![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
28 Cards in this Set
- Front
- Back
|
Which set of configurations will result in all ports on both switches successfully bundling into an EtherChannel? |
switch1channel-group 1 mode desirableswitch2channel-group 1 mode auto |
|
|
The table below lists if an EtherChannel will be formed or not for LACP: |
LACP Active Passive Active Yes Yes PassiveYesNo |
|
|
The table below lists if an EtherChannel will be formed or not for PAgP: |
PAgP Desirable Auto Desirable Yes Yes Auto Yes No |
|
|
After an EtherChannel is configured between two Cisco switches, interface port channel 1 is in the down/down state. Switch A is configured with “channel-group 1 mode active”, while Switch B is configured with “channel-group 1 mode desirable”. Why is the EtherChannel bundle not working? |
The switches are using mismatched EtherChannel negotiation modes. |
|
|
An EtherChannel bundle has been established between a Cisco switch and a corporate web server. The network administrator noticed that only one of the EtherChannel links is being utilized to reach the web server. What should be done on the Cisco switch to allow for better EtherChannel utilization to the corporate web server? |
Adjust the EtherChannel load-balancing method based on source IP addresses. |
|
|
An access switch has been configured with an EtherChannel port. After configuring SPAN to monitor this port, the network administrator notices that not all traffic is being replicated to the management server. What is a cause for this issue? |
The port channel can be used as a SPAN source, but not a destination. |
|
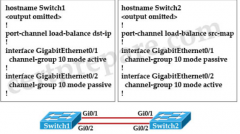
What is the result of the configuration? |
The EtherChannels would form and function properly even though the load-balancing and EtherChannel modes do not match |
|
|
A network engineer tries to configure storm control on an EtherChannel bundle. What is the result of the configuration? |
The settings will be applied to the EtherChannel bundle and all associated physical interfaces. |
|
|
A network engineer must set the load balance method on an existing port channel. Which action must be done to apply a new load balancing method? |
Configure the new load balancing method using port-channel load-balance. |
|
|
A network engineer configured a fault-tolerance link on Gigabit Ethernet links G0/1, G0/2, G0/3, and G0/4 between two switches using Ethernet port-channel. Which action allows interface G0/1 to always actively forward traffic in the port-channel? |
Configure LACP port-priority on G0/1 to 1. |
|
|
Which statement about the use of PAgP link aggregation on a Cisco switch that is running Cisco IOS Software is true? |
PAgP modes are off, auto, desirable, and on. Only the combinations auto-desirable, desirable- desirable, and on-on allow the formation of a channel. |
|
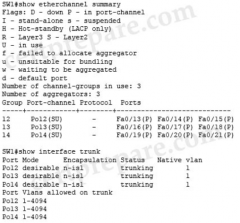
Which EtherChannel negotiation protocol is configured on the interface f0/13 – f0/15? |
Port Aggregation Protocol |
|
|
Which portion of AAA looks at what a user has access to? |
authorization |
|
|
AAA security provides the following services: |
Authentication Authorization Accounting |
|
|
Authentication |
Identifies users, including login and password dialog, challenge and response, messaging support, and, depending on the security protocol that you select, encryption.Authentication is the process of verifying the identity of the person or device accessing the Cisco NX-OS device, which is based on the user ID and password combination provided by the entity trying to access the Cisco NX-OS device. Cisco NX-OS devices allow you to perform local authentication (using the local lookup database) or remote authentication (using one or more RADIUS or TACACS+ servers). |
|
|
Authorization |
Authorization specifies which resources the users are allowed to access. Provides access control.AAA authorization is the process of assembling a set of attributes that describe what the user is authorized to perform. Authorization in the Cisco NX-OS software is provided by attributes that are downloaded from AAA servers. Remote security servers, such as RADIUS and TACACS+, authorize users for specific rights by associating attribute-value (AV) pairs, which define those rights with the appropriate user. |
|
|
Accounting |
Provides the method for collecting information, logging the information locally, and sending the information to the AAA server for billing, auditing, and reporting. |
|
|
Which command creates a login authentication method named “login” that will primarily use RADIUS and fail over to the local user database? |
(config)# aaa authentication login login radius local |
|
|
Which command globally enables AAA on a device? |
aaa new-model |
|
|
Which AAA Authorization type includes PPP, SLIP, and ARAP connections? |
network |
|
|
Which authentication service is needed to configure 802.1x? |
RADIUS with EAP Extension |
|
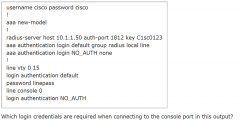
Which login credentials are required when connecting to the console port in this output? |
none required The console port is authenticated with NO_AUTH list. But this list does not contain any authentication method (it uses “none”) so no authentication is required when connecting to the console port. |
|

When a network administrator is attempting an SSH connection to the device, in which order does the device check the login credentials? |
RADIUS server, local username, line password |
|
|
A network engineer configures port security and 802.1x on the same interface. Which option describes what this configuration allows? |
It allows port security to secure the MAC address that 802.1x authenticates. |
|
|
aaa auth explained: aaa authentication login "name of list" group radius local |
In the “aaa authentication login login radius local” command, the first “login” is a keyword which authenticates users who want exec access into the access server (tty, vty, console and aux). The second “login” is a list name. “radius local” part indicates the RADIUS authentication should be used first. If the RADIUS server does not reply then use the local database to authenticate. |
|
|
Method lists explained |
Method lists are specific to the authorization type requested:+ Auth-proxy – Applies specific security policies on a per-user basis. For detailed information on the authentication proxy feature, refer to the chapter “Configuring Authentication Proxy” in the “Traffic Filtering and Firewalls” part of this book.+ Commands – Applies to the EXEC mode commands a user issues. Command authorization attempts authorization for all EXEC mode commands, including global configuration commands, associated with a specific privilege level.+ EXEC – Applies to the attributes associated with a user EXEC terminal session.+ Network – Applies to network connections. This can include a PPP, SLIP, or ARAP connection.+ Reverse Access – Applies to reverse Telnet sessions.When you create a named method list, you are defining a particular list of authorization methods for the indicated authorization type.Once defined, method lists must be applied to specific lines or interfaces before any of the defined methods will be performed. The only exception is the default method list (which is named “default”). If the aaa authorization command for a particular authorization type is issued without a named method list specified, the default method list is automatically applied to all interfaces or lines except those that have a named method list explicitly defined. (A defined method list overrides the default method list.) If no default method list is defined, local authorization takes place by default. |
|
|
port security explained |
You can configure port security and 802.1X on the same interfaces. Port security secures the MAC addresses that 802.1X authenticates. 802.1X processes packets before port security processes them, so when you enable both on an interface, 802.1X is already preventing inbound traffic on the interface from unknown MAC addresses.When you enable 802.1X and port security on the same interface, port security continues to learn MAC addresses by the sticky or dynamic method, as configured. Additionally, depending on whether you enable 802.1X in single-host mode or multiple-host mode, one of the following occurs:+ Single host mode—Port security learns the MAC address of the authenticated host.+ Multiple host mode—Port security drops any MAC addresses learned for this interface by the dynamic method and learns the MAC address of the first host authenticated by 802.1X.If a MAC address that 802.1X passes to port security would violate the applicable maximum number of secure MAC addresses, the device sends an authentication failure message to the host.The device treats MAC addresses authenticated by 802.1X as though they were learned by the dynamic method, even if port security previously learned the address by the sticky or static methods. If you attempt to delete a secure MAC address that has been authenticated by 802.1X, the address remains secure.If the MAC address of an authenticated host is secured by the sticky or static method, the device treats the address as if it were learned by the dynamic method, and you cannot delete the MAC address manually.Port security integrates with 802.1X to reauthenticate hosts when the authenticated and secure MAC address of the host reaches its port security age limit. |
|
|
configure AAA |
ASW1(config)#aaa new-model ASW1(config)#radius-server host 172.120.39.46 key rad123 ASW1(config)#aaa authentication dot1x default group radius ASW1(config)#dot1x system-auth-control ASW1(config)#interface fastEthernet 0/1 ASW1(config-if)#switchport mode access ASW1(config-if)#dot1x port-control auto DSW1(config)#ip access-list standard 10 DSW1(config-std-nacl)#permit 172.120.40.0 0.0.0.255 DSW1(config-std-nacl)#exit DSW1(config)#vlan access-map MYACCMAP 10 DSW1(config-access-map)#match ip address 10 DSW1(config-access-map)#action forward DSW1(config-access-map)#exit DSW1(config)#vlan filter MYACCMAP vlan-list 20 |

