![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
11 Cards in this Set
- Front
- Back
- 3rd side (hint)
|
Confidentiality |
Preventing unauthorised disclosure of information. |
|
|
|
Integrity |
Preventing unauthorised modification or destruction of information |
|
|
|
Availability |
Ensuring resources are accessible when required by an authorised user |
|
|
|
Entity authentication |
The process of verifying a claimed identify |
|
|
|
Data origin authentication |
Verify the source (and integrity) of a message |
|
|
|
Non-repudiation |
Create evidence that an action has occured, so that user cannot falsely deny the actuon later. |
|
|
|
Asset |
Anything that supports information-related activities. |
|
|
|
Threats |
All the things that have a potential to cause harm by compromising the security goals |
|
|
|
Vulnerabilities |
Characteristic or weaknesses in a system that could be used to cause harm if acted on by a threat |
|
|
|
Security incidents |
When threats and vulnerabilities coincide, information assets can be harmed. |
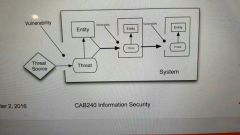
|
|
|
Security measures or controls |
Preventive: aim to prevent attempts to exploit vulnerabilities. Detective: monitor to receive warnings of attempts to exploit vulnerabilities Corrective: aim to correct errors or irregularities that have been detected. |
|

