![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
15 Cards in this Set
- Front
- Back
|
To define a domain-wide account policy you do the following: |
1. a. GPMC or group policy management console |
|
|
Kerberos is the default mechanism for _____(a)_____ domain users in Windows Server (named after the 3-headed dog-monster guarding the crossing over the River Styxx in Hell).
It is a ___(b)___-based system that allows domain access by using a Key ____(c)____ Center (KDC), used to issues Kerberos tickets to users, computers, or network services. These tickets have a finite lifetime and are based in part on system time clocks. They have a 5-minute ____(d)____ tolerance between the client and DC. |
a - authenticating
b - ticket c - Distribution d - clock-skew Pg 161 |
|
|
Local policies are local to a computer. When they are part of a GPO in AD, they affect the ________ security settings of computer accounts to which the GPO is applied. |
local |
|
|
To track what a user does on his computer you would define __________ policies in a GPO applied to that PC. |
local |
|
|
In auditing, tracking successful events allows you to find out how often resources are ____a_____. Tracking failed events can help determine when security breaches should be resolved. Auditing is turned ___b___ by default, so you must decide what will get audited. If an event is an AD event such as a user logon, it gets written to ____c____. On the other hand, local computer events such as accessing files gets written to the local computer's logs. |
a - accessed
b - off c - the domain controller |
|
|
Auditing best practices include: |
a - necessary
b - Full c - Archive d - number |
|
|
The two main requirements necessary to set up and administer an audit policy are:
1. Possession of the Manage A___(a)___ and Security Log user right for the computer on which you want to configure a policy or review a log, granted by default to admins. 2. Any files or folders to be audited must be on ___b___ volumes. |
a - Auditing
b - NTFS |
|
|
The Event Log Policy settings area allows for configuration of the maximum __a__ size, ret___(b)___, and ac___(c)___ rights for each log. The number and type of logs varies depending on what roles are installed on the server. Pg 167
|
a - log
b - retention c - access |
|
|
R____(a)____ Groups can be used to set exactly who is a member of security-sensitive groups, such as the administrators group. Once this is set, if administrators are added to the group outside this setting (e.g., in AD Users & Computers), they will be removed during the next cycle and replaced with only those specified in the r___(a)___ group. |
a - Restricted |
|
|
T_____(a)____ing refers to an administrative template setting that continues to apply until it is reversed using a policy that overwrites the setting. Put another way, it is a group policy setting that is not removed when it reverts to "Not Configured" |
a - Tatooing, pg 173 |
|
|
(Kerberos Policy settings) |
a - Group Policy |
|
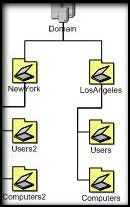
Your company's network is a single AD domain with 2 sites - LA and NY with the displayed OU hierarchy. The NY OU has 2 GPOs applied, GPO-User and GPO-computer, to the users and computers OUs respectively. Users report logging in is very slow so you need to reduce the amount of time it takes to process GPOs. What should you do? a - configure Windows Management Interface (WMI) filtering for the GPO-User GPO b - disable computer config for the GPO-User GPO; disable user config for the GPO-computer GPO. c - configure WMI filtering for the GPO-Computer GPO. d - Link GPO-User to the Users2 OU; link GPO-Computers to the Computers2 OU. |
b. Explanation: - GPO-User GPO doesn't need to process computer-specific settings and GPO-Computer GPO doesn't need to process user-specific settings. Limiting which containers are processed will speed up GPO processing. - While WMI filtering provides a way to limit which computers or users receive a GPO, they increase processing time, impacting performance instead of improving it. - There is no need for filtering in this instance because the GPOs are designed with specific targets (e.g. GPO-Users for users)
|
|
|
A new corporate security policy requires that all changes to user, computer, and group objects must be logged to the security log. For modification, both the old and new values must be recorded. You need to ensure that the domain complies with the security policy. Which two actions should you take? a - enable audit directory service access on the default domain controllers GPO b - modify the advanced security properties of the domain c - enable audit directory service access on the default domain GPO d - execute the auditpol command e - modify the advanced security properties for each OU |
B and D Explanation: - The auditpol command enables auditing for the directory service changes subcategory of the "audit directory service access" GPO audit setting. - To enable success auditing, execute "auditpol /set /subcategory:"directory service changes" /success:enable - You also need to modify the advanced security properties of the domain - this is how you create the system access control list (SACL) |
|
|
(derived from practice exam) You need to apply a fine-grained password policy to all network administrators because a new company security policy requires their passwords to be at least 10 characters long. Which one of the following would you use for the task: a - assign password policy to a OU b - assign password policy to a global group c - assign password policy to a domain local group d - define password inside GPO |
b global group Explanation: - Fine-grained password policies can be assigned to a user or global group. - They can't be defined in or assigned to OUs, domain local groups, or GPOs. |
|
|
(practice exam) Your company's network is configured as a single domain with 4 sites. All DCs are running Server 08. Clients are running Windows XP, Vista, or 7. Your company uses a large number of GPOs to manage config settings. A Windows XP Pro box named Admin1 is being used to manage, create, and edit GPOs. You analyze network traffic and disk space consumption and determine that GPOs are using a large amount of both. You need to reduce disk space consumption and bandwidth used by GPOs while using only the upgrades necessary to meet the requirements. What should you do? (Each correct answer presents part of the solution. Choose two) a - store the ADM files in a central store b - upgrade all client computers to Windows Vista or later c - store the ADMX files in a central store d - upgrade Admin1 to Windows Vista or later e - store the ADMX and ADM files on Admin1 |
c and d Explanation: - ADM files are stored in each GPO, not a central store (a subfolder in SYSVOL) - Upgrading all clients to Vista would not help in this situation. - ADMX files are used to define group policy settings. They reside in the central store of DCs, not in GPOs. Therefore they are not distributed throughout the network (like ADM files are). This dramatically will lessen network usage by GPOs. - Admin1 needs to be upgraded to at least Vista to support ADMX files. - ADM files can't be stored on an administrative workstation. |

