
|
Detailed data for a General Ledger (Control) Account that has individual sub-accounts
Accounts Receivable Accounts Payable |
Subsidiary
(ch 2) |
|
|
Types of AIS storage:
|
Paper-based
Ledgers Journals Computer-based (ch 2) |
|
|
Well-designed source documents can ensure that data captured is
|
Accurate
Provide instructions and prompts Check boxes Drop-down boxes Complete Internal control support Prenumbered documents (ch 2) |
|
|
Source data is captured
|
In machine-readable form
At the time of the business activity E.g., ATM’s; POS (ch 2) |
|
|
Data are collected on source documents
|
E.g., a sales-order form
The data from paper-based will eventually need to be transferred to the AIS (ch 2) |
|
|
Turnaround document
|
Usually paper-based
Are sent from organization to customer Same document is returned by customer to organization (ch 2) |
|
|
As a business activity occurs data is collected about:
|
(activities, resources, people)
Each activity of interest The resources affected The people who are participating (ch 2) |
|
|
Data processing cycle
|
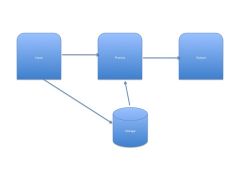
Data processing cycle:
(ch 2) |
|
|
(T/F) A chart of accounts provides the user with a list of general ledger accounts.
|
True
(ch 2) |
|
|
(T/F) An audit trail can only assist external auditors.
|
False
(ch 2) |
|
|
(T/F) A master file is analogous to a journal in a manual system.
|
False
The master file is analogous to a ledger in a manual system. (ch 2) |
|
|
(T/F) Accounts receivable generally has a sub-ledger for many companies.
|
True
(ch 2) |
|
|
(T/F) Data processing is comprised of four elements and can be represented by the acronym CRUD. The R in CRUD stands for Revise.
|
False
(ch 2) |
|
|
A set of two or more interrelated components interacting to achieve a goal
|
System (ch 1)
|
|
|
Occurs when components act in their own interest without regard for overall goal
|
Goal Conflict (ch 1)
|
|
|
Occurs when components acting in their own interest contribute toward overall goal
|
Goal Congruence (ch 1)
|
|
|
Facts that are recorded and stored.
Insufficient for decision making. |
Data (ch 1)
|
|
|
Processed data used in decision making.
Too much information however, will make it more, not less, difficult to make decisions. This is known as Information Overload. |
Information (ch 1)
|
|
|
Benefits of information
|
Reduce Uncertainty
Improve Decisions Improve Planning Improve Scheduling (ch 1) |
|
|
Costs of information
|
Time & Resources
- Produce Information - Distribute Information (ch 1) |
|
|
What characteristics makes information useful?
|
accessible
complete relevant reliable timely understandable verifiable (ch 1) |
|
|
“The capacity of information to make a difference in a decision by helping users to form predictions about the outcomes of past, present, and future events or to confirm or correct prior expectations.”
|
Relevant (ch 1)
|
|
|
Available when needed (see Timely) and in a useful format (see Understandable).
|
Accessible (ch 1)
|
|
|
“The quality of information that assures that information is reasonably free from error and bias and faithfully represents what it purports to represent.”
|
Reliable (ch 1)
|
|
|
“The inclusion in reported information of everything material that is necessary for faithful representation of the relevant phenomena.”
|
Complete (ch 1)
|
|
|
“Having information available to a decision maker before it loses its capacity to influence decisions.”
|
Timely (ch 1)
|
|
|
“The quality of information that enables users to perceive its significance.”
|
Understandable (ch 1)
|
|
|
Business process, systems working toward organizational goals are:
|
Financing
Revenue Expenditure Production HR (ch 1) |
|
|
AIS purpose
|
Collect, process, store, and report data and information (ch 1)
|
|
|
If Accounting = language of business, AIS = _______
|
information providing vehicle (ch 1)
|
|
|
Components of an AIS
|
people
procedures instructions data software IT internal control and security (ch 1) |
|
|
AIS and business functions
|
collect/store data (about active., resources, personnel)
transform data into info (mgmt can plan, execute, ctl, veal) provide control/safeguard (data, assets) (ch 1) |
|
|
What value does AIS add; what's improved?
|
quality
cost reduced efficiency sharing knowledge supply chain internal ctl decision making (ch 1) |
|
|
How does AIS improve decision making?
|
identify (situations req action)
provide (alt choices, accurate and timely info) uncertainty reduced feedback on prev decisions (ch 1) |
|
|
What is a value chain?
|
The set of activities a product or service moves along before as output it is sold to a customer
At each activity the product or service gains value (ch 1) |
|
|
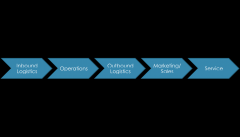
Value chain primary activities (in order of steps)
|
inbound logistics (receiving and storing materials)
operations (manufacturing, repackaging) outbound logistics (distribution, shipping) marketing and sales (advertising, selling) service (repair, maintenance) (ch 1) |
|
|
Name the value chain support activities (4)
|
Firm infrastructure
HR Technology Purchasing (ch 1) |
|
|
What is the sequence of the supply chain? (there are 5)
|
Raw materials supplier
manufacturer distributor retailer consumer (ch 1) |
|
|
______ requires independent auditors to understand all internal control procedures.
Documentation assists in auditor understanding and documentation of their understanding |
SAS 94
(ch 3) |
|
|
Sarbanes-Oxley states that management:
Is responsible for ____, _____ Both management and external auditors need to document and test ____ |
internal control system
assessing the effectiveness of the IC System IC System (ch 3) |
|
|
Represents a source of data or input into the system
or Represents a destination of data or output from the system |
entity (ch 3)
|
|
|
Movement of data among:
Entities (sources or destinations) Processes Data stores Label should describe the information moving |
data flows (ch 3)
|
|
|
Represents the transformation of data
|
process (ch 3)
|
|
|
Represents data at rest
|
data store (ch 3)
|
|
|
data flow diagram levels
|
context
level-0 level-1 (ch 3) |
|
|
Highest level (most general)
Purpose: show inputs and outputs into system Characteristics: one process symbol only, no data stores |
Context
(ch 3) |
|
|
Purpose: show all major activity steps of a system
Characteristics: processes are labeled 1.0, 2.0, and so on |
Level-0
(ch 3) |
|
|
documentation tools
|
data flow diagram
document flowchart system flowchart program flowchart (ch 3) |
|
|
Illustrates the flow of documents through an organization
Useful for analyzing internal control procedures |
Document flowchart
(ch 3) |
|
|
Logical representation of system inputs, processes, and outputs
Useful in systems analysis and design |
System flowchart
(ch 3) |
|
|
a graphical description of the sequence of logical operations a computer performs as it executes a program
|
Program flowchart
(ch 3) |
|

symbols
|
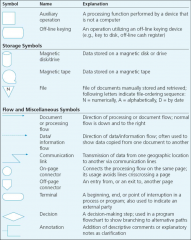
symbols
(ch 3) |
|
|
depict the relationships among system input, processing, and output
|
system flowcharts
(ch 3) |
|
|
threats to AIS
|
Natural disasters
terrorism human error computer crime (ch 3) |
|
|
Gaining an unfair advantage over another person
|
fraud
(ch 5) |
|
|
examples of fraud
|
A false statement, representation, or disclosure
A material fact that induces a person to act An intent to deceive A justifiable reliance on the fraudulent fact in which a person takes action An injury or loss suffered by the victim (ch 5) |
|
|
Individuals who commit fraud are referred to as _____
|
white-collar criminals
(ch 5) |
|
|
intentional or reckless conduct, whether by act or omission, that results in materially misleading financial statements” (The Treadway Commission).
|
Fraudulent financial reporting
(ch 5) |
|
|
Theft of a companies assets.
|
Misappropriation of assets
(ch 5) |
|
|
Largest factors for theft of assets:
|
Absence of internal control system
Failure to enforce internal control system (ch 5) |
|
|
Reasons for Fraudulent Financial Statements
|
Deceive investors or creditors
Increase a company’s stock price Meet cash flow needs Hide company losses or other problems (deceive, stock, cash, hide) (ch 5) |
|
|
Treadway Commission Actions to Reduce Fraud
|
Establish environment which supports the integrity of the financial reporting process.
Identification of factors that lead to fraud. Assess the risk of fraud within the company. Design and implement internal controls to provide assurance that fraud is being prevented. (environment, identify, assess risk, internal controls) (ch 5) |
|
|
Whose responsibility is it to detect fraud?
|
auditors
(ch 5) |
|
|
auditor's responsibilities
|
understand fraud
discuss risks identify, assess, respond to risk evaluate audit test results determine impact on fin stmts of fraud doc/communicate findings incorp. technolog. focus (ch 5) |
|
|
What three conditions are present when fraud occurs?
|
pressure
opportunity rationalization (ch 5) |
|
|
motivation or incentive to commit fraud
|
pressure
(ch 5) |
|
|
types of pressure
|
employee: finan, emot, lifestyle
financial: industry conditions, mgmt charac (ch 5) |
|
|
Condition or situation that allows a person or organization to commit or conceal the fraud or convert the theft to personal gain
|
opportunity
(ch 5) |
|
|
ways of concealing fraud
|
lapping
kiting (ch 5) |
|
|
Justification of illegal behavior
|
rationalization
(ch 5) |
|
|
Three justifications for illegal behavior
|
Justification
I am not being dishonest. Attitude I don’t need to be honest. Lack of personal integrity Theft is valued higher than honesty or integrity. (ch 5) |
|
|
Any illegal act in which knowledge of computer technology is necessary for:
Perpetration Investigation Prosecution |
computer fraud
(ch 5) |
|
|
Facts about computer fraud
|
Definition is not agreed on
Many go undetected High percentage is not reported Lack of network security Step-by-step guides are easily available Law enforcement is overburdened Difficulty calculating loss (ch 5) |
|
|
Alteration or falsifying input
|
Input Fraud
(ch 5) |
|
|
Unauthorized system use
|
Processor Fraud
(ch 5) |
|
|
Modifying software, illegal copying of software, using software in an unauthorized manner, creating software to undergo unauthorized activities
|
Computer Instructions Fraud
(ch 5) |
|
|
Illegally using, copying, browsing, searching, or harming company data
|
Data Fraud
(ch 5) |
|
|
Stealing, copying, or misusing computer printouts or displayed information
|
Output Fraud
(ch 5) |
|
|
Data flow diagrams creation guidelines
|
understand - the system
ignore - certain aspects of the system (ch 5) |
|
|
A written step by step explanation of system components and interactions
|
narrative description
(ch 5) |
|
|
movement of data among processes, stores, sources and destinations
|
data flow (ch 3)
|
|
|
transformation of data in a data flow diagram
|
processes (ch 3)
|
|
|
helps understand the flow of documentation
|
system documentation technique (ch 3)
|
|
|
What is the audit goal?
|
To see if the financial statements are accurate (ch 3)
|
|
|
For fraud, a civil tort, to occur what are the conditions?
|
false statement, representation or disclosure
intent to deceive justifiable reliance injury/loss must occur - suffered by the victim (ch 5) |
|
|
What is the #1 reason for misappropriation of assets?
|
failure to enforce internal control (ch 5)
|
|
|
3 steps to fraud
|
commit
conceal convert (into personal gain) (ch 5) |
|
|
scheme where perpetrator steals cash/checks from customer A, pays off customer A's account with checks from customer B and pays off customer B's account with checks from customer C
|
lapping (ch 5)
|
|
|
scheme where cash is created using the lag between the time a check is deposited and the time it clears the bank.
Eg: Creating cash by depositing $1000 check from bank B in bank C and withdrawing the funds. If it takes two days for the check to clear bank B, he has created $1000 for two days. After two days perp deposits a $1000 check from bank A into bank B to cover for two more days |
kiting (ch 5)
|

