![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
202 Cards in this Set
- Front
- Back
- 3rd side (hint)
|
What are three fundamental approaches to proof of possession of secret?
|
One-time password, encryption (symmetric secret or public key), or hashing (message authentication code).
|
|
|
|
The hash mechanism that provides integrity.
|
Message Authentication Code (MAC) and Message Integrity Code (MIC)
|
|
|
|
What is the pseudocode for a MAC?
|
Msg, nonce, hash(PW , Msg , nonce)
|
|
|
|
Can you use an encryption function as a hashing function?
|
Yes, but you must throw something away.
|
|
|
|
What is the probability of a hash collision of message M2 with message M1 using an n bit hash?
|
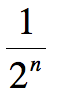
1 / (2^n)
|
|
|
|
How many messages would have to be generated to raise the probability of a hash between any two to ~50%?
|
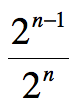
2^(n-1) / 2^n
|
|
|
|
[Cryptool] Look at the “grids” representing a plaintext block and the cipher key. How many bits comprise an AES block?
|
16 blocks * 2 hex chars * 4 bits per hex char = 128
|
|
|
|
[Cryptool] How many total AES rounds are there per plaintext block?
|
10
|
(Note: In class lecture I refer to this concept more generally as iterations. This may be a bit confusing as the presentation confuses the issue a bit. Specifically, do we count the initial round or not? The answer is no, they don’t count the initial round in the total number of rounds.)
|
|
|
[Cryptool] What does the ‘S’ in “S-Box” stand for?
|
Substitution
|
(Note: you find the same kind of thing in the DES algorithm, and others)
|
|
|
[Cryptool] What is the primary source of obscuring the relationship between columns and rows in Rijndael?
|
diffusion
|
|
|
![[Cryptool] Can you discern what operation is represented by the circle-enclosed plus sign?](https://images.cram.com/images/upload-flashcards/38/27/27/5382727_m.png)
[Cryptool] Can you discern what operation is represented by the circle-enclosed plus sign?
|
XOR
|
If you don’t know this from memory (computer arch. or discrete math class), see if you can reverse-engineer its meaning by analyzing the math shown. E.g., 66 operated on by fa yields 9c.
|
|
|
[Cryptool] While observing the Key Schedule process, you see that the 10 round keys (partial keys) are generated by using what technique(s) against the main AES key?
|
both substitution and transposition
|
|
|
|
[Cryptool] What are the S-Boxes used on?
|
plaintext blocks and derived round keys
|
|
|
|
[Cryptool] AES encrypts a block of plaintext using?
|
10 different keys, one per round, but each derived from a single 128-bit key
|
|
|
|
[Cryptool] Who is the CA (Certification Authority) for this certificate?
|
CrypTool
|
|
|
|
[Cryptool] What is the validity period (duration not end date) for the cryptool lab certificate?
|
1 year
|
|
|
|
[Cryptool] What algorithm do you think was used to create the “Public Key Fingerprint” in this certificate?
|
MD5
|
|
|
|
[Cryptool] How large (number of bits) is your public key?
|
1024
|
|
|
|
[Cryptool] Where in the certificate is your corresponding private key?
|
It only holds public keys in the certificate
|
|
|
|
[Cryptool] What is the bit length of this signature?
|
2048
|
|
|
![[Cryptool] What does the warning above apply to?](https://images.cram.com/images/upload-flashcards/38/27/39/5382739_m.png)
[Cryptool] What does the warning above apply to?
|
The fact that you’re about to import a CA certificate.
|
|
|
|
[Cryptool] Alice’s shared key was generated according to A = g^a mod p. Which component(s) on the right side of this equation is/are the private part(s)?
|
a
|
|
|
|
[Cryptool] To see signs of the “Strict Avalanche Criterion”, what would you expect the percentage difference to be?
|
Close to 50%
|
|
|
|
[Cryptool] By what factor do you figure base-64 “compacts” binary?
|
3 bytes of binary to 4 bytes of characters (the resulting file is 33% larger)
|
|
|
|
[Cryptool] What character set does base-64 use?
|
A-Z, a-z, 0-9, /, and +
|
Look at the base-64 encoding of SampleFile.txt and see if you can glean what the character set is that base-64 utilizes. That is, for hexadecimal we know we use the character set (0-9,A-F).
|
|
|
[SP800-32 PKI] What are the two example pieces of U.S. legislation (many other countries have similar laws and regulations) whose implementation requirements influenced the need for PKI?
|
Government Paperwork Elimination Act and Health Insurance Portability and Accountability Act
|
|
|
|
[SP800-32 PKI] PINs and passwords can be used to provide non-repudiation.
|
False
|
|
|
|
[SP800-32 PKI] What are the three commonly used classes of cryptographic mechanisms?
|
Symmetric algorithms, secure hash algorithms, and asymmetric algorithms
|
|
|
|
[SP800-32 PKI] What is the general method used to deal with the secret key distribution problem, when PKI (asym crypto) is not available?
|
Out-of-band mechanisms
|
Hint: OOB delivery
|
|
|
[SP800-32 PKI] What is the general solution to scale OOB key management for large groups?
|
Trusted third party
|
Hint: TTP
|
|
|
[SP800-32 PKI] What does HMAC stand for?
|
Hash-based message authentication code
|
|
|
|
[SP800-32 PKI] What was not mentioned as one of the three operations performed by asymmetric algorithms?
|
message encryption
|
|
|
|
[SP800-32 PKI] What is referred to as the “Achilles heel” for symmetric algorithms?
|
Key distribution
|
|
|
|
[SP800-32 PKI] What best summarizes the role of an RA in PKI?
|
Verifies identities of entities requesting certificates
|
|
|
|
[SP800-32 PKI] What does CRL stand for?
|
Certificate revocation lists
|
|
|
|
[SP800-32 PKI] Federal government CAs should always use cryptographic modules that have been validated against what document?
|
FIPS-140
|
|
|
|
[SP800-32 PKI] What are the three architectures to dealing with this certificate authorities?
|
Hierarchical architecture, mesh architecture, and bridge CA architecture
|
|
|
|
[SP800-32 PKI] If Alice digitally signed an email to Carol, upon what cryptographic trust basis would Carol “accept” this signature?
|
Because both Carol’s and Alice’s trusted CA signed the Bridge CA certificate
|
|
|
|
[SP800-32 PKI] Describe a Mesh architecture.
|
Anyone may stand up his/her/their own CA. Any CA wanting its users to be interoperable (“federate”) with another CA will enter an agreement with that other CA to issue cross-certificates for one another.
|
|
|
|
[SP800-32 PKI] Describe a Hierarchical architecture.
|
The U.N. is established as “super-root” and issues one root certificate to each country, which then issues sub-CA certs to states, organizations, etc., and no other (private of otherwise) CAs are involved.
|
|
|
|
[SP800-32 PKI] What combination uniquely identifies any certificate?
|
Issuer name & serial number
|
|
|
|
[SP800-32 PKI] What does FBCA stand for?
|
Federal Bridge Certificate Authority
|
|
|
|
[SP800-32 PKI] What does CP stand for in the context of PKI?
|
CPS translates CPs into operational procedures on the CA level; the CP sets standards for use (i.e. a CA will provide PKI service)
|
|
|
|
[SP800-32 PKI] What does CPS stand for in the context of PKI?
|
CPS translates CPs into operational procedures on the CA level; CPS is the site implementation of the PKI (i.e. how a group will use PKIs for access to information)
|
|
|
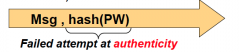
Why is this a failed attempt at authenticity?
|
Regardless if PW is only used once or not, attacker can still modify this message (unless the hash was only known to the sender/receiver)
|
|
|
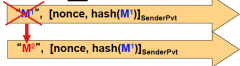
Where attacker has found an M2 such that the digital signatures are the same… because the
nonce is left alone and hash(M1) == hash(M2). Why is this not a birthday attack? |
The attacker would need ONE specific message to find a collision (Pre-Image Attack)
|
|
|
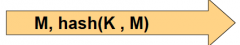
Does this hash provide authenticity?
|
No, if you intercept a message you can add on to the end of the MAC because the message is hashed as a chain
|
|
|
|
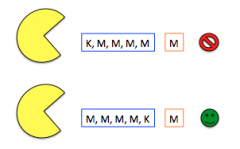
When using a hash how can you fix chaining so that messages end on a 512 bit boundary?
|
Pad to a 512 bit boundary
|
Specifically for MD4, MD5, or SHA-1
|
|
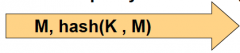
How does an HMAC fix the problem of hashing with the method provided?
|
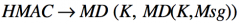
By re-hashing the hash with the same key
|
|
|
|
Why are the two different cases of authentication treated differently?
|
A computer can store a high quality secret and a human typically cannot
|
Human to Computer vs Computer to Computer
|
|
|
When you say "yes" to "remember me on this computer", what have you effectively done?
|
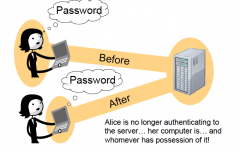
Changed the relationship from authenticating a human to authenticating a machine
|
|
|
|
Even with password-based authentication hashes are still vulnerable to what two things?
|
brute force attack and dictionaries of pre-hashed dictionaries
|
|
|
|
What good does adding a salt to a hash provide?
|
Adding salt prevents the attacker from using a pre-hashed dictionary to do lookups
|
|
|
|
How does space-time relate to computing problems?
|
Small solution space requires a lot of time and a quick solution requires a lot of space
|
|
|
|
In terms of space-time computing problems, what is meant by space?
|
processor size and memory size
|
|
|
|
What do rainbow tables target?
|
The password space in a head - tail fashion in order to easily reproduce salts or dictionary passwords when needed
|
|
|
|
What is the "secret sauce" in a rainbow table?
|
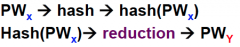
It employs a reduction function that does the opposite of a hash function
|
|
|
|
How does a reduction function differ from a hash?
|
IT DOES NOT UN-HASH, it does not matter what password comes out of the reduction function just only that the password will result in the correct hash
|
|
|
|
What are the two types of authentication?
|
Symmetric (KDC) and Asymmetric (PKI)
|
|
|
|
What is the effect of using a Key Distribution Center (KDC) for symmetric authentication?
|
It changes the key size distribution problem from a n(n-1)/2 key problem to an n problem
|
|
|
|
What is the effect of using a Key Distribution Center (KDC) for asymmetric authentication?
|
It changes the key size distribution problem from a n(n-1) key problem to an n problem
|
|
|
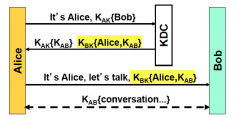
What are the highlighted items referred to as?
|
tickets
|
|
|
|
How can you recognize a ticket?
|
you can recognize it because somebody will get something they cannot decrypt
|
|
|
|
What is transitive trust?
|
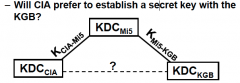
An implicit relationship established between two parties of a common KDC (or group of KDCs)
|
|
|
|
What is the effect of using a Key Distribution Center (KDC) for asymmetric authentication?
|
Changes key management problem from n(n-1) problem to an n problem
|
|
|
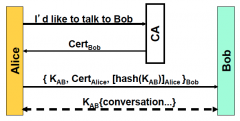
Why isn't Cert(alice) protected with a hash?
|
So that Bob can decrypt the hash of K(ab)
|
|
|
|
What is an indication of a root certificate?
|
It's self signed
|
|
|
|
[SP800-77 IPSec] What does FISMA stand for?
|
Federal Information Security Management Act
|
|
|
|
[SP800-77 IPSec] Just to set the appropriate expectations, this document…
|
presents information that is independent of any particular platform, OS, or application
|
|
|
|
[SP800-77 IPSec] Only one example of an application-layer security control was provided. What was it?
|
Pretty Good Privacy (PGP)
|
|
|
|
[SP800-77 IPSec] What does TLS stand for, and what other (named) security protocol is it a replacement for?
|
Transport Layer Security (Secure Sockets Layer)
|
|
|
|
[SP800-77 IPSec] What “one drawback” of TLS was mentioned?
|
Only capable of supporting TCP-based communications
|
|
|
|
[SP800-77 IPSec] Which of these correctly indicates which layer(s) a data link layer security control protects?
|
It would provide confidentiality for all layers above layer 2 (TCP/IP layers 3-5)
|
|
|
|
[SP800-77 IPSec] For review purposes; notice the mention of MAC. Which of these represents a MAC?
|
hash(SymSecret, data-to-be-protected)
|
|
|
|
[SP800-77 IPSec] Notice the mention of “out-of-band” with respect to dealing with the problem of exchanging what kind of keys?
|
Symmetric
|
|
|
|
[SP800-77 IPSec] What does DES stand for?
|
Digital Encryption Standard
|
|
|
|
[SP800-77 IPSec] What does 3DES stand for?
|
Triple DES
|
|
|
|
[SP800-77 IPSec] What does AES stand for?
|
Advanced Encryption Standard
|
|
|
|
[SP800-77 IPSec] What does RC4 stand for?
|
Rivest Cipher 4
|
|
|
|
[SP800-77 IPSec] What does IDEA stand for?
|
International Data Encryption Algorithm
|
|
|
|
[SP800-77 IPSec] What does HMAC stand for?
|
Hash Message Authentication Code
|
|
|
|
[SP800-77 IPSec] What does MD5 stand for?
|
Message Digest 5
|
|
|
|
[SP800-77 IPSec] What does SHA stand for?
|
Secure Hash Algorithm
|
|
|
|
[SP800-77 IPSec] What does RSA stand for?
|
Rivest Shamir Adleman
|
|
|
|
[SP800-77 IPSec] What does DSA stand for?
|
Digital Signature Algorithm
|
|
|
|
[SP800-77 IPSec] What does ECDSA stand for?
|
Elliptic Curve DSA
|
|
|
|
[SP800-77 IPSec] What is the least commonly used VPN architecture?
|
Host-to-Host
|
|
|
|
[SP800-77 IPSec] Which statement is true? (only one)
a. AH cannot provide any confidentiality service. b. ESP provides confidentiality, but cannot provide any integrity protection. c. Some IPSec software no longer supports ESP because AH can do it all. d. AH and ESP authentication capabilities are identical. |
AH cannot provide any confidentiality service
|
|
|
|
[SP800-77 IPSec] Which is true? (only one)
a. Both ESP and AH can be operated in both tunnel or transport mode. b. ESP works solely in tunnel mode, AH works solely in transport mode. c. ESP can run in either tunnel or transport mode, but AH only works in tunnel mode. d. ESP can only run in tunnel mode, but AH can be operated in either mode. |
Both ESP and AH can be operated in both tunnel or transport mode
|
|
|
|
[SP800-77 IPSec] In AH mode, what—if anything—in an IP datagram is excluded from integrity protection?
|
any IP header fields that might change enroute
|
any IP header fields that might ________ enroute; e.g., TTL, MF flag, etc
|
|
|
[SP800-77 IPSec] Which is true?
a. If you only need confidentiality, you could use AH mode. b. If you only need integrity, you must use AH mode. c. If you want both confidentiality and integrity, both AH & ESP modes must be used together. d. If you want both confidentiality and integrity, you could use just ESP mode. |
If you want both confidentiality and integrity, you could use just ESP mode
|
|
|
|
[SP800-77 IPSec] Why is it that IPSec and NAT often do not “play well” together?
|
When NAT alters the IP source and destination addresses to map a private IP address to a public one, the receiving end calculation of the AH protection scheme will not match.
|
|
|
|
[SP800-77 IPSec] This section indicates that the AH header Payload Length field indicates the length of the payload in 4-byte increments, minus 2. Can you figure out what the “minus 2” accounts for?
|
Minus 2, would be minus 8 byes (since the counter counts 4-byte words). So… the developers of this protocol opted to not bother counting the first two rows of the AH header as the four items found there should always be present (Next Header, Payload Length, Reserved, and SPI).
|
|
|
|
[SP800-77 IPSec] What best expresses the role of the SPI?
|
Used by each side in order to know which SA to use for traffic to the other side
|
Replay protection via nonces has been addressed in class lecture. A typical question arises along the lines of “for how long should a recipient remember nonces received from a given sender?”
|
|
|
[SP800-77 IPSec] What does IPSec (AH or ESP mode) employ for replay protection?
|
Sequence Numbers
|
|
|
|
[SP800-77 IPSec] How does IPSec employ sequence numbers for replay protection?
|
Numbers are assigned by sender, recipient ensures all received numbers fall within the range of a sliding window.
|
|
|
|
[SP800-77 IPSec] What—exactly—is the MAC for the AH transport mode example of Figure 3-4?
|
61 a6 6b fb ae 89 23 1b e4 52 42 ff
|
|
|
|
[SP800-77 IPSec] “AH still provides one benefit that ESP does not: _______________ protection for the ____________________ IP header.”
|
Integrity / outermost
|
|
|
|
[SP800-77 IPSec] Looking at Figure 3-7, you can see that ESP in Transport mode does not include the IP header in what it provides integrity protection for; as does AH (see Figs 3-1 and 3-2). Why then is ESP in Transport mode still incompatible with NAT?
|
. In each TCP packet, the TCP checksum is calculated on both TCP and IP fields, including the source and destination addresses in the IP header. If NAT is being used, one or both of the IP addresses are altered, so NAT needs to recalculate the TCP checksum. If ESP is encrypting packets, the TCP header is encrypted; NAT cannot recalculate the checksum, so NAT fails.
|
Google “TCP Pseudo Header”
|
|
|
[SP800-77 IPSec] An Initialization Vector (IV) is included in the ESP payload. In short, what is the usage of this item?
|
The IV is used during encryption with a different value for each packet so that if two packets have the same content, the IV will cause the encryption of the two packets to have different results
|
|
|
|
[SP800-77 IPSec] Which is true regarding ESP’s use of padding?
a. It is always used. b. It is only used if it is desired to obscure the true amount of data contained in each packet. c. It is only used to ensure the data length matches a multiple of the underlying encryption cipher’s block size, or to ensure the overall ESP PDU falls on a 4-byte boundary. d. Both b and c. |
Both b and c
|
|
|
|
[SP800-77 IPSec] Which of these is true?
a. AH Transport mode is the most compatible with NAT operation. b. AH Tunnel mode is the most compatible with NAT operation. c. ESP Transport mode is the most compatible with NAT operation. d. ESP Tunnel mode is the most compatible with NAT operation. |
ESP Tunnel mode is the most compatible with NAT operation
|
|
|
|
[SP800-77 IPSec] You see reference to “-SHA1-96” here, yet you may recall that SHA1 has a 160-bit hash output. What do you think is going on?
|
They simply truncate the 160-bit SHA-1 result to 96 bits
|
|
|
|
[SP800-77 IPSec] _______________ is the most commonly used IPSec mode.
|
ESP Tunnel mode
|
|
|
|
[SP800-77 IPSec] What does IKE do first?
|
Negotiate the protection suite that will be used to protect subsequent IKE traffic
|
|
|
|
[SP800-77 IPSec] What all is (or can be) negotiated or “exchanged” during Phase One of IKE? (5 items)
|
Encryption algorithm, integrity protection algorithm, authentication method, Diffie-Helman group, and cookies
|
|
|
|
[SP800-77 IPSec] What encryption algorithm and mode is being offered?
|
DES-CBC (Digital Encryption Standard in Cipher Block Chaining mode)
|
|
|
|
[SP800-77 IPSec] What hash algorithm is being offered?
|
MD5
|
|
|
|
[SP800-77 IPSec] Is this endpoint suggesting pre-shared key or PKI-based authentication?
|
Pre-shared key
|
|
|
|
[SP800-77 IPSec] What kind of DH technique is being offered?
|
The strongest exponentiation over prime modulus
|
|
|
|
[SP800-77 IPSec] What is true about the responder cookie in this 1st message of the 1st part of IKE Phase 1?
|
It’s zero
|
|
|
|
[SP800-77 IPSec] What is the Next Payload sequence in this IKE Main Mode 3rd message?
|
ISAKMP → Key Exchange → Nonce
|
|
|
|
[SP800-77 IPSec] In IKE Main Mode, during which pair of message exchanges do the two endpoints authenticate one another?
|
Third
|
|
|
|
[SP800-77 IPSec] Which of these correctly summarizes the purpose of each pair of message exchanges of IKE Main Mode?
|
Agreement on algorithms to use – DH Session Key Construction – Authentication
|
|
|
|
[SP800-77 IPSec] Which of these is true?
a. Main mode is faster, but Aggressive mode is more secure. b. Main mode is more secure, but support for it is optional. c. Aggressive mode is faster, but Main mode is more secure. d. Aggressive mode more secure, but support for it is optional. |
Aggressive mode is faster, but Main mode is more secure
|
|
|
|
[SP800-77 IPSec] Which of these best states the purpose of IKE Phase 2?
a. Authenticate the two endpoints. b. Establish an SA for the actual IPSec (data transfer) connection. c. Establish a new session key for use in creating IPSec SA instances. d. Validation of endpoint-provided public keys. |
Establish an SA for the actual IPSec (data transfer) connection.
|
|
|
|
[SP800-77 IPSec] Which of these is true regarding IKE Phase 2?
a. All IPSec SA protocol decisions have been established during IKE Phase 1, so IKE Phase 2 only needs to send a chosen (session) key for each IPSec connection. b. Phase 2’s only purpose is to assign a SPI for each IPSec SA instance. c. Phase 1 negotiates keys & algorithms, Phase 2 handles authentication. d. IPSec keys and algorithms are established for each IPSec SA in this phase. |
IPSec keys and algorithms are established for each IPSec SA in this phase
|
|
|
|
[SP800-77 IPSec] Which of these best expresses the “bottom line” on PFS?
a. Attacker must resort to brute-force to compromise a session key. b. Attacker compromise of one key, does not help in compromising other keys. c. All keys, including session keys, are asymmetric-based. d. Each IPSec SA creates a unique session key from all other IPSec SAs. |
Attacker compromise of one key, does not help in compromising other keys.
|
|
|
|
[SP800-77 IPSec] Which of these best summarizes the difference between the SAD and the SPD?
a. SAD indicates what traffic to protect; SPD indicates how to protect it. b. SAD is list of what to protect; SPD is a list of algorithms that could be used. c. SPD lists all participating IPs; SAD lists all participating ports. d. SPD indicates what traffic to protect; SAD indicates how to protect it. |
SPD indicates what traffic to protect; SAD indicates how to protect it
|
|
|
|
[SP800-77 IPSec] In summary…
a. IKE phase 1 creates an IKE SA; IKE phase 2 creates an IPSec SA. b. IKE phase 1 creates an IPSec SA; IKE phase 2 creates an IKE SA. c. IKE phase 1 negotiates keys and algorithms; IKE phase 2 authenticates. d. IKE phase 1 builds the SAD; IKE phase 2 builds the SPD. |
IKE phase 1 creates an IKE SA; IKE phase 2 creates an IPSec SA
|
|
|
|
[SP800-77 IPSec] What does “bump in the stack” mean?
|
Inserting a third party client between the IP stack and the local network drivers to “build-in” an IPSec client
|
|
|
|
[SP800-77 IPSec] All other things being equal, which would represent a more secure IPSec implementation for the enterprise that supports remote user IPSec VPN tunnels?
|
Split-tunneling not permitted
|
|
|
|
[SP800-77 IPSec] In a nut shell, this sections addresses the defense-in-depth concept; including several specific “defenses” not directly related to IPSec. One of these (bottom of p. 4-11 and top of p. 4-12) mentions “. . . checking its host security control settings, and then deciding if it should be permitted to use the organization’s networks . . . .” This security control was recently (2012) implemented at NPS. What is the term used for this?
|
Network Access Control (NAC)
|
|
|
|
[SP800-77 IPSec] Which statement is true?
a. L2F is a Cisco proprietary protocol that can implement the host-to-host VPN architecture. b. PPTP should not be used to protect communications because of its known weaknesses. c. L2TP is limited to PPP-provided authentication methods. d. Most data link layer VPN protocols use GRE to provide their encryption. |
PPTP should not be used to protect communications because of its known weaknesses
|
|
|
|
[SP800-77 IPSec] Which statement is false?
a. TLS is most commonly used to provide security for HTTP-based applications. b. TLS authentication is typically one-way, authenticating the server to the client. c. All major Web browsers include support for TLS. d. Users wanting to utilize TLS security will likely need to install special client software. |
Users wanting to utilize TLS security will likely need to install special client software
|
|
|
|
[SP800-77 IPSec] Which statement is false?
a. A commonly used application layer VPN protocol is SSH. b. SSH is better classified as a transport—vice application—layer VPN protocol. c. Only shell-based commands can be passed through SSH tunnels. d. In some cases, an app-layer VPN protocol may only protect a portion of the application data. |
Only shell-based commands can be passed through SSH tunnels
|
|
|
|
When validating a CA's signature the certificate should be valid until?
|
Expired
|
|
|
|
What field should be checked for correctness when validating a CA's signature?
|
Key Usage Field
|
|
|
|
What should be checked against a CRL or OCSP for any given certificate?
|
that is has not been revoked
|
|
|
|
What is a CRL?
|
certificate revocation list
|
|
|
|
What is an OCSP?
|
online certificate status protocol
|
|
|
|
What is the key notion of trust in PKI?
|
Protecting the trust/veracity of the binding between identity of the subject and the public key association
|
|
|
|
How does a public key cert issuer protect the binding between the ID of a subject and the public key?
|

|
|
|
|
[Cryptool] What do you think is inside of this PKCS#12 container?
|
private key, corresponding public cert, ca root cert
|
|
|
|
[SP800-77 IPSec] Which VPN architecture provides the most thorough protection in terms of topological coverage of the protective encryption?
a. Gateway-to-Gateway b. Host-to-Gateway c. Host-to-Host |
Host-to-Host
|
|
|
|
[SP800-77 IPSec] Technically- (vice practically-) speaking…
a. we could use transport mode for any of the three VPN architectures. b. we could use tunnel mode for any of the three VPN architectures. c. we must use tunnel mode for gateway-to-gateway, and we must use transport mode any time one endpoint is a host. d. we must use transport mode for host-to-host, and we must use tunnel mode any time one endpoint is a gateway. |
we could use tunnel mode for any of the three VPN architectures
|
|
|
![[SP800-77 IPSec] Which mode combination of IPSec does this “stack” illustrate? Assume # equates to protocol layer in the TCP/IP stack, and assume that gray shading indicates encrypted.
a. AH in transport mode.
b. AH in tunnel mode.
c....](https://images.cram.com/images/upload-flashcards/51/28/82/5512882_m.png)
[SP800-77 IPSec] Which mode combination of IPSec does this “stack” illustrate? Assume # equates to protocol layer in the TCP/IP stack, and assume that gray shading indicates encrypted.
a. AH in transport mode. b. AH in tunnel mode. c. ESP in transport mode. d. ESP in tunnel mode. |
ESP in tunnel mode
|
|
|
|
[SP800-77 IPSec] Several keyed hash algorithms are mentioned. One of them, (AES-XCBC-MAC-96) employs an encryption algorithm (AES) vice a hash algorithm! Hopefully you recall from lecture how this can be accomplished. Briefly explain how.
|
Use sub-set of cipher text as the hash
|
|
|
![[SP800-77 IPSec] What—exactly—is the sequence number for the AH example of Figure 3-4?](https://images.cram.com/images/upload-flashcards/51/29/66/5512966_m.png)
[SP800-77 IPSec] What—exactly—is the sequence number for the AH example of Figure 3-4?
|
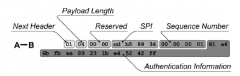
00 00 00 01
|
|
|
|
[SP800-77 IPSec] If ESP is implemented to include integrity protection, where is the integrity-providing MAC carried?
a. In the ESP header. b. In the ESP trailer. c. In the ESP payload. d. Coded into the SPI value. |
In the ESP trailer
|
|
|
|
[SP800-77 IPSec] If you read the descriptions of the Digital Signature and Public Key Encryption based authentication methods; you may (from lecture discussion) notice an error in the way the second is explained. What is the error?
|
It should read “each peer encrypts with the peer’s pubic key…”
|
|
|
|
[SP800-77 IPSec] DH gets heavy usage in network crypto applications. Which of these best explains the use of DH as it pertains to VPNs?
a. A way for 2 remote devices to create a shared secret, without a secure channel to begin with. b. Method employed during Phase I to establish the pre-shared secret for initial authentication. c. DH is employed to slightly alter the IPSec SA key for each packet. d. DH is the core technique employed to authenticate the endpoints prior to IPSec SA creation. |
A way for 2 remote devices to create a shared secret, without a secure channel to begin with
|
|
|
|
[SP800-77 IPSec] In Figure 3-13, you see that the payload is encrypted. Given that we are still looking at IKE negotiation, vice an instance of an IPSec tunnel to protect actual user data transfer; what is the advantage/intent of encrypting this third IKE message exchange pair?
|
the third pair authenticates the endpoints to each other so that it cannot be replayed or misused
|
|
|
|
[SP800-77 IPSec] Which of these is correct?
a. A SAD points to an SA using a SPI. b. The SPI contains all instances of SAs which hold SAD information. c. A SPI points to an SA instance in the SAD. d. A SAD contains all the information needed to define a single IPSec SA. |
A SPI points to an SA instance in the SAD.
|
|
|
|
[SP800-77 IPSec] What combination of information allows an IPSec VPN endpoint to look-up the correct SA?
a. Destination IP, SPI, and ESP-or-AH b. Source IP, Destination IP, and SPI c. SPI, ESP-or-AH, and Tunnel-or-Transport d. SPI, SPD, SAD |
Destination IP, SPI, and ESP-or-AH
|
|
|
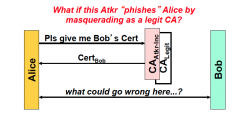
What is the attacker's next move?
|
Impersonate Bob in an attack on Alice
|
|
|
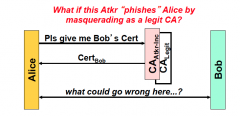
Why SHOULD Alice have detected the fake Cert?
|
Because she does not have attack Inc as a root certificate or the certificate's signature cannot be verified
|
|
|

Is this communication vulnerable to attack by someone impersonating Bob?
|
No
|
|
|
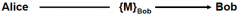
Is this communication vulnerable to attack by someone impersonating Bob?
|
Yes
|
|
|

Is this communication vulnerable to attack by someone impersonating Bob?
|
Yes
|
|
|
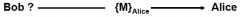
Is this communication vulnerable to attack by someone impersonating Bob?
|
No
|
|
|
|
What if Cert owners have different CAs? What are the two general solutions?
|
Cross certification and CA chaining
|
|
|
|
What is cross certification?
|
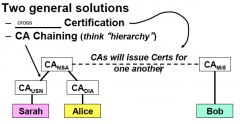
One CA's public key signed with another CA's private key.
|
|
|
|
What is CA Chaining?
|
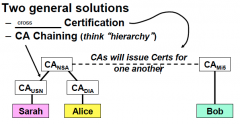
a common heiarchy with branches
|
|
|
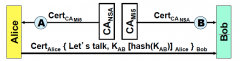
What will Bob use to verify Alice's cert?
|
Cert CA (NSA)
|
|
|
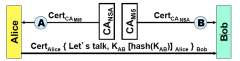
What will Bob use to decrypt the message?
|
Bob's private key
|
|
|
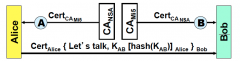
What will Bob find inside the message?
|
Alice's public key
|
|
|
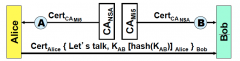
What will Bob use alice's public key for?
|
Decrypt hash (K ab)
|
|
|
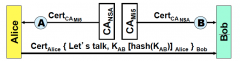
How will Bob verify the K ab?
|
re-hash K ab and compare against the one that was just decrypted
|
|
|
|
What is needed between a certificate user and a certificate owner to trust each other?
|
A common trust anchor
|
|
|
|
[SP800-32 PKI] Assume your organization tailors its v3 X.509 certificates to include blood type in an extension field because this additional information is sometimes useful to have within your organization. Which of these makes the most sense regarding that extension’s criticality flag?
a. Set it, because this information (blood type) is considered critical. b. Set it, as we’d want all certificate processing software to be required to understand this field. c. Don’t set it, as we would not want to hinder the use of our certificates in other environments. d. Don’t set it, since this information is not a mandatory field of the X.509 data structure. |
Don’t set it, as we would not want to hinder the use of our certificates in other environments
|
|
|
|
[SP800-32 PKI] Let’s say that your organization wishes to use PKI in a manner that facilitates a greater degree of authorization, rather than merely identification of a person entity. Let’s say that the attribute used to determine authorization will be that of the person’s security clearance. What are the two ways in which PKI can support this?
|
Include security clearance in subjects’ public key certificate as an extension and Issue each subject an attribute certificate.
|
|
|
|
[SP800-32 PKI] What percentage of bits change for each of your modifications?
|
Always around 50%
|
|
|
|
[SP800-32 PKI] What ultimately got encrypted?
|
The 160 bit hash pre-pended with padding and an algorithm ID
|
|
|
|
[SP800-32 PKI] According to what you are now looking at in the bottom of the Step by Step Signature Generation window, what is the digital signature of this file composed of?
|
The word “Signature:” followed by both the 1024 bit encryption of the answer to Q29, some additional information about what algorithms were used to compute the signature, and a reference to the digital certificate whose private key was used to sign the answer to Q29
|
|
|
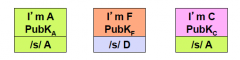
Are there any root certificates here?
|
Yes, A is a root certificate
|
Which one is self-signed?
|
|
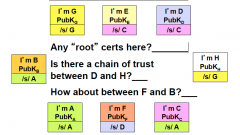
Is there a chain of trust between F and B?
|
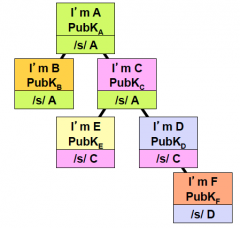
Yes, look at it from a hierarchical view
|
|
|
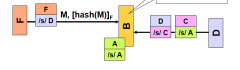
What will B do with certs C and D?
|
cache them
|
|
|
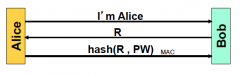
What could an attacker do if R & PW are re-used?
|
replay
|
|
|
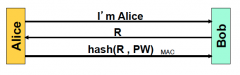
What is this session vulnerable to if done only at the beginning of conversation?
|
hijack
|
|
|
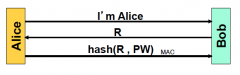
What could an attacker do if he can read the stored PW at Alice or Bob?
|
Impersonate Alice or Bob
|
|
|
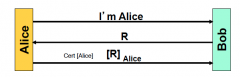
Is this remote connection flawed? If so, what could an attacker do?
|
An attacker could simply reuse R since it is in the clear
|
|
|
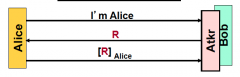
Is this remote connection flawed? If so, what could an attacker do?
|
An attacker could save the key and send it another time to re-use it
|
|
|
|
Most PKI implementations issue users separate key pairs for what?
|
identity, email encryption, and email signing
|
|
|
|
When two parties are authenticating each other who should authenticate first?
|
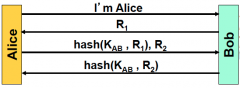
Whoever initiated
|
|
|
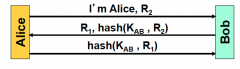
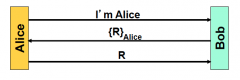
Is this remote connection flawed? If so, what could an attacker do?
|
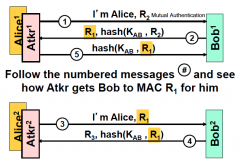
Follow the numbered messages and see how Atkr gets Bob to MAC R1 for him
|
|
|
|
A contributing factor to the reflection attack is that both authenticators are doing the same thing, how can this be fixed?
|
Adding directionality
|
|
|
|
What does it mean to directionalize a remote connection authentication procedure?
|
initiator message must look different than the responder message
|
|
|
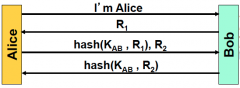
Why is the scheme not susceptible to reflection or brute forcing a symmetric key given R and the MAC?
|

The scheme follows a good auth’n protocol design in that the initiator authenticates first
|
|
|
|
How do you know if you have Perfect Forward Secrecy (PFS)?
|
You have PFS if the attack can break into either or both ends, steal a long term secret, and still not be able to decrypt any previously recorded message
|
|
|
|
What is the most essential part to establishing Perfect Forward Secrecy (PFS)
|
establish a session key that will protect the C I a of the ensuing msg traffic
|
|
|
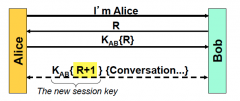
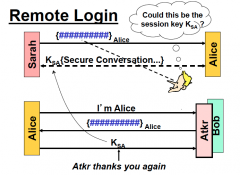
Is PFS achieved? If not, why?
|
If attacker steals KAB from Alice or Bob he can create the session key and decrypt this recorded conversation. So PFS is NOT achieved.
|
|
|
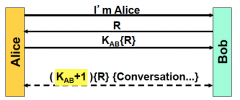
Is PFS achieved? If not, why?
|
No, I just need to get K AB from either Bob or Alice (offline though)
|
|
|

Is PFS achieved with PKI? If not, why?
|
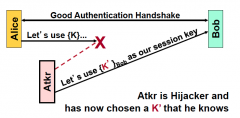
No, the attack can hijack the message because he can choose K' or just break into Bob and steal his private key.
|
|
|
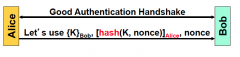
Is PFS achieved with PKI and signing? If not, why?
|
No, you can still get Bob's private keys to decrypt the message
|
|
|

Is PFS achieved with both sides contributing to the key? If not, why?
|
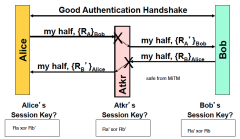
No, the attack can essentially get in the middle of the session and break the chain.
|
|
|
|
(True or False) The Diffie-Hellman protocol allows two remote entities to arrive at a
shared secret... in such a way that an eavesdropper (sniffer) who observes the entire secret-building session between the two entities would be unable to derive the shared secret himself. |
True
|
|
|
|
Does Diffie-Hellman provide PFS?
|
No, because DH facilitates the construction of a secret with someone (who you may not know)
|
|
|
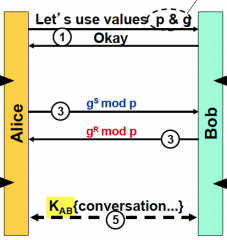
What is the secret part of the exchange?
|
the exponent (S and R)
|
|
|
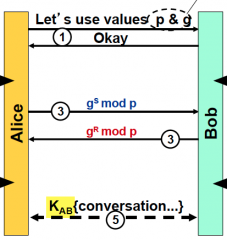
How can you correct Diffie Hellman to add Perfect Forward Secrecy?
|
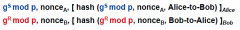
add a HMAC (PW & something else)!
|
|
|
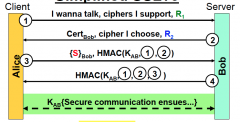
In what step was authentication done and who did it?
|
Step 4, this is where Alice is finally convinced that true Bob has the private certificate that was used in step 2. Alice does NOT authenticate!
|
|
|
|
Does SSLv3 achieve PFS?
|
No
|
|
|
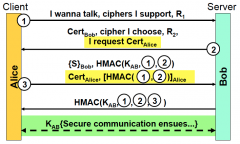
In what step was authentication done and who did it?
|
Alice authenticates by signing in step 3 and Bob authenticates by decrypting in step 4
|
|
|
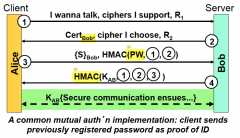
In what step was authentication done and who did it?
|
Alice authenticates in step 3 by using a shared secret and Bob authenticates in step 4 by decrypting
|
|
|
|
What is an assumption made about every rainbow table?
|
password space (length and applicable characters)
|
|
|
|
When a match is found in a rainbow table, do we definitely have PWt?
|
No, you have a password that hashes to the same value as the PWt
|
|
|

If you had the option of a very long chain or a large number of chains with a single hash ... which is better? How does it relate to space and time?
|
A shorter chain St (#2) is better because time is more valuable to an attacker
|
|
|
|
Assuming that all the PWs in all the chains are distinct, how much of the PW space is effectively represented by these tables?
|

The table cover 218 trillion possibilities with 220 trillion table spots (and duplicate entries)
|
|
|
|
What is Lamport's Hash Algorithm for authentication?
|
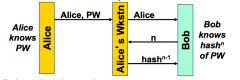
Bob authenticates by hashing hash n-1 and comparing it to the previously hashed n. Then he replaces hash n with hash n-1 and decrements n for the next time Alice logs in.
|
|
|
|
In Lamport's Hash Algorithm what happens when n reaches 1?
|
Alice will need a different PW for each server unless a salt is added.
|
|
|
|
In Lamport's Hash Algorithm, how can we ensure the same salt will not be generated for use at >1 server?
|
Rather than salt being a random value, we can add the IP address of the server we are communicating to with a random salt value.
|
|
|
|
In Lamport's Hash Algorithm, under what conditions can an attacker impersonate Alice to Bob?
|
so long as n stored at Bob is higher than the hash intercepted by the attacker
|
|

