![]()
![]()
![]()
Use LEFT and RIGHT arrow keys to navigate between flashcards;
Use UP and DOWN arrow keys to flip the card;
H to show hint;
A reads text to speech;
139 Cards in this Set
- Front
- Back
|
What is the structured approach called for developing software and information systems?
A) Software design B) Prototyping C) Systems development life cycle D) Systems methodology |
Systems development life cycle
|
|
|
Who is the person who typically manages the software development project?
A) Software engineer B) Project manager C) IT manager D) Technology director |
Project manager
|
|
|
In which phase of the software design and development project would you try to understand the proposed project?
A) Planning phase B) Initial phase C) Requirements phase D) Analysis phase |
Analysis phase
|
|
|
In which phase of the software design and development project would you build a blueprint of the proposed system?
A) Analysis phase B) Design phase C) Requirements phase D) Development phase |
Design phase
|
|
|
In which phase of the software design and development project would you build the proposed system?
A) Design phase B) Requirements phase C) Development phase D) Implementation phase |
Development phase
|
|
|
In which phase of the software design and development project would you take the newly built system and place in operations?
A) Requirements phase B) Development phase C) Implementation phase D) Execution phase |
Implementation phase
|
|
|
In which phase of the software design and development project would you fix errors in the new built and operational system?
A) Development phase B) Maintenance phase C) Implementation phase D) Execution phase |
Maintenance phase
|
|
|
What term refers to the fast-paced building or construction of a software prototype?
A) Rapid application development (RAD) B) Rapid agility programming (RAP) C) Speed programming D) Express development (ED) |
Rapid application development (RAD)
|
|
|
What type of software design and development methodology does Microsoft Corporation employ?
A) Rapid application development B) Extreme programming C) Speed programming D) Express development |
Extreme programming
|
|
|
What term refers to the end user developing software without the assistance of IT?
A) User development B) In-sourcing C) Self service D) Selfsourcing |
Selfsourcing
|
|
|
What type of information should you avoid including on your Web site?
A) Links to sites of interest B) Private personal information C) Work and academic experience D) Graphical |
Private personal information
|
|
|
Which of the following web elements should you know about before building your web site?
A) The web audience B) The operating environment of your ISP C) The operating system of your visitor D) Each consideration should determine your web design choices |
The web audience
|
|
|
What is the language of the Web?
A) Basic B) C++ C) MS Visual Basic D) HTML |
HTML
|
|
|
What does an HTML tag do?
A) It specifies formatting and layout instructions for your web page B) It hides programming instructions from view C) It determines the organizational structure of your Web site D) It connects your web site to an operating environment |
It specifies formatting and layout instructions for your web page
|
|
|
A Web document is broken into sections. What are the tags called that create these sections?
A) Structure tags B) HTML tags C) Heading tags D) Body tags |
Structure tags
|
|
|
What should be the first and last pair of tags in your Web document?
A) <html></html> B) <start><end> C) <head><body> D) <title></title> |
<html></html>
|
|
|
There are two main sections in every HTML document. What are they?
A) Introduction and instructions B) Head and body C) System and Wed content D) Code and content |
Head and body
|
|
|
For every Web document, you can add words that appear in the upper left bar area of your browser. What set of tags allows you to provide this information?
A) <head></head> B) <head><head> C) <label><label> D) <title></title> |
<title></title>
|
|
|
If you wanted to create text that was a different color or font than other text in your Web page, what type of tag would you use?
A) Layout B) Basic formatting C) Design D) Outline |
Basic formatting
|
|
|
What tag would you use if you wanted a blank line in your Web document?
A) <line> B) <br> C) <li> D) <cr> |
<br>
|
|
|
Three primary choices as to who will build your system. _____, selfsourcing (aka end-user development), and outsourcing.
|
Insourcing
|
|
|
Three primary choices as to who will build your system. Insourcing, _____(aka end-user development), and outsourcing.
|
selfsourcing
|
|
|
Three primary choices as to who will build your system. Insourcing, selfsourcing (aka end-user development), and _____.
|
outsourcing
|
|
|
Involves in-house IT specialists within your organization to develop the system.
|
Insourcing
|
|
|
The development and support of IT systems by end users ( knowledge workers) with little or no help from IT specialists.
|
Selfsourcing (aka end-user development)
|
|
|
The delegation of specific work to a third party for a special length of time, at a specified cost, and at a specified level of service.
|
Outsourcing
|
|
|
A structured step-by-step approach for developing information systems. Includes seven key phases.
|
Systems Development Life Cycle (SDLC)
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Define the system to be developed?
|
Planning
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Set the project scope?
|
Planning
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Develop the project plan including tasks, resources, and timeframes?
|
Planning
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Gather the business requirements for the system?
|
Analysis
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Design the technical architecture required to support the system?
|
Design
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Design system models?
|
Design
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Build the technical architecture?
|
Development
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Build the database and programs?
|
Development
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Write the test conditions?
|
Testing
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Preform the testing of the system?
|
Testing
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Write detailed user documentation?
|
Implementation
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Provide training for the system users?
|
Implementation
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Build a help desk to support the system users?
|
Maintenance
|
|
|
In the Systems Development Life Cycle (SDLC), what phase is the activity: Provide an environment to support system changes?
|
Maintenance
|
|
|
During the _____ phase of the SLDC you crate a solid plan for developing your information system.
|
planning
|
|
|
The _____ phase of the SLDC involves end users and IT specialists working together to gather, understand, and document the business requirements for the proposed system.
|
analysis
|
|
|
The primary goal of the _____ phase of the SLDC is to build a technical blueprint of how the proposed system will work.
|
design
|
|
|
The _____ phase of the SLDC verifies that the system works and meets all the business requirements defined in the analysis phase.
|
testing
|
|
|
During the _____ phase of the SLDC you distribute the system to all the users and they begin using the system to perform their everyday jobs.
|
implementation
|
|
|
During the ______ phase of the SLDC, you monitor and support the new system to ensure it continues to meet business goals.
|
maintenance
|
|
|
The advantages of selfsourcing are:
1. Improves _____ determination 2. Increases end user participation and sense of ownership 3. Increases speed of systems development 4. Reduces the invisible backlog |
requirement
|
|
|
The advantages of selfsourcing are:
1. Improves requirement determination 2. Increases end user _____ and sense of _____ 3. Increases speed of systems development 4. Reduces the invisible backlog |
participation / ownership
|
|
|
The advantages of selfsourcing are:
1. Improves requirement determination 2. Increases end user participation and sense of ownership 3. Increases _____ of systems development 4. Reduces the invisible backlog |
speed
|
|
|
The advantages of selfsourcing are:
1. Improves requirement determination 2. Increases end user participation and sense of ownership 3. Increases speed of systems development 4. Reduces the _____ _____ |
invisible backlog
|
|
|
_____ is the process of building a model that demonstrates the features of a proposed product, service, or system
|
Prototyping
|
|
|
The five main reasons behind rapid growth:
1. _____ 2. The Internet 3. Growing economy and low unemployment rate 4. Technology 5. Deregulation |
Globalization
|
|
|
The five main reasons behind rapid growth:
1. Globalization 2. The _____ 3. Growing economy and low unemployment rate 4. Technology 5. Deregulation |
Internet
|
|
|
The five main reasons behind rapid growth:
1. Globalization 2. The Internet 3. Growing _____ and low _____ rate 4. Technology 5. Deregulation |
economy / unemployment
|
|
|
The five main reasons behind rapid growth:
1. Globalization 2. The Internet 3. Growing economy and low unemployment rate 4. _____ 5. Deregulation |
Technology
|
|
|
The five main reasons behind rapid growth:
1. Globalization 2. The Internet 3. Growing economy and low unemployment rate 4. Technology 5. _____ |
Deregulation
|
|
|
The three geopolitical outsourcing options:
1. _____ outsourcing 2. Nearshore outsourcing 3. Offshore outsourcing |
Onshore
|
|
|
The three geopolitical outsourcing options:
1. Onshore outsourcing 2. _____ outsourcing 3. Offshore outsourcing |
Nearshore
|
|
|
The three geopolitical outsourcing options:
1. Onshore outsourcing 2. Nearshore outsourcing 3. _____ outsourcing |
Offshore
|
|
|
A Service-Oriented Architecture (SOA) Philosophy is made up of the following focus groups:
______ End Users Software Development Information Needs Hardware Requirements |
Customers
|
|
|
A Service-Oriented Architecture (SOA) Philosophy is made up of the following focus groups:
Customers ___ _____ Software Development Information Needs Hardware Requirements |
End Users
|
|
|
A Service-Oriented Architecture (SOA) Philosophy is made up of the following focus groups:
Customers End Users _____ _____ Information Needs Hardware Requirements |
Software Development
|
|
|
A Service-Oriented Architecture (SOA) Philosophy is made up of the following focus groups:
Customers End Users Software Development _____ _____ Hardware Requirements |
Information Needs
|
|
|
A Service-Oriented Architecture (SOA) Philosophy is made up of the following focus groups:
Customers End Users Software Development Information Needs _____ _____ |
Hardware Requirements
|
|
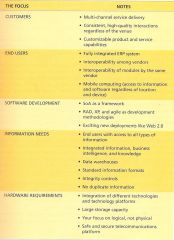
|
Service-Oriented Architecture (SOA)
|
|
|
Involves distributing the information and processing power of IT systems via a network.( This is the the first true network infrastructure)
|
Distributed infrastructure
|
|
|
What are the four tiers of an n-Tier infrastructure model?
__________ 2-tier Application Tier 3-tier Data Teir n-tier Logic Teir |
1-tier Presentation Tier
|
|
|
What are the four tiers of an n-Tier infrastructure model?
1-tier Presentation Tier ___________ 3-tier Data Teir n-tier Logic Teir |
2-tier Application Tier
|
|
|
What are the four tiers of an n-Tier infrastructure model?
1-tier Presentation Tier 2-tier Application Tier __________ n-tier Logic Teir |
3-tier Data Teir
|
|
|
What are the four tiers of an n-Tier infrastructure model?
1-tier Presentation Tier 2-tier Application Tier 3-tier Data Teir __________ |
n-tier Logic Teir
|
|
|
A _____ infrastructure is the most basic setup because it involves a single tier on a single machine.Think of an application that runs on your PC-everything you need to run the application is wrapped up together. An example is a basic word processor or a desktop file utility program.
|
1-tier
|
|
|
A _____ infrastructure is the basic client/server relationship. In essence, the client handles the display, the server handles the request, and this tier is contained on one or both of the tiers.
|
2-tier
|
|
|
A _____ infrastructure is the most common approach used for Web applications today. A typical example if this model is the Web browser that acts as the client, an application server that handles the business logic, and a seperate tier (such as a DBMS) that handles database functions.
|
3-tier
|
|
|
An _____ infrastructure balances the work of the network over several different servers. The letter stands for any number of tiers. Traditionally it starts with a basic 3-tier model and expands on it to allow for greater performance, scalability, and a host of other benefits.
|
n-tier
|
|
|
A delivery model for software in which you pay for software on a pay-per-use basis instead of buying the software outright.
|
Software-As-A-Service (Saas)
|
|
|
A delivery model for software identical to SaaS with additional features of (1) the ability to customize data entry forms, screens, reports, and the like and (2) access to software development tools to alter the way in which the software works by adding new modules (services) and/or making modifications to existing modules.
|
Platform-as-a-Service (PaaS)
|
|
|
The cloud computing model in which you acquire all your technology needs in the cloud.
|
Infrastructure-as-a-Service (IAAS)
|
|
|
The process of continuously measuring system results and comparing those results.
|
Benchmarking
|
|
|
Baseline values a system seeks to attain.
|
Benchmarks
|
|
|
To justify costs of technology, you need to be able to measure the success of technology. With these metrics in hand you can make a cost/benefit judgement about technology. ______ can lead to identifying steps and procedures to improve system performance.
|
Benchmarking
|
|
|
A _____ metric is a measure of the success of your Web and e-business initiatives.
|
Web-centric
|
|
|
Common Web-centric metrics include:
_____ Visitors Total hits Page exposures Conversion rate Click-through cost-per-thousand(CPM) Abandoned registrations Abandoned shopping carts |
Unique
|
|
|
Common Web-centric metrics include:
Unique Visitors Total _____ Page exposures Conversion rate Click-through cost-per-thousand(CPM) Abandoned registrations Abandoned shopping carts |
hits
|
|
|
Common Web-centric metrics include:
Unique Visitors Total hits _____ exposures Conversion rate Click-through cost-per-thousand(CPM) Abandoned registrations Abandoned shopping carts |
Page
|
|
|
Common Web-centric metrics include:
Unique Visitors Total hits Page exposures _____ rate Click-through cost-per-thousand(CPM) Abandoned registrations Abandoned shopping carts |
Conversion
|
|
|
Common Web-centric metrics include:
Unique Visitors Total hits Page exposures Conversion rate _____-through cost-per-thousand(CPM) Abandoned registrations Abandoned shopping carts |
Click
|
|
|
Common Web-centric metrics include:
Unique Visitors Total hits Page exposures Conversion rate Click-through cost-per-_____(CPM) Abandoned registrations Abandoned shopping carts |
thousand
|
|
|
Common Web-centric metrics include:
Unique Visitors Total hits Page exposures Conversion rate Click-through cost-per-thousand(CPM) Abandoned _____ Abandoned shopping carts |
registrations
|
|
|
Common Web-centric metrics include:
Unique Visitors Total hits Page exposures Conversion rate Click-through cost-per-thousand(CPM) Abandoned registrations Abandoned _____ _____ |
shopping carts
|
|
|
Measure the success of call center efforts.
|
Call center metrics
|
|
|
Typical call center metrics include:
_____ rate Average speed to answer (ASA) Time service factor (TSF) First call resolution (FCR) |
Abandon
|
|
|
Typical call center metrics include:
Abandon rate Average _____ to _____ (ASA) Time service factor (TSF) First call resolution (FCR) |
speed to answer
|
|
|
Typical call center metrics include:
Abandon rate Average speed to answer (ASA) _____ _____ factor (TSF) First call resolution (FCR) |
Time service
|
|
|
Typical call center metrics include:
Abandon rate Average speed to answer (ASA) Time service factor (TSF) _____ ____ resolution (FCR) |
First call
|
|
|
The __________ methodology looks very similar to the systems development life cycle. It starts with the oraganization's strategic plan and moves through various phases including analysis ,design, implementation, testing, and maintenance.
|
Business Continuity Planning (BCP)
|
|
|
Principles and standards that guide our behavior toward other people.
|
Ethics
|
|
|
_____ people have integrity.
|
Ethical
|
|
|
Intangible creative work that is embodied in physical form.
|
Intellectual Property
|
|
|
The legal protection afforded an expression of an idea.
|
Copyright
|
|
|
A program that when installed on your computer, records every keystroke and mouse click.
|
Key logger aka Key trapper
|
|
|
The forging of someones identity for the purpose of fraud.
|
Identity theft
|
|
|
A technique to gain personal information for the purpose of identity theft, usually by means of fraudulent e-mail.
|
Phishing (aka carding or brand spoofing)
|
|
|
Phishing that is targeted to a specific individual.
|
Spear phishing
|
|
|
The use of phishing targeted at senior business executives, government leaders, and other types of high-profile individuals.
|
Whaling
|
|
|
The rerouting of your request for a legitimate Web site.
|
Pharming
|
|
|
A small file that contains information about you and your Web activities, which a Web site you visit places on your computer.
|
Cookies
|
|
|
Software to generate ads that installs itself on your computer when you download some other program.
|
Adware
|
|
|
Software you do not want hidden inside software you do want.
|
Trojan Horse
|
|
|
Malicious software that collects information about you and your computer and reports it to someone without your permission.
|
Spyware (aka sneakware or stealthware)
|
|
|
Floods a server or network with so many requests for service that is slows down or crashes.
|
Denial of Service Attack (DOS)
|
|
|
A delivery model for personal productivity software such as Microsoft Office in which you pay for personal productivity software on a pay-per-use basis instead of buying the software outright.
|
Personal Software-as-a-Service (Personal SaaS)
|
|
|
Allows you to send voice communications over the Internet and avoid the toll charges that you would normally recieve from your long distance carrier.
|
Voice over Internet Protocol (VoIP)
|
|
|
Not only captures spoken words but also distinguishes word groupings to form a sentence.
|
Automatic Speech Recognition (ASR)
|
|
|
The three steps of Automatic Speech Recognition are:
1. Feature Analysis 2. Pattern Classification 3. Language _____ |
Processing
|
|
|
The three steps of Automatic Speech Recognition are:
1. Feature _____ 2. Pattern Classification 3. Language Processing |
Analysis
|
|
|
The three steps of Automatic Speech Recognition are:
1. Feature Analysis 2. Pattern _____ 3. Language Processing |
Classification
|
|
|
The system captures your words as you speak into a microphone, eliminates any background noise, and converts the digital signals of your speech into phonemes (syllables)
|
Feature Analysis
|
|
|
The system matches your spoken phonemes to a phoneme sequence stored in an acoustic model database.
|
Pattern Classification
|
|
|
The system attempts to make sense of what you're saying by comparing the word phonemes generated in step 2 with a language model database.
|
Language Processing
|
|
|
A three dimensional computer simulation in which you actively and physically participate.
|
Virtual Reality
|
|
|
An input device that captures and records the shape and movement of your hand and fingers and the strength of your hand and finger movements.
|
Glove
|
|
|
A combined input and output device that (1) captures and records the movement of your head and (2) contains a screen that covers your entire field of vision and displays various views of an environment based on your movements.
|
Headset (head-mounted display)
|
|
|
An input device that captures and records the movement of your feet as you walk or turn in different directions.
|
Walker
|
|
|
Technology to add the sense of touch to an environment that previously only had visual and textual elements.
|
Haptic Interface
|
|
|
Use of physiological characteristics-such as your fingerprint, the blood vessels in the iris of your eye, the sound of your voice, or perhaps even your breath-to provide identification.
|
Biometrics
|
|
|
Custom shoes, Custom wedding gowns, and custom bathrobes are all examples of the use of _____ technology.
|
Biometric
|
|
|
A technology chip that can perform a variety of physiological functions when inserted into the human body.
|
Biochip
|
|
|
A technology-enabled microchip implanted into the human body that stores important information about you (such as your identification and medical history) and that may be GPS-enabled to offer a method of tracking.
|
Implant chip
|
|
|
Software that provides identification by evaluating facial characteristics.
|
Facial recognition software
|
|
|
A standard for transmitting information in the form of short-range radio waves over distances of up to 30 feet.
|
Bluetooth
|
|
|
A standard for transmitting information in the form of radio waves over distances up to about several miles.
|
WiFi (Wireless Fidelity)
|
|
|
A wireless transmission technology developed primarily for mobile phones to support mobile commerce (m-commerce) and other phone activities.
|
Near Field Communication (NFC)
|
|
|
Examples of RFID in use today include:
-_____-_____ car keys -Library book tracking -Livestock tracking -Supply chain -Passports |
Anti-theft
|
|
|
Examples of RFID in use today include:
-Anti-theft car keys -Library book _____ -Livestock tracking -Supply chain -Passports |
tracking
|
|
|
Examples of RFID in use today include:
-Anti-theft car keys -Library book tracking -______tracking -Supply chain -Passports |
Livestock
|
|
|
Examples of RFID in use today include:
-Anti-theft car keys -Library book tracking -Livestock tracking -______ chain -Passports |
Supply
|
|
|
Examples of RFID in use today include:
-Anti-theft car keys -Library book tracking -Livestock tracking -Supply chain -_____ |
Passports
|
|
|
Microchip in a tag or label to store information, and information is transmitted from, or written to, the tag or label when the microchip is exposed to the correct frequency of radio waves.
|
RFID (radio frequency identification)
|

