![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
248 Cards in this Set
- Front
- Back
|
3 types of access controls: |
type 1: what you have(lock and key, CaC) type 2: what you know ( information, passwords) type 3: what you are (biometrics) |
|
|
What is accountability? |
the idea that user should be accountable to the actions performed under his/her name. |
|
|
What is Kerberos? |
Client sends login information to KDC (Key Distribution Center), which verifies a clients credentials and sends request to TGS (ticket granting server), followed by a TGT (ticket granting ticket) to the client. |
|
|
What is an SYN flood? |
Sending TCP packets to deny availability
|
|
|
What is an ICMP flood? |
Sending ICMP (usually ping) packets to deny availability.
|
|
|
What is smurfing? |
A special ICMP flood attack that braodcasts ICMP requests. |
|
|
Buffer Overflow: |
Sending a malformed packet that overflows a memory address to deny availability and possibly gain privileges |
|
|
Backdoor: |
Gain access through a secret program (ex. trojan horse) |
|
|
Sniffing: |
Read information off the network
|
|
|
Spoofing: |
Hiding or disguising an address to make it appear that the requests come from another source. |
|
|
Man n the middle |
Intercepting packets and changing the contents. (denies confidentiality and integrity.) |
|
|
Replay |
session key sniffed and then used.
|
|
|
How does a virus propagate? |
through user action, usually by email. |
|
|
How does a worm propagate? |
self-propagating and uses exploits |
|
|
L2TP operates on the _____ layer. |
Data-Link |
|
|
IPSec operates on the ____ layer and has 2 protocols: ____ and ___. |
network layer, AH and ESP |
|
|
what are S/MIME, MOSS. PEM and PGP? |
email security programs. |
|
|
What is an applet? |
Programs that run in a browser such as Java and activeX. |
|
|
what is the difference between S-HTTP and SSL? |
S-HTTP is connectionless while SSL is connection oriented. |
|
|
What does disk spanning allow? |
Allows a file system to be spread over multiple physical drives. |
|
|
What is WTLS? |
WAP's built in security system and operates over TLS |
|
|
What is WEP? |
a weak security system for wireless LANs and operates on layers 1 and 2 (physical and data)
|
|
|
What is cladding? |
the glass insulator in the fiber optic cable
|
|
|
What is the key anagement protocol that uses EAP? |
802.1x |
|
|
Which type of cabling is said to be shielded against EMI? |
STP cabling |
|
|
Circuit level gateway: |
Maintains state information (connection based) |
|
|
Application level gateway: |
examines each packet coming in for content
|
|
|
What is a proxy server? |
special application level gateway that ensures no direct connection between an untrusted and trusted network. |
|
|
What is an ACL? |
the list that defines the rules that a packet filtering firewall follows |
|
|
Screening router: |
a router between the trusted and untrusted |
|
|
Screened host gateway |
A bastion host that can examine traffic between trusted and untrusted |
|
|
Dual-homed gateway |
a bastion host and router between trusted and untrusted |
|
|
Screened subnet: |
A bastion host (DMZ zone) between two routers |
|
|
Whats the difference between and active IDS and a passive IDS? |
active finds and attempts to circumvent threats, a passive finds threats and alerts administrator |
|
|
How does a host based IDS operate? |
requires special software to be installed on each node |
|
|
Knowledge based IDS: |
works using signatures and known attacks |
|
|
Behavior based IDS: |
works by analyzing baseline v.s real time network traffic |
|
|
what is relaying? |
the behavior of SMTP servers that will send a message from any source (should be disabled) |
|
|
What do anonymous services do? |
allow access without authentication |
|
|
What is AES> |
a symmetric algorithm based on Rijndael Block Cipher |
|
|
What do block ciphers do? |
Encrypt clear text block by block while stream ciphers encrypt in real time |
|
|
Name some symmetrical algorithms |
DES, 3DES, AES and IDEA |
|
|
Name some asymmetric algorithms |
Diffie-Hellman, RSA and El Gamel |
|
|
What are the three types of backups? |
Full, Differential and Incremental |
|
|
What is a differential backup? |
Only the data that has changed since the last full backup was done is backed up
|
|
|
What is an incremental backup? |
Only the data that has changed since the last incremental or full backup is backed up |
|
|
What is MTD? |
Maximum tolerable downtime- the greatest amount of time a system can withstand being un-operational |
|
|
DES: |
sym. 64 bit (56+8 parity) very weak 3DES |
|
|
3DES |
sym. 192 bit (168bit + 24 parity) Moderate AES |
|
|
AES |
sym. Variable (128, 192, 256) strong N/A |
|
|
El Gamel |
N/A very strong |
|
|
MD5 Hash |
Rivest MD5 block hash 512 bit block processing/128 it digest strong MD6 |
|
|
SHA-1 |
512 bit processing/160 bit digest very strong |
|
|
That is CCMP? |
counter mode with cipher block chaining messaging authentication code protocol.
a wrapper that uses 128 bit AES encryption |
|
|
An achievement providing worldwide internet security was the signing of certificates associated with which protocol? |
SSL |
|
|
A chief Information Security officer (CISO) wants to implement two-factor authentication within the company. What will fulfill his requirements? |
USB token and PIN |
|
|
What can a security administrator implement on mobile devices that will help prevent unwanted people from viewing the data if the device is left unattended? |
screen lock |
|
|
What would a security manager implement in order to ID a problem between two systems that are not communication properly? |
Protocol analyzer |
|
|
What can result in significant administrative overhead from incorrect reporting? |
false positives |
|
|
A security admin wants to perform routine tests in the network during working hours when certain apps are being accessed. What will allow the S.A. to test the lack of security controls for those applications with the least impact to the system? |
vulnerability scan |
|
|
What risk concept requires an organization to determine the number of failures per year? |
ALE |
|
|
A system security analyst using an enterprise monitoring tool notices an unknown internal host exfiltrating files to several foreign IP addresses. What would be an appropriate mitigation technique? |
rogue machine detection |
|
|
what are three primary security control types that can be implemented? |
operational, technical, and management |
|
|
The helpdesk reports increased call from clients reporting spiked in malware infections on their systems. What phases of incident response is MOST appropriate as a first response? |
Identification |
|
|
What are the steps to incident response? |
Identification, Containment, Validation, Eradication, Recovery, Follow-up. |
|
|
Which protocol operates at the highest level of the OSI model? |
SCP |
|
|
Joe, the S.A has been asked to calculate the annual loss expectancy (ALE) for a $5000 dollar server, which often crashes. In the past year, the server crashed 10 times, requiring a system reboot to recover with only 10% loss of data or function. What is the ALE of this server? |
$5000 |
|
|
What should an administrator implement to research current attack methodologies? |
Honeypot |
|
|
What can be implemented in hardware or software to protect a web server from cross-site scripting attacks? |
Web application firewall |
|
|
Which means of wireless authentication is easily vulnerable to spoofing? |
MAC filtering |
|
|
The BEST methods for a web developer to prevent the website application code from being vunerable to cross=site request (XSRF) are to ____ and ____. |
validate and filter input on the server side and the client side; restrict and sanitize use of special characters in input and URLs |
|
|
Jane, a security administrator, needs to implement a secure wireless authentication method uses a remoter RADIUS server for authentication. Which method should Jane use? |
LEAP
|
|
|
Computer evidence at a crime scene is documented with a tag stating who had possession of the evidence at a given time. What does this illustrate? |
chain of custody |
|
|
A net admin is configuring access control foe the sale department which has high employee turnover. What is BEST suited when assigning user rights to individuals in the sales department? |
group based privileges |
|
|
What is being tested when a company's payroll server is powered off for eight hours? |
continuity of operations plan |
|
|
A security analyst is reviewing an IRC channel and notices that a malicious exploit has been created for a frequently used application. She notifies the software vendor and asks them for remediation steps, but is alarmed to find that no patches are available to mitigate this vulnerability. What is the best description of this exploit? |
Zero-day exploit |
|
|
A security admin has concerns about new types of media which allow for the mass distribution of personal comments to a select group of people. To mitigate the risks involved with this media, employees should receive training on what? |
social networking |
|
|
A net admin is responsible for securing applications against external attacks. Every month, the underlying operating system is updated. There is no process in lace for the other software updates. What could MOST effectively mitigate these risks? |
Application patch management |
|
|
A network engineer is designing a secure tunneled VPN. Which protocol would be the MOST secure? |
IPSec |
|
|
Which implementation steps would be appropriate for a public wireless hot spot? |
open system authentication |
|
|
An integral step in deploying a WPA=2 enterprise wireless network |
install a digital certificate on the authentication server |
|
|
Which control would allow a company to reduce the exposure of sensitive systems from unmanaged devices on internal networks> |
802.1x |
|
|
What preventative control would be appropriate for responding to a directive to reduce the attack surface of a specific host? |
disabling unnecessary services |
|
|
A security manager must remain aware of the security posture of each system. What would support that requirement? |
Establishing baseline reporting |
|
|
deploying a wildcard certificate is one strategy to do what? |
reduce the certificate management burden
|
|
|
Th security admin needs to manage traffic on a layer 3 device to support FTP from a new remote site. What would need to be implemented? |
access control lists |
|
|
Which port is used for SSH by default |
22 |
|
|
A network admin has been tasked with securing the WLAN. Which cryptographic product would be used to provide the MOST secure environment for the WLAN? |
WPA2 CCMP |
|
|
A server with an IP address of 10.10.2.4 has been having intermittent connection issues. The logs show repeated connection attempts from the following IPs: 10.10.3.16, 10.10.3.23, 212.178.24.26, and 217.24.94.83.
These attempts are overloading the server to the point that it cannot respond to traffic. Which attack is occurring? |
DDoS |
|
|
Which cipher would be best used to encrypt streaming video? |
RC4 |
|
|
A user attempting to log on to a workstation for the first time is prompted for the following info before being granted access: username, password, and 4 digit pin that was mailed to him during account registration. This is an example of what? |
single factor authentication |
|
|
After analyzing and correlating activity from multiple sensors, the security admin has determined that a group of very well organized individuals from an enemy country is responsible for various attempts to breach the compay network, through the use of a very sophisticated and targeted attacks. This is an example of____. |
advanced persistent threat |
|
|
true/false: In a client-server architecture, when data integrity is critical to the organization, input validation should be performed on the server side. |
true |
|
|
A merchant acquirer has the need to store credit card numbers in a transitional database in a high performance environment. What best protects the credit card data? |
database field encryption |
|
|
A bank has a fleet of aging payment terminals used by merchants for transactional processing. The terminals currently support single DES but require an upgrade in order to be compliant with security standards. What is likely to be the simplest upgrade to the aging terminals which will improve in-transit protection of the transactional data? |
3DES |
|
|
What is the BEST at blocking and providing security at layer 7 of the OSI model? |
WAF
|
|
|
What is BEST used to capture and alayze network traffic between hosts on the same network segment? |
protocol analyzer |
|
|
After a number of highly publicized and embarrassing customer data leaks as a result os social engineering attacks by the phone, the chief information officer (CIO) has decided the user training will reduce the risk of another data leak. What would be the MOST effective in reducing data leaks in this situation? |
Information Security Awareness |
|
|
What function provides an output which cannot be reversed and converts data into a string of characters? |
hashing |
|
|
What encrypts data a singlel bit at a time? |
stream cipher |
|
|
what is used to verify data integrity? |
SHA |
|
|
by default, TCP port 22 is used by ____. |
SCP, SSH and SFTP |
|
|
Access mechanisms to data on encrypted USB hard drives must be implemented correctly otherwise what may occur? |
the security controls on the USB drive can be bypassed.
|
|
|
Maintenance workers find an active network switch hidden above a dropped ceiling tile in the CEOs office with various connected cables from the office. What type of attack is occuring? |
packet sniffing |
|
|
A security admin is segregating all web facing server traffic from the internal network restricting it to a single interface on a firewall. What BEST describes this new network? |
DMZ |
|
|
What was based on a previous X 500 specification and allows either unencrypted authentication or encrypted authentication through the use of TLS? |
LDAP |
|
|
The quality assurance team is testing a new third party developed application. The quality team does not have any experience with the application. What is the team performing? |
black box testing |
|
|
___ has a storage root key. |
TPM |
|
|
A data center requires that staff be able to ID whether or not items have been removed from the facility. Which controls will allow the organization to provide automated notification of item removal? |
RFID |
|
|
A malicious person gained access to a datacenter by ripping the proximity badge reader off the wall near the datacenter entrance. This caused the electronic locks on the datacenter door to release because the ___. |
system was designed to fail open for life-safety. |
|
|
The concept of rendering data passing between two points over an IP based network impervious to all but the most sophisticated advanced persistent threats is BEST categorized as ___. |
transport encryption |
|
|
On Monday, all company employees report eing unable to connect to the corporate wireless network, which uses 802.1x with PEAP. A technician verifies that no configuration changes were made to the wireless network and its supporting infrastructure, and that there are no outages. What is MOST likely the cause of this? |
The remote authentication dial-in user service server certificate has expired. |
|
|
What would BEST deter an attacker trying to brute force 4 digit PIN numbers to access an account at a bank tell machine? |
account lockout settings |
|
|
In kerberos, the ticketing granting ticket s used for what? |
authentication |
|
|
What network design element allows for many internal devices to share on public IP address? |
PAT |
|
|
What component of an all in one security appliance would MOST likely be configured in order to restrict access to peer to peer file sharing websites? |
URL filter |
|
|
When considering a vendor specific vulnerability in critical industrial control systems, what technique supports availability? |
incorporating diversity into redundant design |
|
|
During the information gatherig stage of a deploying role-based access control model, what information is MOST likely required? |
Matrix of job titles with required access privileges. |
|
|
The CTO has been informed of a potential fraud committed by a database admin performing several other job functions within the company. What is the BEST method to prevent such activities in the future? |
separation of duties |
|
|
Ann would like to forward some personal identifiable information to her HR department by email, but she is worried about the confidentiality of the information. What will accomplish this task securely? |
encryption. |
|
|
A company is trying to limit the risk associated with the use of unapproved USB devices to copy documents. Which would be the BEST technology control to use in this scenario? |
DLP
|
|
|
A company is trying to implement physical deterrent controls to improve the overall security posture of their data center. What would help them BEST meets their goal? |
Hardware locks
|
|
|
A company's employees were victims of a spear phishing campaign impersonating the CEO. The company would nwow like to implement a solution the overall security posture by assuring their that email originated from the CEO. Which of the following controls could they implement to BEST meet this goal?D |
Digital signatures |
|
|
A security technician is attempting to improve the overall security posture of an internal mail server. Which of the following actions would BEST accomplish this goal? |
Disabling unnecessary services |
|
|
A bank has recently deployed mobile tablets to all loan officers for use at customer sites. Which would BEST prevent the discolsure of customer data in the event that a tablet is lost or stolen? |
Remote wiping |
|
|
Which of the following is the primary security concern when deploying a mobile device on a network? |
Data security |
|
|
Which of the following technical controls is BEST used to define which applications a user can install and run on a company issued mobile device? |
Whitelisting |
|
|
After a company has standardized to a single operating system, not all servers are immune to a well-known OS vulnerability. Which solution would mitigate this issue? |
Patch management system |
|
|
A security administrator discovers an image file that has several plain text documents hidden in the file. Which of the following security goals is met by comouflaging data inside of other files? |
confidentiality |
|
|
A company determines a need for additional protection from rogue devices plugging into physical ports around the building. What provides the highest degree of protection from unauthorized wired network access? |
802.1x |
|
|
A company is preparing to decomission an offline, non-networked root certificate server. Before sending the server's drives to be destroyed by a contrated company, the Chief Security Officer wants to be certain that the data will not be accessed. If implimented, what would best reassure the CSO? |
Full disk encryption and disk wiping prcedures |
|
|
During the analysis of a PCAP file, a security noticed several communications with a remoter server on port 53. What protocol type is observed in this traffic? |
DNS |
|
|
A compromised workstation utilized in a DDoS attack has been created. However, the system administrator stated that the system as left unattended for several hours before the image was created. In the event of a court case, what is likely to be an issue with this incident? |
chain of custody |
|
|
During which phase of the incident response process should a security administrator define and the implement general defense general defence against malware? |
preparation |
|
|
Due to hardware limitation, a technician must impelment a wirelss encryption algorithm that used the RC4 protocol. Whcih wireless encryption solution should the technician implement to ensure the strongest level of security? |
WPA-TKIP |
|
|
Joe, a user wants to send an encrypted email to Ann. Which of the following will Ann need to use to verofy that the email came from Joe and decrypt it? |
Anns private key and Joes public key. |
|
|
A technician wants to implement a udual factor authentication system that will enable the organization to authorize access to sensitive systems on a need to know basis. What should be implemented during the authorization stage? |
Biometrics |
|
|
A security researcher wants to reverse engineer an executable file to determine if it is malicious. The file was found on an underused server and appears to contain a zero-day exploit. What can the researcher do to determine in the file is malicious in nature? |
OS baseline comparison |
|
|
A recnet spike in virus detections has been attributed to end-users visiting www.company.com . The business has an established relationship with an organization using the URL of www.company.com but not with the site that hhas been causing the infections. What would BEST describe this type of attack? |
Typo squatting |
|
|
A company has proprietary mission critical devices connected to their network which are configured remotely by both employees and approved customers. The administrator wants to monitor device security without changing their baseline configuration. Whcih od the following should be implemented to secure the devices without risking availability? |
IDS |
|
|
An administrator has a network subnet dedicated to a group of users. Due to concerns regarding data and network secuirty. the administrator desires to proviede network access for this group only. Which of the following would BEST address this desire? |
Configure the switch to allow only traffic from computers based upon their physical address. |
|
|
A security concern regarding users bringing personally-owned devices that they connect to the corporate network? |
Lack of controls in place to ensure that the devices have the latest system patches and signature files. |
|
|
Due to issues with building keys being duplicated and distributed, a security administrator wishes to change to a different security control regarding a restricted area, The goal is to provide access based upon facial recognition. What will address this requirement? |
Place a guard at the entrance to approve access. |
|
|
A security administrator has concerns regarding employees saving data on company provided mobile devices. What would BEST address the administrators concerns? |
Configure the devices so that removable media use is disabled. |
|
|
Identifying residual risk is MOST important to which of the following concepts? |
Risk acceptance |
|
|
The information security technician wants to ensure security controls are depliyed and functioning as intended to be able to maintain an appropriate security posture. What security technique is MOST appropriate to do this? |
continuous security monitoring |
|
|
A small company can only afford to buy an all-in-one wireless router/switch. The company has 3 wireless BYOD users and 2 web servers without wireless access. Which of the following should the company configure to protect the servers from the user devices? |
Create a server VLAN, and create an ACL to access the server |
|
|
Users an authenticate to a company's web applications using their credentials from a popular social media site. Which of the following poses the greatest risk with this integration? |
Password breaches to the social media site affect the company application as well |
|
|
A security team has established a security awareness program. Which of the following would best prove the success of the program? |
metrics
|
|
|
A company needs to receive data that contains personally identifiable information. The company requires both the transmission and data at rest to be encrypted. Which of the following achieves this goal? |
SSH, and PGP/GPG |
|
|
An organization does not have adequate resources to administer its large infrastructure. A security administrator wishes to combine the security controls of some of the network devices in the organization. Which of the following methods would BEST accomplish this goal? |
Unified threat management |
|
|
Which of the following would allow the organization to divide a class C IP address range into several ranges? |
Subnetting |
|
|
The security administrator is currently unaware of an incident that occurred a week ago. Which of the following will ensure the administrator is notified in a timely manner in the future? |
routine auditing |
|
|
An access point has been configures for AES encryption but a client is unable to connect to it. Which of the following should be configures on the client to fix this issue? |
CCMP
|
|
|
The system administrator is tasked with changing the admin password across all 2000 computers in the organization. Which of the following should the system administrator implement to accomplish this task? |
A group policy |
|
|
A network administrator wants to block both DNS requests and zone transfers coming from outside IP addresses. The company uses a firewall which implements an implicit allow and is currently configures with the following ACL applied to its external interface: PERMIT TCP ANY ANY 80 PERMIT TCP ANY ANY 443 Which of the following rules would accomplish this task? |
Change the firewall default settings so that is implements an implicit deny and add the following ACL at the bottom of the current ACL: DENY IP ANY ANY 53 |
|
|
Which of the following attacks would cause all mobile devices to lose their association with corporate access points while the attack is underway? |
Wireless jamming
|
|
|
An administrator wants to ensure that the reclaimed space of a hard drive has been sanitized while the computer is in use. Which can be implemented? |
Cluster tip wiping |
|
|
A company is looking to improve their security posture by addressing risks uncovered by a recent penetration test. Which of the following risks is MOST likely to affect the business on a day-to-day basis? |
Lack of anitvirus software |
|
|
Ann, an employee, is cleaning out her desk and disposes of paperwork containing confidential risk of loss from which of the following attacks? |
dumpster diving |
|
|
A recently installed application update caused a vital application to crash during the middle of the workday. The application remained down until a previous version could be reinstalled on the server, and this resulted in a significant loss of data and revenue. Which of the following could best prevent this issue from occurring again? |
application patch management |
|
|
A security admin wished to increase the security of the wireless network. Which of the following BEST addresses this concern? |
Change the encryption from TKIP based to CCMP based
|
|
|
The system admin has deployed updated security controls for the network to limit risk of attack. The security manager is concerned that controls continue to function as intended to maintain appropriate security posture. Which of the collowing risk mitigation strategies is MOST important to the security manager? |
Routine audits |
|
|
A company is about to release a very large patch to its customers. An administrator is required to test patch installations several times prior to distributing them to customer PCs. Which of the follwing should the admin use to test the patching process quickly and often? |
Create a virtualized sandbox and utilize snapshots |
|
|
An auditing team has found that passwords do not meet best business practices. Which of the following will MOST increase the security of the Passwords? (select two) |
Password Complexity, Password length |
|
|
A vulnerability scan is reporting that patches are missing on a server. After a review, it is determined tat the application requiring the patch does not exist on the operating system. Which of the following describes this cause? |
false positive |
|
|
Company A submitted a bid on a contract to do work for Company B via email. Company B was insistent that the bid did not come from Company A. Which of the following would have assured tat the bid submitted by Company A? |
Digital Signatures |
|
|
Ann, a sales manager, successfully connected her company-issued smartphone to the wireless network in her office without supplying a username/password combination. Upon disconnecting from the wireless network, she attempted to connect her personal tablet computer to the same network and could not connect. Which of the following is MOST likely the reason? |
The company wireless is using a MAC filter
|
|
|
A network technician of on the phone with the system administration team, Power to the server room was lost and servers need to be restarted. The DNS services must be the first to be restarted. Several machines are powered off. Assuming each server only provides one service, which of the following should be powered on FIRST to established DNS services? |
bind server
|
|
|
Which of the following is a hardware based encryption device? EFS/Truecrypt/TPM/SLE |
TPM |
|
|
Certificates are used for: (select two) client authentication/WEP encryption/Access control lists/Code signing/Password hashing |
Client authentication/Code signing |
|
|
a security admin wants to check user password complexity. Which of the following is the BEST tool to use?
Password history/password logging/password cracker/password hashing
|
password cracker |
|
|
Which of the following can be used by a security administrator to successfully recover a user's forgotten password on the password protected file? |
cognitive password/password sniffing/brute force/social engineering |
|
|
Which of the following application security testing techniques is implemented when an automates system generates random input data?
fuzzing/XSRF/hardening/Input validation |
fuzzing |
|
|
Which of the following devices would most likely have a DMZ interface?
Firewall/Switch/load balancer/proxy |
Firewall
|
|
|
Employee badges are encoded with a private encrytpion key and specific personal information/ The encoding is then used to provide access to the netwrok. Which of the following describes this access control type?
Smartcard/token/discretionary access control/mandatory access control |
smartcard |
|
|
Which of the following MUST be updated immediately when an employee is terminate to prevent unauthorized access?
registration/CA/CRL/Recovery agent |
CRL |
|
|
A security administrator needs to determine which system a particular user is trying to login to at various times of the day. Which of the following log types would the administrator check?
firewall/application/IDS/security |
security |
|
|
Drag and drop the correct protocol to its default:
FTP/Telnet/SMTP/SNMP/SCP/TFTP
161/22/21/69/25/23 |
FTP=21 TELNET=23 SMTP=25 SNMP=161 SCP=22 TFTP=69 |
|
|
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them:
RAM.CPU cache/swap/hard drive |
CPU cache/RAM/swap/Hard drive |
|
|
For each of the given items, select the appropriate authentication category from the dropdown choices.
retina scan/smart card/hardware token/password/PIN number/Firngerprint scan |
Retina scan=all given authentication categories smart card=something you have hardware token=something you are password=something you know pin number=something you know fingerprint scan=all given authentication categories |
|
|
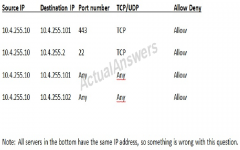
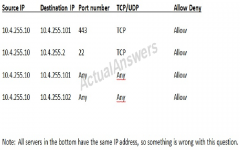
Select the appropriate attack from each drop down list to label the corresponding illustrated attack: 1. attacker gains conf. company info 2. attacker posts links to fake AV software 3. attacker collecting credit card details 4. attacker mass-emails 5. attacker redirects name resolution
|
1. spear pushing 2. hoax 3. vishing 4. phishing 5. pharming |
|
|
For each given item, select the apprompriate authentication category from the drop down choices:
Fingerprint scan/hardware token/smartcard/password/PIN number/retina scan |
fingerprint scan=biometric autherntication Hardware token=one time password smart card=multi-factor password=PAP authentication PIN number=PAP authentication Retina scan=biometric authentication |
|
|
A security admin wants to implement strong security on the company smart phones and terminal servers located in the data center. Drag and drop the applicable controls to each type. (controls can be used multiple times)
scerren locks/strong password/device encyption/remote wipe/GPS tracking/pop up blocker/ cable locks/antivirus/host based firewall/proximity reader/sniffer/mantor ap |
smart phone: scerren locks/srtong password/device encryption/remote wipe/gps tracking/pop-up blocker
data center terminal server: cable locks /antivirus/host based firewall/sniffer/mantor app |
|
|
determine the types of attacks below by selecting an option from the dropdown list:
1. email sent to multiple users to a link 2. phone calls made to CEO of organization 3. Phone call made to individual stating there was an IT issue 4. social media site and instant message pops up 5. a friend/collegue asks you questions of a personal nature |
1. phishing 2. whaling 3. vishing 4. spim 5. social engineering
|
|
|
drag the items on the left to show the different types of security for the shown devices. Not all fields need to be filled. Not all items need to be used.
mobile device security/server in data center security
|
mobile device security=GPS tracking/remote wipe/device encryption/strong passwords
server in data center security=FM-200/biometrics/proximity badges/mantrap
|
|
|
|
|
|
Which of the follwoing would be used when a higher level of security is desired for encryption storage?
tactas+/L2TP/LDAP/TPM |
TPM |
|
|
In regards to secure coding practices, why is input validation important?
it mitigates buffer overflow attacks it makes the code more readable it provides an application config baseline it meet gray box testing standards |
it mitigates buffer overflow attacks
|
|
|
All of the following are valid cryptographic hash functions EXCEPT
RIPEMD/RC4/SHA-512/MD4
|
RC4 |
|
|
Which of the following devices is BEST suited for servers that need to store private keys?
Hardware security module hardened network firewall solid state disk drive hardened host firewall |
hardware security module |
|
|
Which of the following is the BEST approach to perform risk mitigation of user access control rights? conduct surveys and rank the results Implement periodic vunerability scanning disable user accounts |
perform routine user permission reviews |
|
|
A network stream nees to be encrypted. Sara, the network admin has selected a cipher which will encrypt 8 bits at a time before sending the data across the network. Which of the following has sara selected?
block cihper/stream cipher/CRC/hashing algorithm |
block cipher |
|
|
Pete, the sysad is reviewing his disaster recovery plans. He wishes to limit the downtime in the event of a disaster, but does not have the budget approval to implement or maintain an offsite location. Which of the following is his BEST option?
use hardware/move the servers/retain data/move the data back-ups... |
Use hardware already at an offsite location and configure it to be quickly utilized |
|
|
Pete, the system admin has blocked users from accessing social media web sites. In addition to protection company information from being accidentally leaked, which additional security benefit does this provide?
no competition.../protection against malware introduced by banner ads/increased number.../elimination... |
protection against malware introduced by banner ads |
|
|
Which of the following can be implemented with multiple bit strength? AES/DES/SHA-1/MD5/MD4 |
AES |
|
|
Pete, the security engineer would like to prevent wireless attacks on his network. Pete has implemented a security control to limit the connecting MAC addresses to a single port. Which of the following wireless attacks would this address? interference/man in the middle/ARP/Rogue access point |
rogue access point |
|
|
Pete's corporation has outsourced help desk services to a large provider. Management has published a procedure that requires all users, when receiving support, to call a special number. Users then need to enter the code provided to help them by the help desk tech prior to allowing the technician to work on their PC. Which of the following does this procedure prevent?
Collucion/impersontation/pharming/transitive access
|
impersonation |
|
|
The infosec team does a presentation on social media and advises the participants not to provide too much personal information on social media websites. This advice would BEST protect people from which of the following?
rainbow table attacks/brute force attacks/birthday attacks/cognitive passwords attacks |
cognitive passwords attacks |
|
|
Pete, a developer writes an application. Jane, the security analyst knows some things about the overall application but does not have all the details. Jane needs to review the software before it is released to production. Which of the following reviews should Jane conduct? Gray box testing/black box testing/business impact analysis/white box testing |
gray box testing |
|
|
Which of the following is the LEAST volatile when performing incident response procedures? Registers/RAID cache/RAM/Hard drive |
hard drive |
|
|
Sara, an application developer, implemented error and exception handling alongside input validation. Which of the following does this help prevent?
buffer overflow/pop up blockers/cross site scripting/fuzzing |
buffer overflow |
|
|
Which of the following encompasses application patch management?
configuration management/policy management/crosssite management/fuzzing |
configuration management |
|
|
Which of the following presents the STRONGEST access control?
MAC/TACTACS/DAC/RBAC |
MAC |
|
|
Configuring the mode, encryption methods, and security associations are part of which of the following?
IPSec/full disk encryption/802.1x/PKI |
IPSec |
|
|
Which of the following assessments would Pete, the security administrator, use to actively test that an application's security controls are in place?
code review/penetration test/protocol analyzer/vunerability scan |
penetration test |
|
|
A security admin has just finished creating a hot site for the company. This implementation relates to which of the following?
confidentiality/availability/succession planning/integrity |
availability |
|
|
In the initial stages of an incident response, Matt, the security admin, was provided he hard drives in QUESTION NO: from the incident manager. Which of the following incident response procedures would he need to perform in order to begin analysis?
take hashes/begin chain of custody paperwork/take screen shots/capture the system image/decompile suspicious files |
take hashes/capture the system image |
|
|
Which of the following is used to certify intermediate authorities in a large PKI deployment?
Root CA/Recovery agent/root user/key escrow |
Root CA |
|
|
Which of the following components MUST be trusted by all parties in PKI?
Key escrow/CA/Private key/recovery key |
CA |
|
|
Which of the following should Matt, a security admin, include when encrypting smartphones?
steganography images/internal memory/master boot records/removable memory cards, public keys |
internal memory, removable memory cards |
|
|
Which of the following is the below psuedo-code an ecample of? IF VARIABLE |(CONTAINS NUMBERS = TRUE) THEN EXIT
buffer overflow prevention/input validation/CSRF prevention/cross-site scripting prevention |
input validation |
|
|
A system admin is using a packet sniffer to troubleshoot remote authentication. The administrator detects a device trying to communicate to TCP port 49. Which of the following authentication methods is most likely being attempted?
RADIUS/TACACS+/Kerberos/LDAP |
TACACS+ |
|
|
Which of the following can ise RC4 for encryption?
CHAP/SSL/WEP/AES/3DES |
SSL/WEP |
|
|
Which of the following defines a business goal for system restoration and acceptable data loss?
MTTR/MTBF/RPO/Warm site |
RPO |
|
|
Which of the following allows a company to maintain access to encrypted resources when employee turnover is high?
Recovery agent/Certificate authority/trust model/key escrow |
recovery agent |
|
|
Which of the following devices will help prevent a laptop from being removed from a certain location?
|
cable locks |
|
|
Which of the following is the most secure protocol to transfer files?
FTP/SFTP/SSH/TELNET |
SFTP (FTPS) |
|
|
Which of the following protocols is used to authenticate the client and server's digital certificate?
PEAP/DNS/TLS/ICMP |
TLS |
|
|
Which of the following can be used to mitigate risk is a mobile device is lost?
Cable lock/transport encryption/voice encryption/strong passwords |
strong passwords |
|
|
Which of the following security concepts would sara, the security admin, use to mitigate the risk of data loss?
Record time offset/clean desk policy/cloud computing/routine log review |
clean desk policy |
|
|
Mike, a security professional, is tasked with actively verifying the strength of the security controls on a company's live modem pool. Which of the following activities is MOST appropriate?
War dialing/War chalking/war driving/bluesnarfing |
war dialing |
|
|
Users at a company report that a popular news website keeps taking them to a web page with derogatory content. This is an example of which of the following?
Evil twin/DNS poisoning/Vishing/Session hijacking |
DNS poisoning |
|
|
An encrypted message is sent using PKI from Sara, a client, to a customer. Sara claims she never sent the message. Which of the following aspects of PKI BEST ensures the Identity of the sender?
CRL/non-repudiation/trust models/recovery agents |
non-repudiation |
|
|
Jane, a security admin has observed repeated attempts to break into a server. Which of the following is designed to stop an intrusion on a specific server?
HIPS/NIDS/HIDS/NIPS |
HIPS |
|
|
Matt, the IT manager wants to create a new network available to virtual servers on the same hypervisor, and does not want this network to be routable to the firewall. How could this best be accomplished?
Create a VLAN/remove the network from the routing table/create a virtual switch/commission a stand-alone switch
|
create a virtual switch |
|
|
A security admin implements access controls base on the security classification of the data and need-to-know info. Which of the following BEST describes this level of access control?
Implicit deny/role-base access control/mandatory access controls/least privilege |
mandatory access controls |
|
|
A company that purchased an HVAC system for the datacenter is MOST concerned with which of the following?
availability/integrity/confidentiality/fire suppression |
availability |
|
|
Which of the following pseudocodes can be used to handle program exceptions?
If a program detects another instance of itself, then kill program instance if user enters invalid input, then restart program if program module crashes, then restart program module if user's input exeeds buffer length, then truncate the input |
if program module crashes, the restart program module |
|
|
Which of the following technologies uses multiple devices to share work?
switching/load balancing/RAID/VPN concentrator |
Load Balancing |
|
|
Which od the following protocols uses an asymmetric key to open a session then establishes a symmetric key for the remainder of the sessions?
SFTP/HTTPS/TFTP/TLS |
HTTPS |
|
|
Which of the following describes how sara, an attacker, can send unwanted advertisements to a mobile device?
man in the middle bluejacking bluesnarfing packet sniffing |
bluejacking |
|
|
Pete, an employee, is terminated from the company and the legal dept needs documents from his encrypted HDD. Which of the following should be used to accomplish this task?
Private hash/recovery agent/public key/key escrow/CRL |
recovery agent, key escrow |
|
|
Which of the following mitigation strategies is established to reduce risk when performing updates to business critical systems?
incident management/server clustering/change management/forensic analysis |
change management |
|
|
which of the following can pete, a security admin, use to distribute the processing effort when generating hashes for a password cracking program?
RAID/clustering/redundancy/virtualization |
clustering |
|
|
Which of the following should Jane, a security admin perform before a HDD is analyzed with forensics tools?
Identify user habits/disconnect system from network/capture system image/interview witnesses |
capture systems image |
|
|
Jane, an admin needs to make sure the wireless network is not accessible from the parking area of their office. Which of the following would BEST help Jane when deploying a new access point?
Placement of antenna/disabling the SSID/implementing WPA2/Enableing the MAC filtering |
Placement of the antenna |
|
|
Which of the following allows Pete, a security technicain to provide the MOST secure wireless implementation?
Implement WPA/disable SSID/adjust antenna placement/implement WEP |
Implement WPA |
|
|
Which of the following is a management control?
logon banners/written security policy/SYN attack prevention/access controls list (ACL) |
written security policy |
|
|
Which of the following security strategies allows a company to limit damage to internal systems and provide loss control?
Restoration and recovery strategies/ deterrent strategies/containment strategies/detection strategies |
containment strategies |
|
|
In order for sata, a client, to logon to her desktop computer, she must provide her username, password, and a four digit PIN. Which of the the following authentication methods is sara using?
three factor/single factor/two factor/four factor |
single factor |
|
|
Using proximity card readers instead of the traditional key punch doors would help to mitigate
impersonation/tailgaitng/dumpster diving/shoulder surfing |
shoulder surfing |
|
|
Which of the following application attacks is used gain access to SEH?
Cookie stealing/buffer overflow/directory traversal/XML injection |
Buffer overflow |
|
|
Which of the following is an authentication service that uses UDP as a transport medium?
TACACS+/LDAP/Kerberos/RADIUS |
RADIUS |
|
|
Which of the following can be used on a smartphone to BEST protect against sensitive data loss if the device is stolen?
Tethering/screen lock/remote wipe/email password/GPS tracking/device encryption |
Remote wipe/device encryption |
|
|
Which odf the following should Pete, a security manager, implement to reduce the risk of employees working in collusion to embezzle funds from their company?
Privacy policy/least privilege/acceptable use/mandatory vacations |
mandatory vacations |
|
|
which of the following will allow pete, a security analyst to trigger a security alert because of a tracking cookie?
network based firewall/anti spam software/host based firewall/anti spyware software |
anti spyware software |
|
|
Which f the collowing protocols are used to secure transfer of files?
ICMP/SNMP/SFTP/SCP/TFTP |
SFTP, SCP |

